Security domains, Deployment scenarios, Remote and local key management requirements – HP Secure Encryption User Manual
Page 13
Planning 13
unencrypted when accessed from the host system and placed on tape. Software or hardware utilizing an
independent encryption feature is not impacted by HP Secure Encryption.
Security domains
A security domain is a blueprint for separating out different groups of servers or key management escrows
where access to a set of keys is inhibited by the structure of the various domains. The best mechanisms for
establishing separate security domains are either through the use of separate HP ESKM 3.1 or via the use of
groups within the HP ESKM 3.1. Unique groups provide a software mechanism for each server to partition
off their key sets from one server to another. Groups are created on the HP ESKM 3.1 and assigned to a
server via the HP iLO Key Manager page. For more information, see "Remote Key Management Mode (on
)."
Deployment scenarios
Remote and local key management requirements
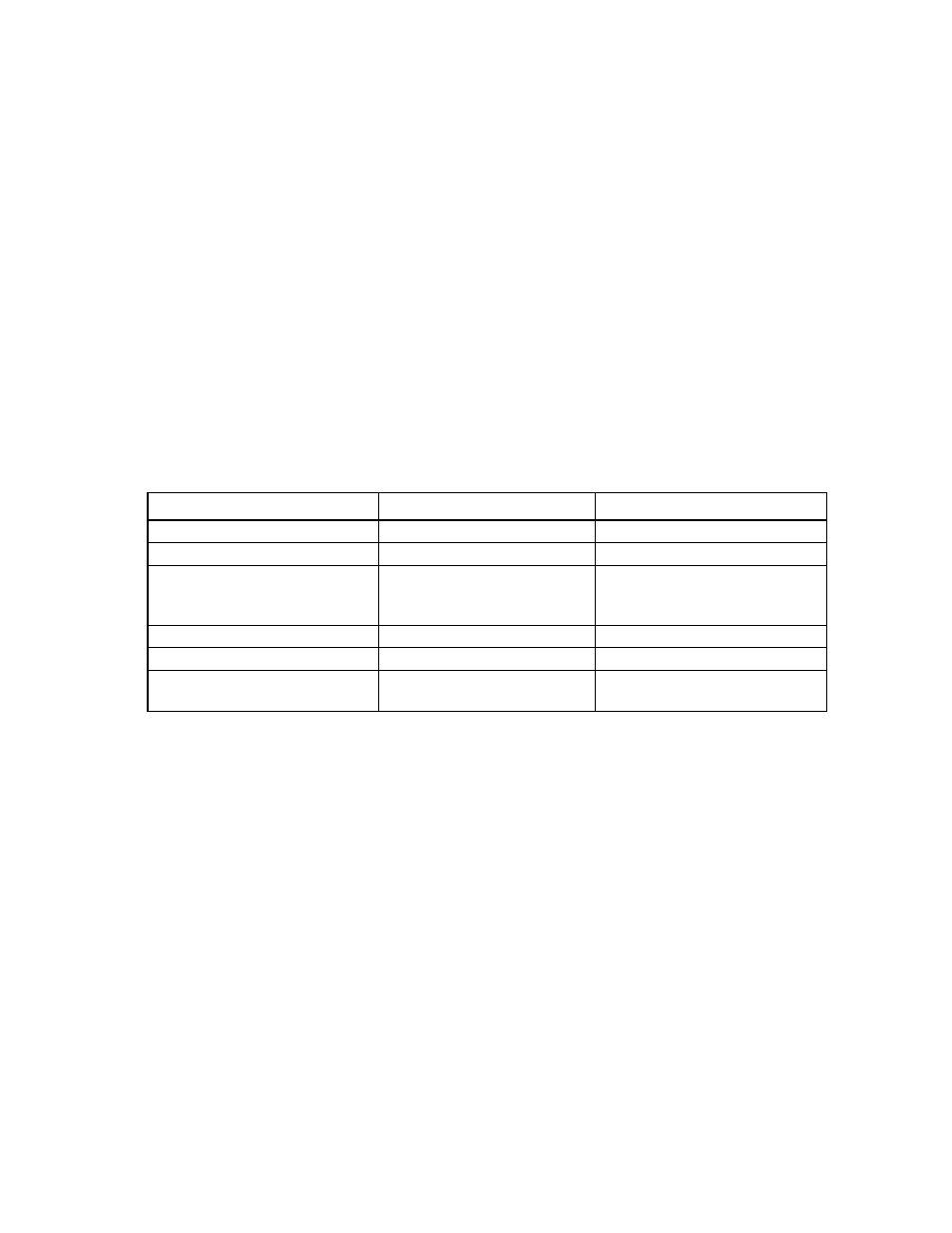
Use the table below to determine which encryption mode is right for you.
Mode parameters
Local Key Management Mode Remote Key Management Mode
Number of servers
<99 (recommended)
100 or more
Support of HP ESKM 3.1 by customer No
Yes
Utilize Integrated Lights Out (iLO)
Advanced or Scale Out License in the
infrastructure
No
Yes
Requirement to escrow keys
No
Yes
Manual tracking of keys
Yes
No
Poor or no network connectivity to HP
ESKM 3.1
Yes
No
