2 secure shell access, 3 encryption algorithm, Secure shell access encryption algorithm – Fortress Technologies ecure Wireless Access Bridge User Manual
Page 49
Fortress Bridge: Configuration
39
If the Bridge fails any self-test on startup, it is rendered
inoperable and must be returned to the vendor for repair or
replacement.
Only a designated Crypto Officer, as defined by the Federal
Information Processing Standards, may perform
administrative functions on the Bridge and its Secure
Clients.
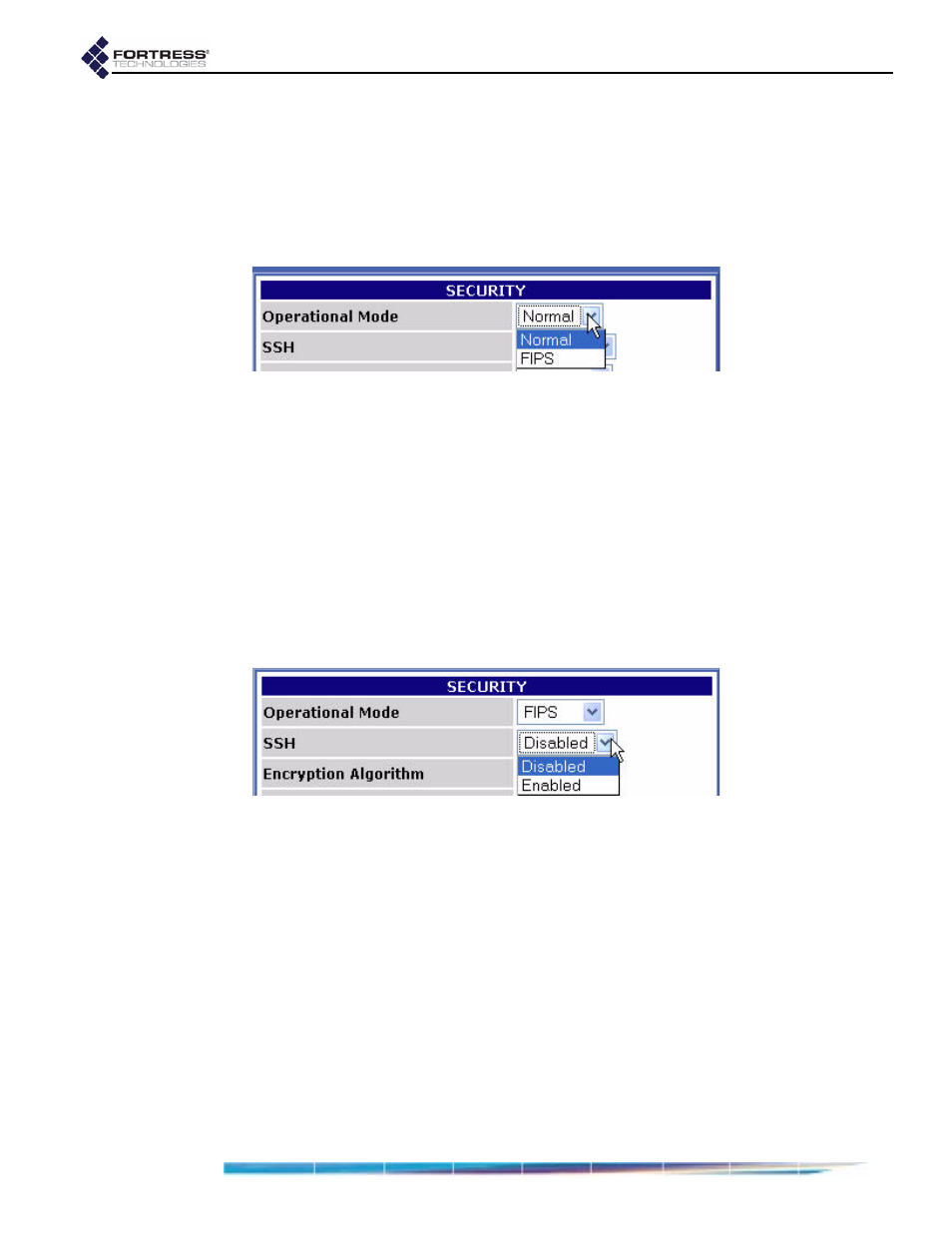
To change the Bridge operating mode:
1
Log on to the Bridge GUI
admin
account and select
SECURITY
SETTINGS
from the menu on the left.
2
In the
SECURITY
section of the
SECURITY
SETTINGS
screen,
select the Bridge’s operating mode.
3
Click
Apply
at the bottom of the screen.
3.6.2
Secure Shell Access
In order to access the Bridge CLI from a network connection to
the Bridge’s management interface, Secure Shell (SSH) must
be enabled. When SSH is disabled, you can access the Bridge
CLI exclusively through a direct connection to its
Console
port.
Secure Shell (SSH) is disabled on the Bridge by default.
To configure SSH access to the Bridge CLI:
1
Log on to the Bridge GUI
admin
account and select
SECURITY
SETTINGS
from the menu on the left.
2
In the
SECURITY
section of the
SECURITY
SETTINGS
screen,
select whether SSH is
Enabled
or
Disabled
.
3
Click
Apply
at the bottom of the screen.
3.6.3
Encryption Algorithm
The Bridge supports the strong, AES encryption standard at
these user-specified key lengths:
AES-256 (default)
AES-192
AES-128
All Secure Clients logging on to the Bridge must be configured
to use the same encryption algorithm and key length as the
detail:
detail:
