Enabling protection – HP Storage Mirroring V5 Software User Manual
Page 44
34
Protecting an Exchange Cluster with a Like-Named Cluster
8.
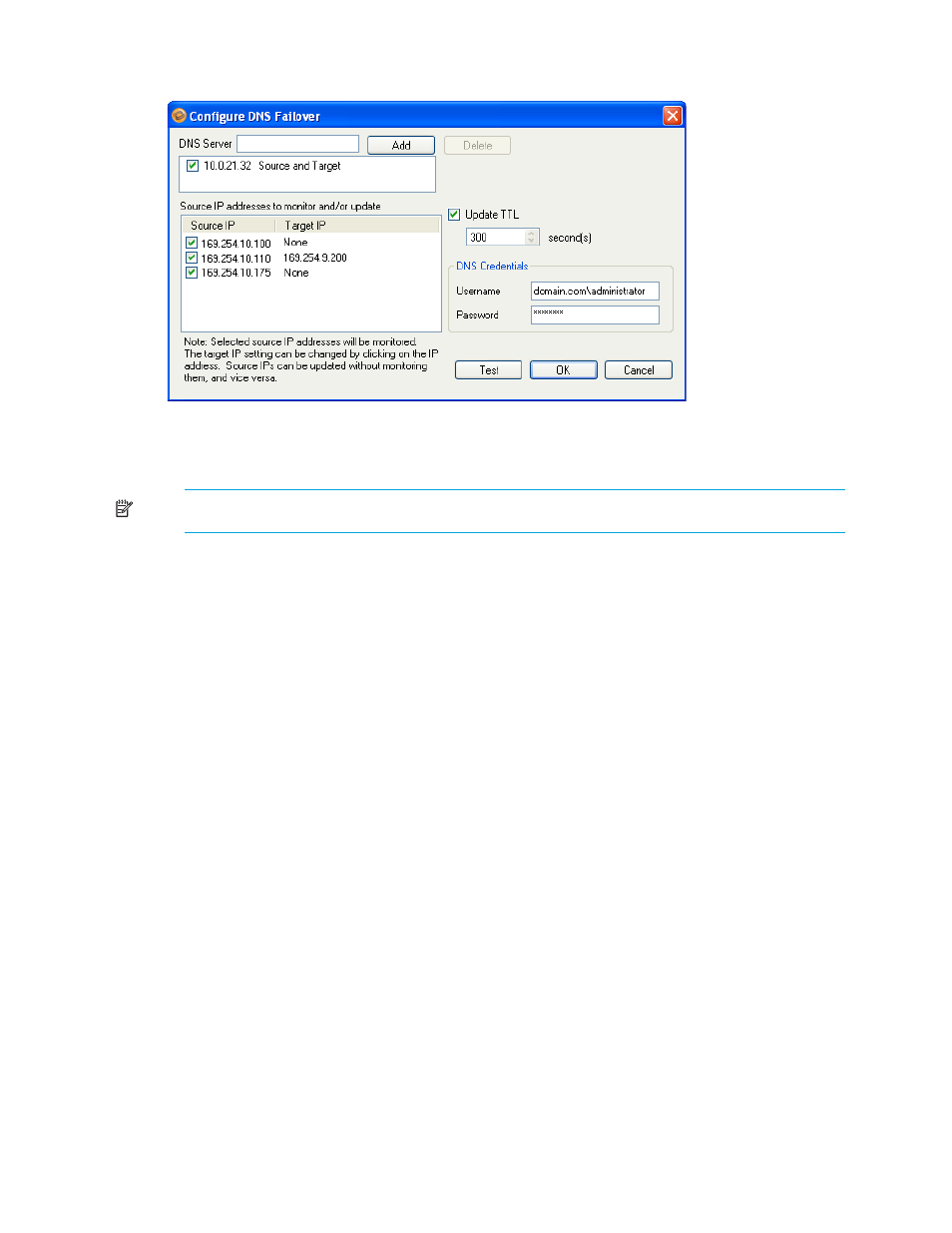
If you want to modify DNS configuration options, click
Configure
. The
Configure DNS Failover
window will
appear.
9.
On the
Configure DNS
window, you can modify the TTL value for the DNS record. You can also specify the
user credentials needed to modify DNS. When you are finished, you can click
Test
to test the DNS
configuration for the selected DNS server(s), or click
OK
to return to the
Configure Protection
window.
NOTE:
Decreasing the TTL value will increase the speed at which clients get the updated information.
10.
After you have changed the configuration parameters, click
OK
to apply the settings and return to the
Manage Exchange
window. If you click
Cancel
, any changes you have made will be discarded and the
previous configuration parameters will be used.
11.
Click
Validate
to validate the selected cluster pair. The validation proceeds exactly like validation for other
methods of failover.
12.
Click
Enable Protection
to enable protection for the source cluster.
Enabling protection
After protection is enabled, the Storage Mirroring Application Manager creates four resources on the target
cluster: two generic script resources, an IP address resource, and a temporary name resource. The temporary
name resource is the source EVS name with “_LN” appended to the end. The Application Manager uses the
temporary name resource for the connection between the source and target clusters. The Application Manager
gets the order of the source cluster resources from the Microsoft Cluster DLL, then builds the scripts with the
resources in order and based off the source’s resources configuration.
