Authenticate --update --kerberos, Authenticate --add [--user Page 31
Page 31
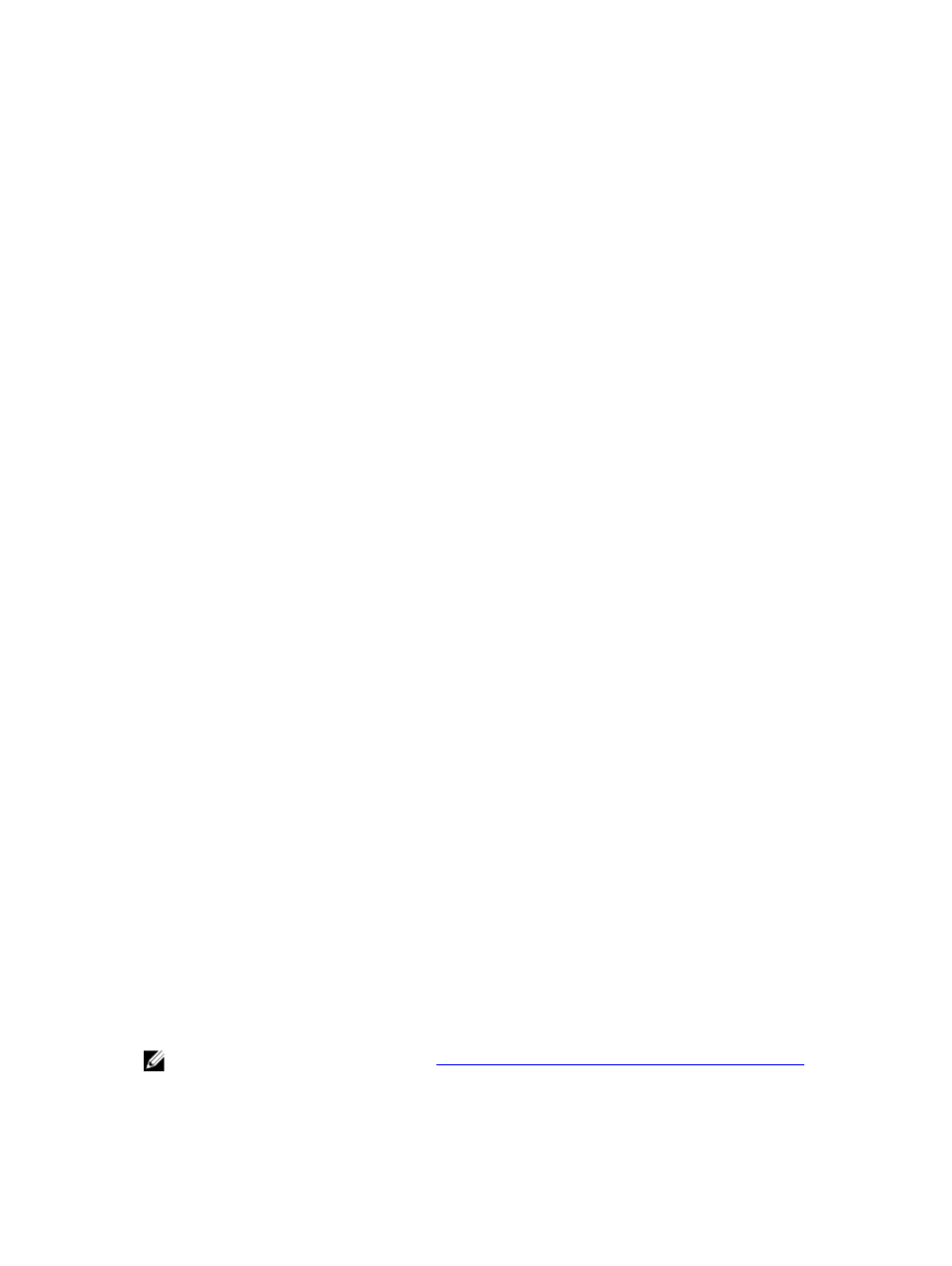
authenticate --update --kerberos
Description
Updates a Microsoft Active Directory Service (ADS) Kerberos configuration (Kerberos is a computer network
authentication protocol).
Syntax
authenticate --update --kerberos
Result
Updated kerberos configuration.
authenticate --add [--user
Description
Adds a new local CIFS workgroup user for CIFS authentication (and administrative tasks) after you provide and confirm
the CIFS user password.
Syntax
authenticate --add --user administrator2
Result
Enter password for new CIFS user administrator2:
Re-enter password for new CIFS user administrator2:
Added CIFS user administrator2.
authenticate --add [--login_group
Description
Adds an authenticated login group in an Active Directory Services (ADS) domain in accordance with the following ADS
login group guidelines:
•
Log in as an administrator via the CLI, and use SSH, Telnet, or a local console connection as a domain\user that is
part of a login group. When you log in as an administrator via the CLI, you are prompted to use the credentials of the
user account by which you log in (for example: if you log in as a Domain\administrator, you need to respond using
these credentials).
•
Log in as an administrator via the GUI, and use a web interface connection as a domain\user that is part of a login
group (when this has been enabled via the CLI).
•
If no login group is specified, or the group is disabled, no access using domain accounts is permitted.
•
Adding a login group can only be enabled via the CLI.
•
Adding a login group is only possible when the DR Series system is already joined to a domain.
•
If the login group name has a space in it, it must be contained within double-quotation marks (“ “).
•
When adding a login group, it must use the naming convention of Domain\group name.
•
The login group must exist in the domain before you can add it (a check is performed to verify that the group exists in
ADS).
•
Changes made to the login group take effect on the next log in attempt (no active checking is done on group, which
matches how Windows ADS works).
NOTE: To delete an existing login group, see
authenticate --delete [--login_group
.
31
