Echelon OpenLDV User Manual
Page 109
OpenLDV Programmer’s Guide
101
of the downlink lookup key. Chapter 7, LNS Programming with xDriver, on page
137, provides programming samples that illustrate this behavior.
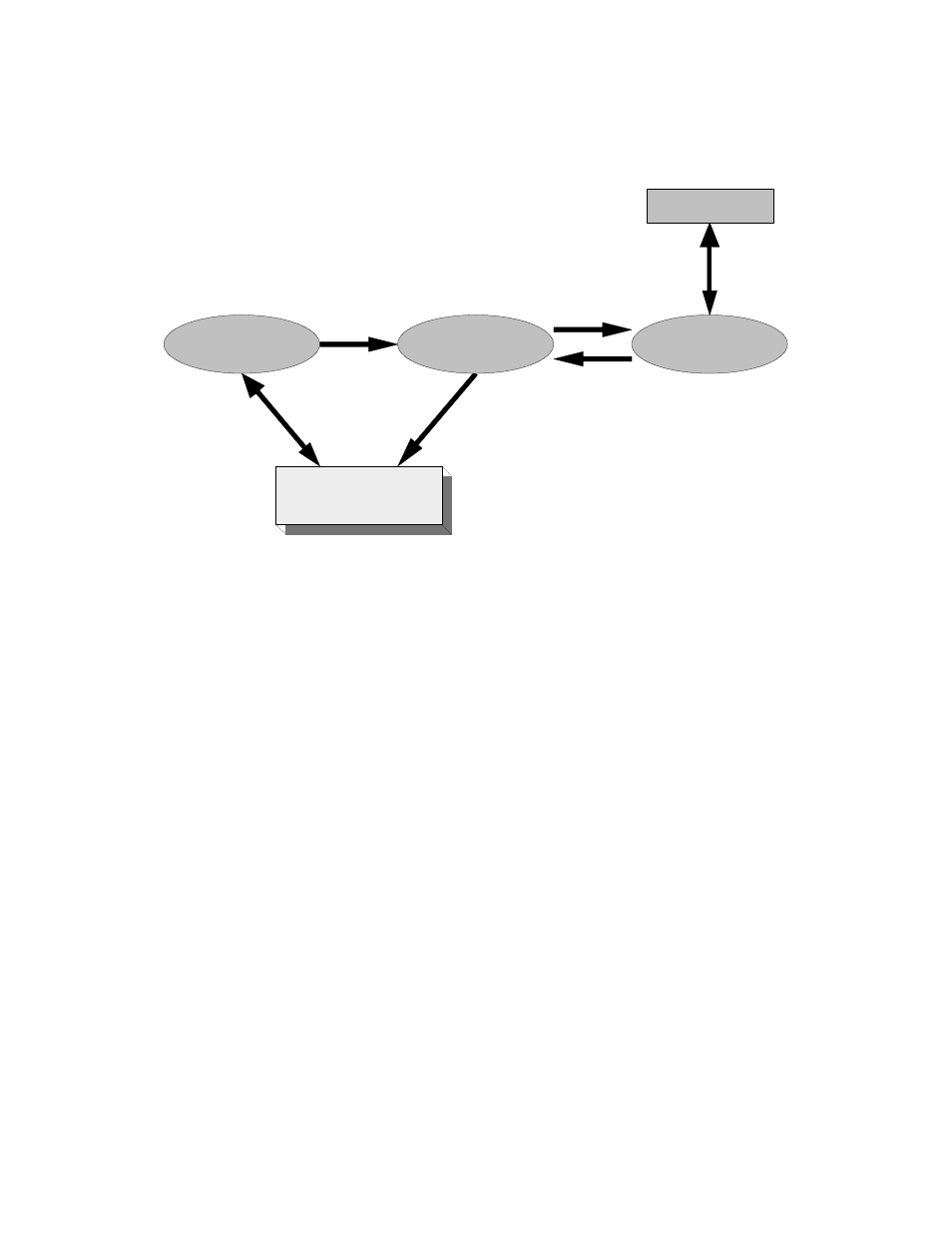
Figure 14 shows the application flow for a downlink session.
User Application
xDriver Manager
Database
Lookup Extension
1
6
2
4
3
5
x.Profile.RNI
Figure 14. Downlink Session
The application flow for a downlink session includes the following steps (see
1. When the OpenLDV application initiates the connection, the xDriver
manager initializes an SCO for the session, and adds the downlink lookup
key (derived from the network interface name of the RNI) into the SCO.
2. The SCO is then passed to the lookup extension component.
3. The lookup extension component extracts the downlink lookup key from
the SCO, and uses it to access the database record for the specified RNI.
The lookup extension component then retrieves additional information
from the database (such as authentication flag, authentication keys, and
IP address and port number of the RNI) to fill in the SCO with the
information required to establish the connection.
For more information about the SCO and the information it stores, see
Session Control Object on 108. For sample programs that initiate
downlink xDriver sessions, see Chapter 7, LNS Programming with
4. The connection is established and the authentication key is used to
validate the connection, if authentication is enabled.
5. If the authentication is successful, packets are exchanged in both
directions. For more information about authentication, see
Authentication Key Handling on page 111.
6. The OpenLDV application performs any required network operations.
