Option 5 - delete user, Option 6 - show the list of authorized users, Option 7 - add group – AMX Signature Series NetLinx Integrated Controller NI-3101-SIG User Manual
Page 115: Edit group menu
NetLinx Security with a Terminal Connection
105
NI-3101-SIG Signature Series NetLinx Integrated Controller
Option 5 - Delete user
1.
Type 5 and
existing user account. A sample session response is:
Select from the following list of enrolled users:
1) administrator
2) NetLinx
3) techpubs
4) Pat
Select User ->
2.
Enter the value associated to the user you want to delete and press
account and returns you to the Security Setup menu.
Option 6 - Show the list of authorized users
1.
Type 6 and
of currently enrolled users.
2.
Press
Option 7 - Add Group
1.
Type 7 and
group account. A sample session response is:
The following groups are currently enrolled:
administrator
Enter name of new group:
2.
Enter a name for the group. A group name is a valid character string (4 - 20 alpha-numeric characters)
defining the group. This string is case sensitive, and each group name must be unique.
3.
Press
Edit Group Menu
Please select from the following options:
1) Add Directory Association
2) Delete Directory Association
3) List Directory Associations
4) Change Access Rights
5) Display Access Rights
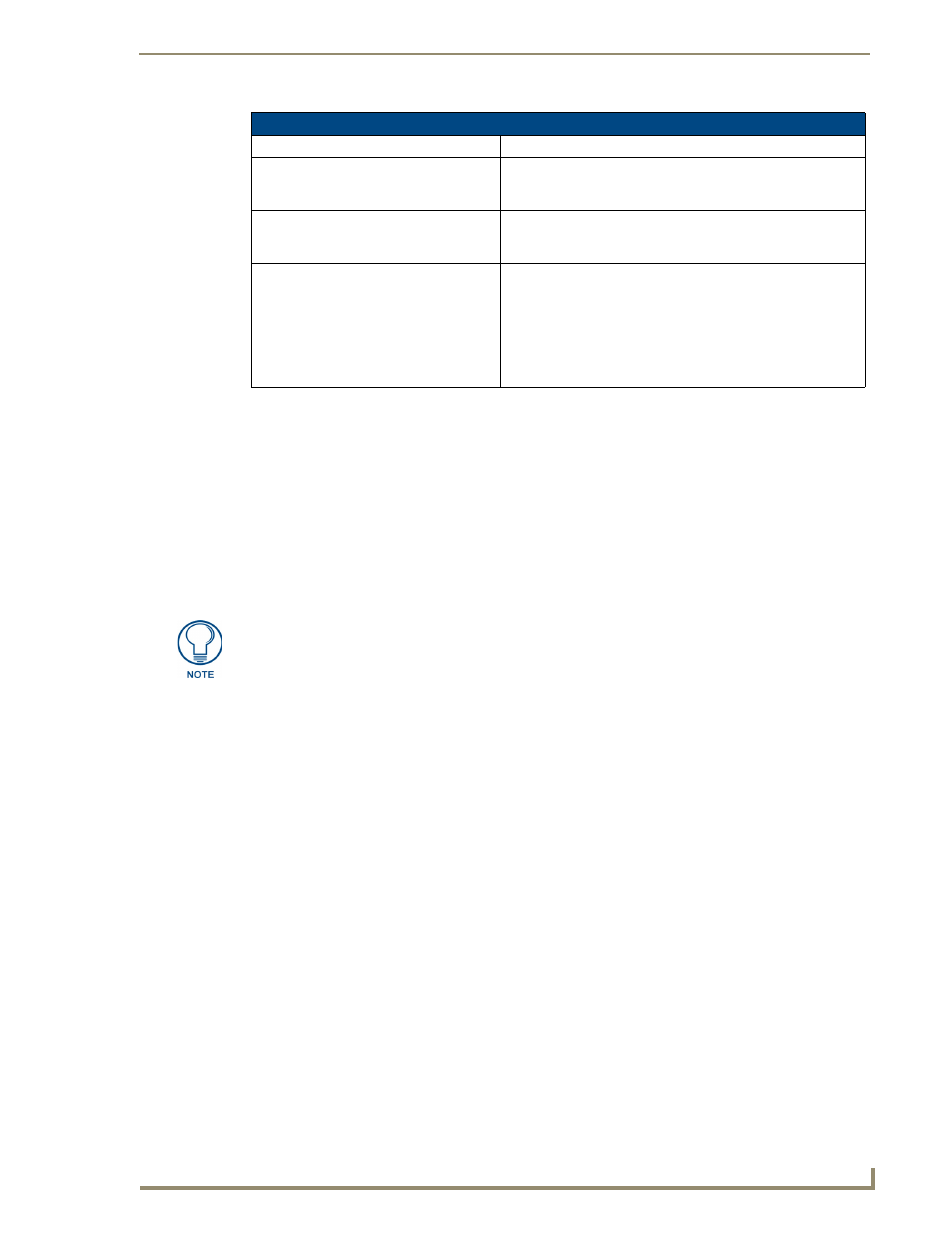
Access Rights Menu (Cont.)
Command
Description
6) Configuration Access
(Enable/Disable)
This selection enables/disables Configuration Access rights for
the target Master. The account has sufficient access rights to
access the Main Security Menu if this option is enabled.
5) ICSP Security
(Enabled/Disabled)
This selection enables/disables ICSP communication access.
The account has sufficient access rights to initiate ICSP data
communication.
6) ICSP Encryption Required
(Enabled/Disabled)
This selection enables/disables the need to require encryption of
the ICSP communicated data.
If enabled:
- All communicating AMX components must authenticate with
a valid username and password before beginning
communication with the Master.
- All communication must be encrypted.
Changes made to the target Master from within the Terminal window are not reflected
within the web browser, until the Master is rebooted and the web browser connection
is refreshed. Any changes made to the Master, from within the web browser are
instantly reflected within the Terminal session without the need to reboot.
