Configuring inverse split tunneling – Panasonic 7 User Manual
Page 85
Attention! The text in this document has been recognized automatically. To view the original document, you can use the "Original mode".
Chapter 4 Configuring user tunnels 85
LDAP search allows you to enter any LDAP database attribute that is part
of the person, organizational Person, or inetOrgPerson object database
(for example, cn=common name or sn=surname) to generate the
associated user’s profile. Refer to your LDAP vendor’s documentation for
complete details.
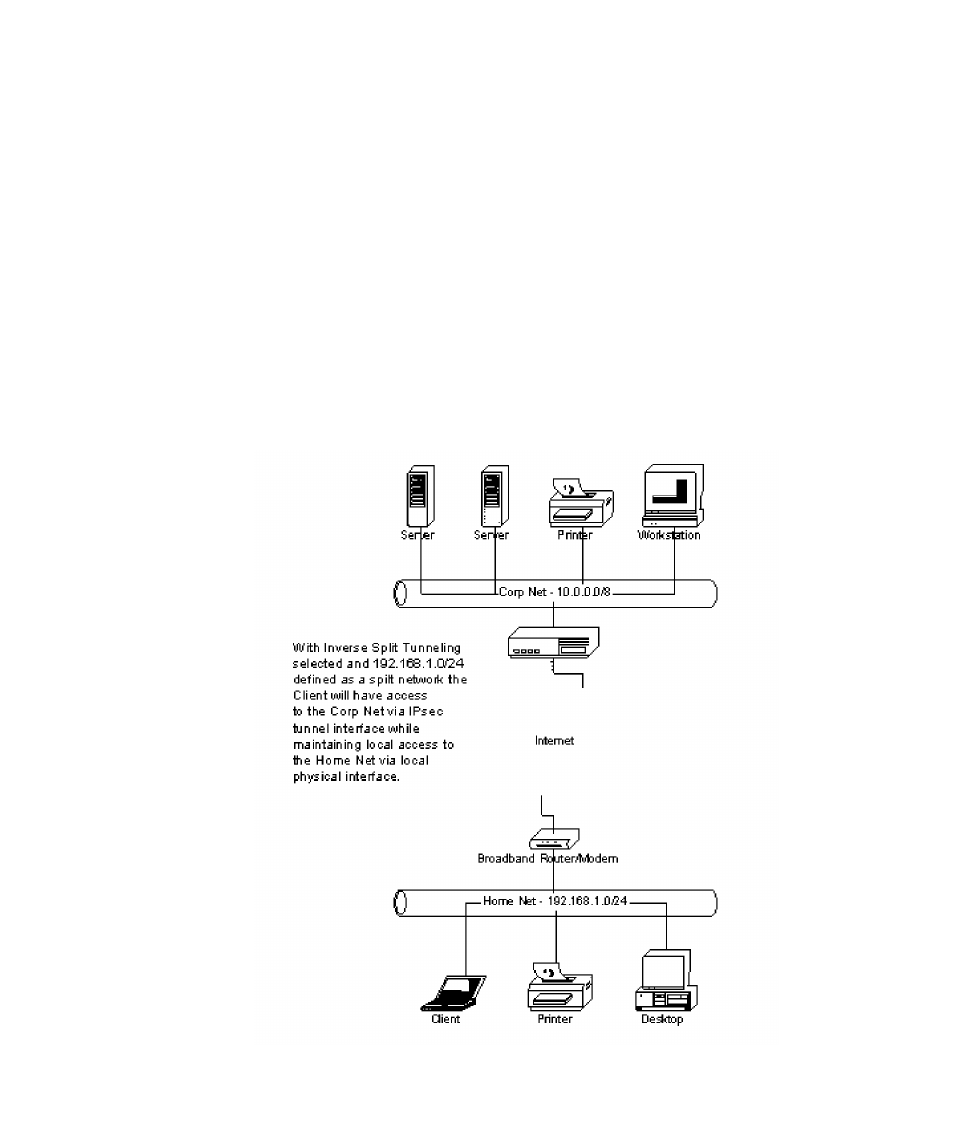
Configuring inverse split tunneling
Inverse split tunneling (Figure 10) provides the flexibility of allowing remote
users access to network resources outside of the mandatory tunnel while still
maintaining most of the security advantages of this tunnel type.
Figure 10 Inverse Split Tunneling
Nortel VPN Router Configuration — Basic Features
- Infrared Light Emitting Diodes SHC00023CED (4 pages)
- Light Emitting Diodes LN217RPH (3 pages)
- UP0KG8DG (6 pages)
- Light Emitting Diodes SHD00438BEK (3 pages)
- 2SC2406 (5 pages)
- 2SC6036 (3 pages)
- Band Switching Diodes MA27077G (4 pages)
- MA21D382G (4 pages)
- WV-PS31 (2 pages)
- 2SA2174G (4 pages)
- UP0KG8D (5 pages)
- 2SD0965 (3 pages)
- LNG497CK4 (3 pages)
- Light Emitting Diodes LNG0A8CYBZ (3 pages)
- BL-PA100A (32 pages)
- Light Emitting Diodes LN29RPX (3 pages)
- AC Adaptor AG-B15 (8 pages)
- 2SA2079 (3 pages)
- 2SA1790G (4 pages)
- 2SA1748 (3 pages)
- Chip RC Networks EZANT (9 pages)
- 2SB0792A (4 pages)
- 2SA1309A (3 pages)
- Zener Diodes MAZSxxxG Series (8 pages)
- WJ-NT314 (2 pages)
- MA26P02 (2 pages)
- MA27P070G (4 pages)
- CF-VFS372 (4 pages)
- FP (Sigma) (20 pages)
- 2SC2634 (3 pages)
- Light Emitting Diodes LNJ024X4ARA1 (3 pages)
- MA27P010G (4 pages)
- LN1261CTR (3 pages)
- WJ-NT104 (84 pages)
- KX-RC22 (48 pages)
- WJ-NT304 (20 pages)
- AJ-HDP2000P (20 pages)
- TC-32LX60L (34 pages)
- MA271110G (4 pages)
- 2SC4656G (4 pages)
- 2SA2174J (3 pages)
- 2SA2009G (4 pages)
- 2SB0710A (4 pages)
- WJ-PB65E01 (8 pages)
- LNJ216C8ARA (3 pages)
