Layer 2 protocol tunneling, 1 layer 2 protocol tunneling overview, Chapter 29 layer 2 protocol tunneling – ZyXEL Communications XGS-4526 User Manual
Page 273: Layer 2 protocol tunneling (273)
XGS-4526 User’s Guide
273
C
H A P T E R
2 9
Layer 2 Protocol Tunneling
This chapter shows you how to configure layer 2 protocol tunneling on the Switch.
29.1 Layer 2 Protocol Tunneling Overview
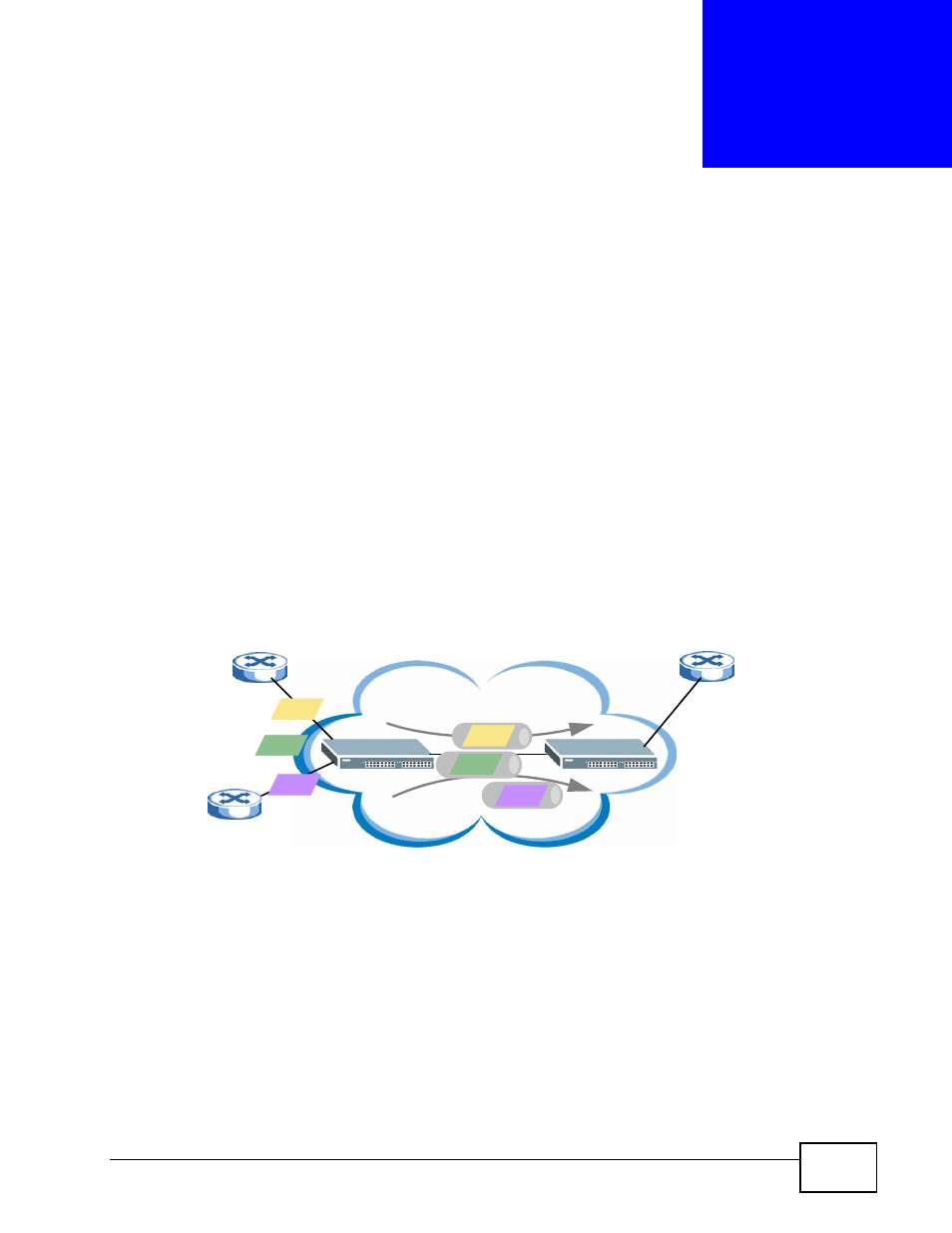
Layer 2 protocol tunneling (L2PT) is used on the service provider's edge devices.
L2PT allows edge switches (1 and 2 in the following figure) to tunnel layer 2 STP
(Spanning Tree Protocol), CDP (Cisco Discovery Protocol) and VTP (VLAN Trunking
Protocol) packets between customer switches (A, B and C in the following figure)
connected through the service provider’s network. The edge switch encapsulates
layer 2 protocol packets with a specific MAC address before sending them across
the service provider’s network to other edge switches.
Figure 140 Layer 2 Protocol Tunneling Network Scenario
In the following example, if you enable L2PT for STP, you can have switches A, B,
C and D in the same spanning tree, even though switch A is not directly
connected to switches B, C and D. Topology change information can be
propagated throughout the service provider’s network.
To emulate a point-to-point topology between two customer switches at different
sites, such as A and B, you can enable protocol tunneling on edge switches 1 and
1
2
A
C
Service Provider's
Network
STP
CDP
B
VTP
STP
VTP
CDP
