Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 15
7
Attack type
Description
Smurf
A Smurf attacker sends large quantities of ICMP echo requests to the broadcast address of
the target network. As a result, all hosts on the target network will reply to the requests,
causing the network congested and hosts on the target network unable to provide services.
Source route
A source route attack exploits the source route option in the IP header to probe the topology
of a network.
Route record
A route record attack exploits the route record option in the IP header to probe the topology
of a network.
Large ICMP
For some hosts and devices, large ICMP packets will cause memory allocation error and
crash down the protocol stack. A large ICMP attacker sends large ICMP packets to a target
to make it crash down.
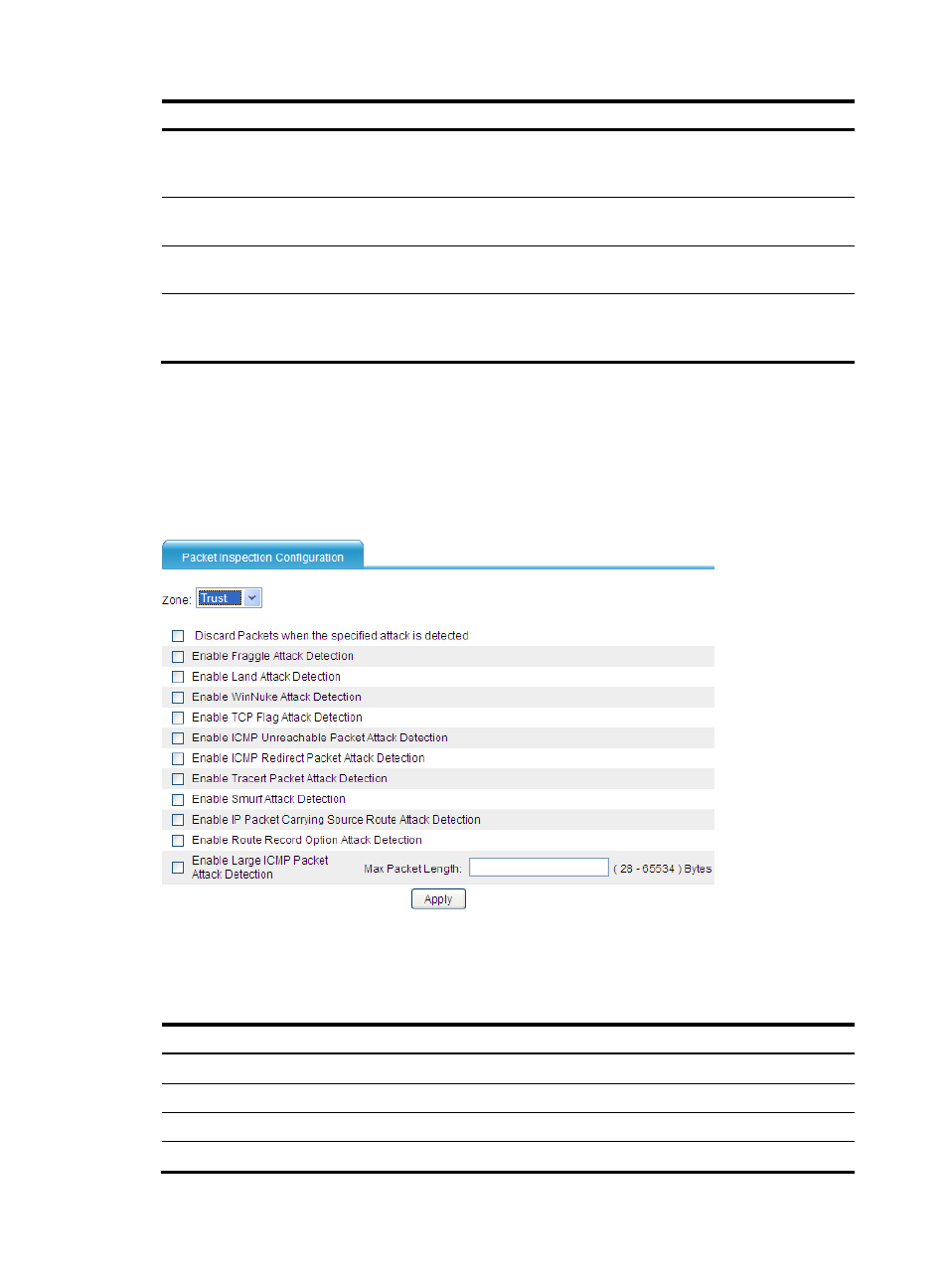
Configuration procedure
1.
From the navigation tree, select Intrusion Detection > Packet Inspection to enter the packet
inspection page.
Figure 8 Configuration page
2.
Configure packet inspection as described in
3.
Click Apply.
Table 4 Configuration items
Item
Description
Zone
Select a zone to detect attacks from the zone.
Discard Packets when the specified attack is detected Select this option to discard detected attack packets.
Enable Fraggle Attack Detection
Enable or disable detection of Fraggle attacks.
Enable Land Attack Detection
Enable or disable detection of Land attacks.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
