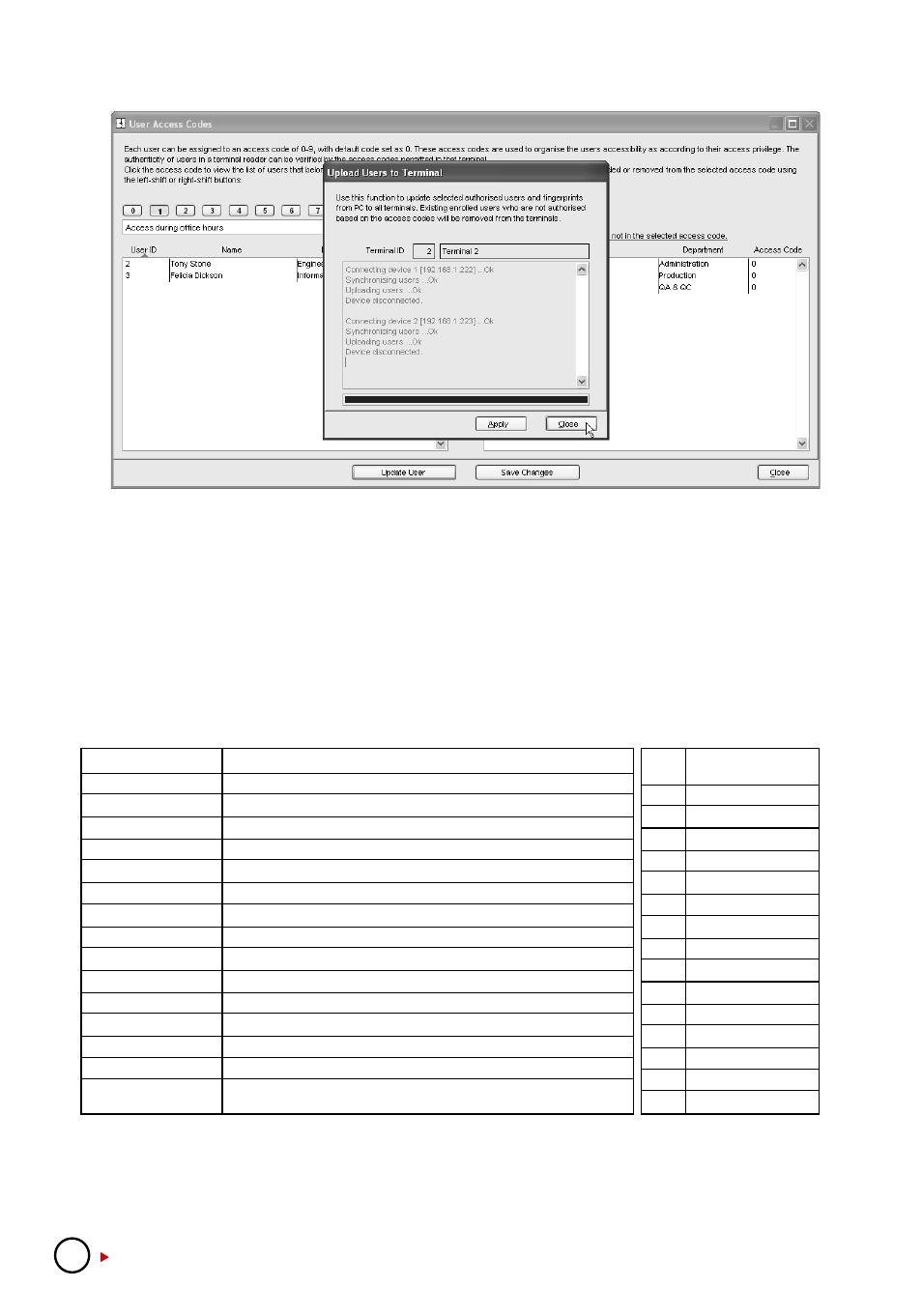
Different verification methods – FingerTec DiGiTime (OEM) User Manual
Page 71
70
Type of verifications Operations
FP / PW / RF
Terminal verifies users with fingerprint, password OR RFID card.
FP
Terminal verifies users with fingerprint only.
PIN
Terminal verifies users with User ID only.
PW
Terminal verifies users with password only.
RF
Terminal verifies users with RFID card only.
FP / PW
Terminal verifies users with fingerprint OR password.
FP / RF
Terminal verifies users with fingerprint OR RFID card.
PW / RF
Terminal verifies users with via password OR RFID card.
PIN & FP
Terminal verifies users with 1:1 fingerprint matching only.
FP & PW
Terminal verifies users with fingerprint AND password only.
FP & RF
Terminal verifies users with fingerprint AND RFID card only.
PW & RF
Terminal verifies users with password AND RFID card only.
FP & PW & RF
Terminal verifies users with fingerprint AND password AND RFID card.
PIN & FP & PW
Terminal verifies users with User ID AND fingerprint AND password.
FP & RF / PIN
Terminal verifies users with fingerprint AND RFID card OR 1:1 finger-
print matching.
Group Types of Verification
method
1
FP / PW / RF
2
FP
3
PIN
4
PW
5
RF
6
FP / PW
7
FP / RF
8
PW / RF
9
PIN & FP
10
FP & PW
11
FP & RF
12
PW & RF
13
FP & PW & RF
14
PIN & FP & PW
15
FP & RF / PIN
Different Verification Methods
By default, all models support one of these verification methods, fingerprint, password, card
or fingerprint with card. However, some of the models support two verification methods for
one user, for example, a user enrolls with both fingerprint and password. During verifica-
tion, the user must provide his fingerprint followed by his password to gain a successful
verification.
There are a total of 15 verification types available:
Each terminal can support 15 groups for different verification method. Configurations can
be done as below:
Now you can assign users into the groups so that they can comply with the verification
methods.
