HP StorageWorks XP Remote Web Console Software User Manual
Page 51
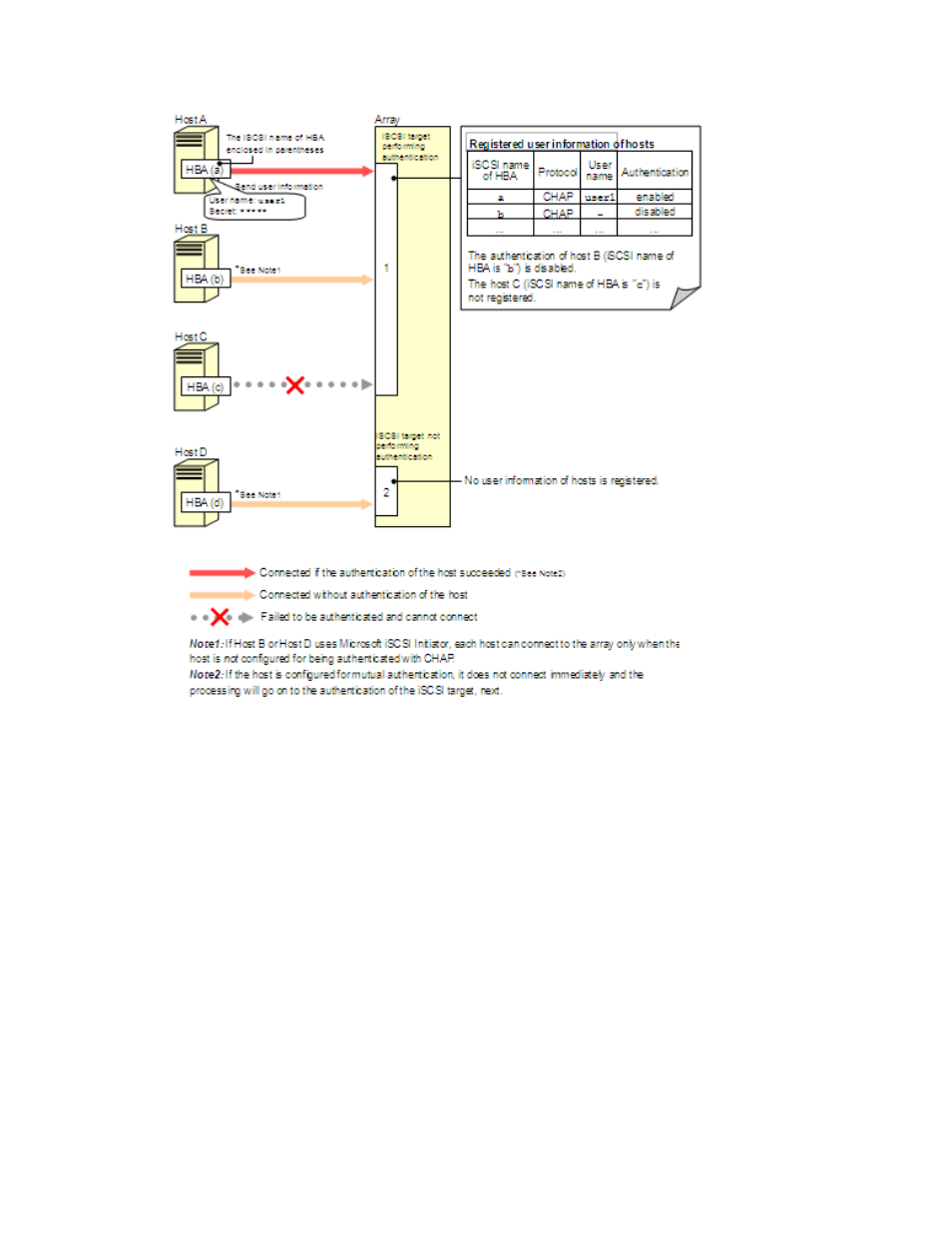
LUN Configuration and Security Manager XP user guide for the XP12000/XP10000/SVS200
51
shows an example of authentication of hosts. In this figure, iSCSI names of host bus adapters
(HBAs) are abbreviated as a, b, and so on.
Figure 13
Example of authentication of hosts (iSCSI environments)
In
, iSCSI target 1 performs authentication of hosts, but iSCSI target 2 does not.
Host A’s user information is registered on iSCSI target 1, and the authentication setting is enabled.
Therefore, if authentication of the host succeeds, Host A can connect to the array (or processing goes to
the authentication of the iSCSI target). As a precondition of successful authentication, configure Host A for
authentication by iSCSI targets with CHAP.
Host B’s user information is also registered on iSCSI target 1, but the authentication setting is disabled.
Therefore, Host B can connect to the array without authentication. (If Host B uses Microsoft iSCSI Initiator,
Host B can connect to the array only when Host B is not configured for authentication by iSCSI targets
with CHAP.)
Host C’s user information is not registered on iSCSI target 1. Therefore, when Host C tries to connect to
the array, authentication fails and the connection request is denied regardless of Host C’s setting.
Host D is attached to iSCSI target 2, which does not perform authentication of hosts. Therefore, Host D
can connect to the array without authentication. In this case, it does not matter whether Host D’s user
information is registered on iSCSI target 2. (If Host D uses Microsoft iSCSI Initiator, Host D can connect to
the array only when Host D is not configured for authentication by iSCSI targets with CHAP.)
For more information, see:
•
Enabling and disabling authentication of hosts on iSCSI targets
•
Registering a host’s user information on an iSCSI target
•
Settings and connection results in authentication of hosts (iSCSI environments)
