Wireless security – Ubiquiti Networks PowerBridgM User Manual
Page 25
22
Chapter 4: Wireless Tab
airOS
™
v5.5.4 User Guide
Ubiquiti Networks, Inc.
Antenna Gain
(Only applicable to devices with external
antenna connectors.) Enter the antenna gain in dBi. With
Auto Adjust to EIRP Limit enabled, Antenna Gain calculates
the TX power backoff needed to remain in compliance
with local regulations. The Antenna Gain setting
complements the Cable Loss setting; they both affect the
TX power of the device.
Cable Loss
(Only applicable to devices with external
antenna connectors.) Enter the cable loss in dB. With
Auto Adjust to EIRP Limit enabled, Cable Loss affects the TX
power of the device. In case you have high amounts of
cable loss, you may increase the TX power while remaining
in compliance with local regulations. The Cable Loss
setting complements the Antenna Gain setting; they both
affect the TX power of the device.
Output Power
Defines the maximum average transmit
output power (in dBm) of the device. To specify the output
power, use the slider or manually enter the output power
value. The transmit power level maximum is limited
according to country regulations. (If the device has an
internal antenna, then Output Power is the output power
delivered to the internal antenna.)
Data Rate Module
(Not applicable to the airGateway.)
You have a choice of data rate algorithms to use for your
link, Default or Alternative. If the Default is not working
well for your link, you can try the Alternative to determine
which is the best data rate algorithm for your individual
situation. The Alternative tries to move the link to a higher
data rate but continuously monitors the packet failure
counters. You should get more stable data rates when
using the Alternative; however, results will vary depending
on the link’s specific environment and configuration. For
example, if a problematic link has traffic stability issues
and uses the Default, you may want to try the Alternative
to see if it improves the situation.
Note:
You can select Default or Alternative on
a single device; this option does not depend
on which algorithm is selected on the AP or its
stations.
Max TX Rate, Mbps
Defines the data rate (in Mbps) at
which the device should transmit wireless packets. You
can fix a specific data rate between MCS 0 and MCS 7 (or
MCS 15 for 2x2 chain devices). We recommend that you
use the automatic option, especially if you are having
trouble getting connected or losing data at a higher rate.
In this case, the lower data rates will be used automatically.
If you select 20 MHz Channel Width, the maximum data
rate is MCS 7 (65 Mbps) or MCS 15 (130 Mbps). If you select
40 MHz Channel Width, the maximum data rate is MCS 7
(150 Mbps) or MCS 15 (300 Mbps).
•
Automatic
If enabled, the rate algorithm selects the
best data rate, depending on link quality conditions. We
recommend that you use this option, especially if you
are having trouble getting connected or losing data at a
higher rate. For more information about data rates, refer
to ”Advanced Wireless Settings” on page 49.
Wireless Security
In Access Point or AP‑Repeater mode, configure the wireless
security settings that will be used by the devices on your
wireless network.
In Station mode, enter the security settings of the AP that
the device is associated with.
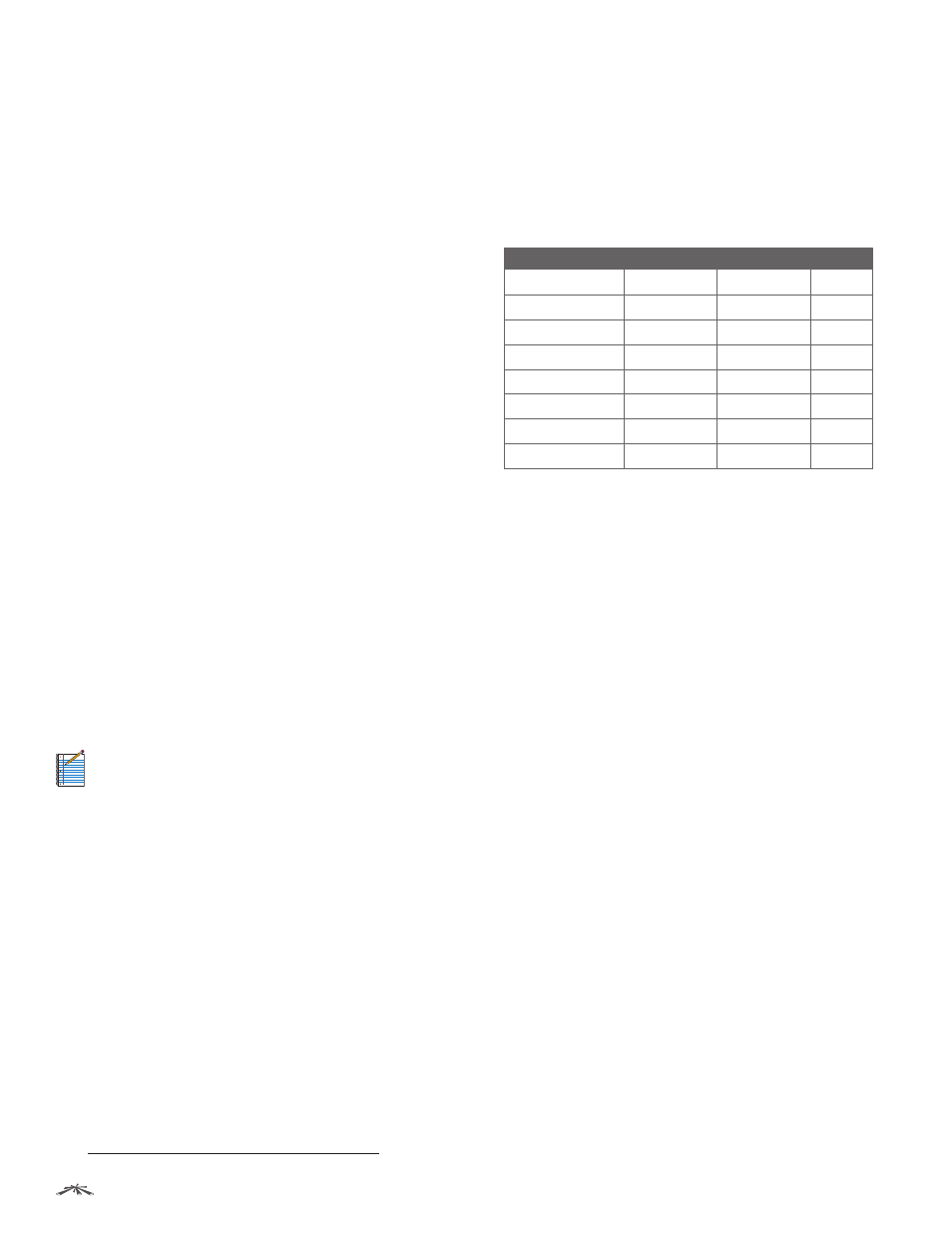
The following table lists the wireless security methods
available for each wireless mode:
Security Method
Access Point
AP‑Repeater
Station
none
✓
1
✓
1
✓
WEP
✓
2
✓
2
✓
WPA
✓
✓
WPA-TKIP
✓
✓
WPA-AES
✓
✓
WPA2
✓
✓
WPA2-TKIP
✓
✓
WPA2-AES
✓
✓
1 If you select none as your security method, then this may compromise the
security of your network; however, you have the options of using RADIUS MAC
Authentication and MAC ACL.
2 If you select WEP as your security method, then this may compromise the
security of your network; however, you have the option of using MAC ACL.
Security
airOS supports the following wireless security
methods:
•
none
If you want an open network without wireless
security, select none. You still have the option of using
RADIUS MAC authentication and MAC ACL.
•
WEP
WEP (Wired Equivalent Privacy) is the oldest
and least secure security algorithm. Use WPA or WPA2
security methods when possible.
•
WPA
WPA (Wi-Fi Protected Access) was developed as a
stronger encryption method than WEP.
•
WPA‑TKIP
WPA (Wi-Fi Protected Access) security mode
with TKIP (Temporal Key Integrity Protocol) support
only. TKIP uses the RC4 encryption algorithm. There is a
performance limitation to using TKIP, so we recommend
using AES.
•
WPA‑AES
WPA security mode with AES (Advanced
Encryption Standard) support only. AES is also known
as CCMP (Counter Mode with Cipher Block Chaining
Message Authentication Code Protocol), which uses the
AES algorithm.
•
WPA2
WPA2 was developed to strengthen wireless
encryption security and is stronger than WEP and WPA.
•
WPA2‑TKIP
WPA2 security mode with TKIP support
only. TKIP uses RC4 encryption algorithm. There is a
performance limitation to using TKIP, so we recommend
using AES.
•
WPA2‑AES
WPA2 security mode with AES support only.
This is the strongest security option available. If all of the
wireless devices on your network support this option,
we recommend that you select it.
