Stateful inspection, 4 stateful inspection – ZyXEL Communications ZYWALL10 User Manual
Page 163
ZyWALL 10 Internet Security Gateway
13-6
What Is a Firewall?
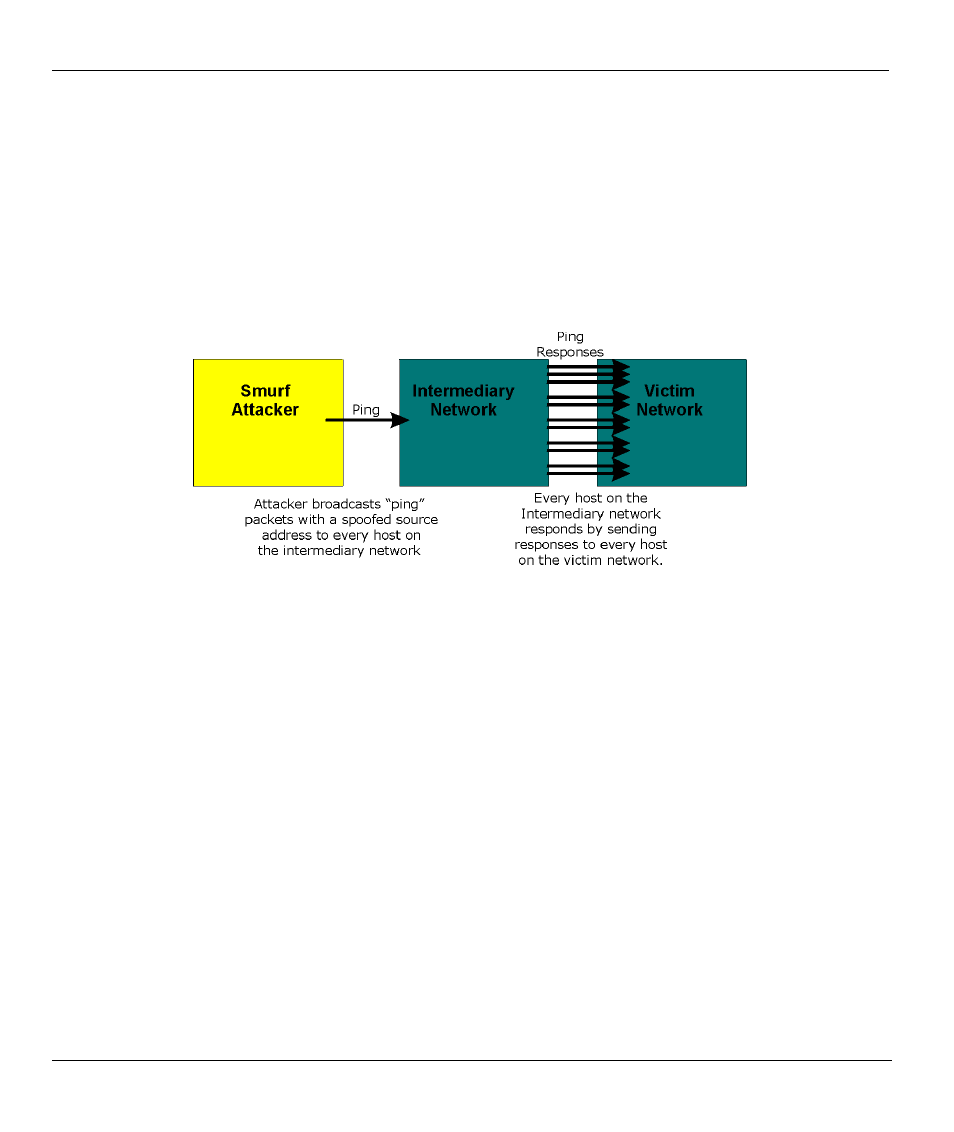
3. A brute-force attack, such as a "Smurf" attack, targets a feature in the IP specification known as
directed or subnet broadcasting, to quickly flood the target network with useless data. A Smurf hacker
floods a router with Internet Control Message Protocol (ICMP) echo request packets (pings). Since the
destination IP address of each packet is the broadcast address of the network, the router will broadcast
the ICMP echo request packet to all hosts on the network. If there are numerous hosts, this will create a
large amount of ICMP echo request and response traffic. If a hacker chooses to spoof the source IP
address of the ICMP echo request packet, the resulting ICMP traffic will not only clog up the
"intermediary" network, but will also congest the network of the spoofed source IP address, known as
the "victim" network. This flood of broadcast traffic consumes all available bandwidth, making
communications impossible.
Figure 13-4 Smurf Attack
4. Often, many DoS attacks also employ a technique known as "IP Spoofing" as part of their attack. IP
Spoofing may be used to break into systems, to hide the hacker's identity, or to magnify the effect of the
DoS attack. IP Spoofing is a technique used to gain unauthorized access to computers by tricking a
router or firewall into thinking that the communications are coming from within the trusted network. To
engage in IP spoofing, a hacker must modify the packet headers so that it appears that the packets
originate from a trusted host and should be allowed through the router or firewall. The ZyWALL blocks
all IP Spoofing attempts.
13.4 Stateful Inspection
With stateful inspection, fields of the packets are compared to packets that are already known to be trusted.
For example, if you access some outside service, the proxy server remembers things about your original
request, like the port number and source and destination addresses. This “remembering” is called saving the
state. When the outside system responds to your request, the firewall compares the received packets with the
saved state to determine if they are allowed in. The ZyWALL uses stateful packet inspection to protect the
private LAN from hackers and vandals on the Internet. By default, the ZyWALL’s stateful inspection allows
all communications to the Internet that originate from the LAN, and blocks all traffic to the LAN that
originates from the Internet. In summary, stateful inspection:
!
Allows all sessions originating from the LAN (local network) to the WAN (Internet).
