Brocade Fabric OS Encryption Administrator’s Guide Supporting NetApp Lifetime Key Manager (LKM) and KeySecure Storage Secure Key Manager (SSKM) Environments (Supporting Fabric OS v7.2.0) User Manual
Page 157
Fabric OS Encryption Administrator’s Guide (LKM/SSKM)
139
53-1002925-01
CryptoTarget container configuration
3
•
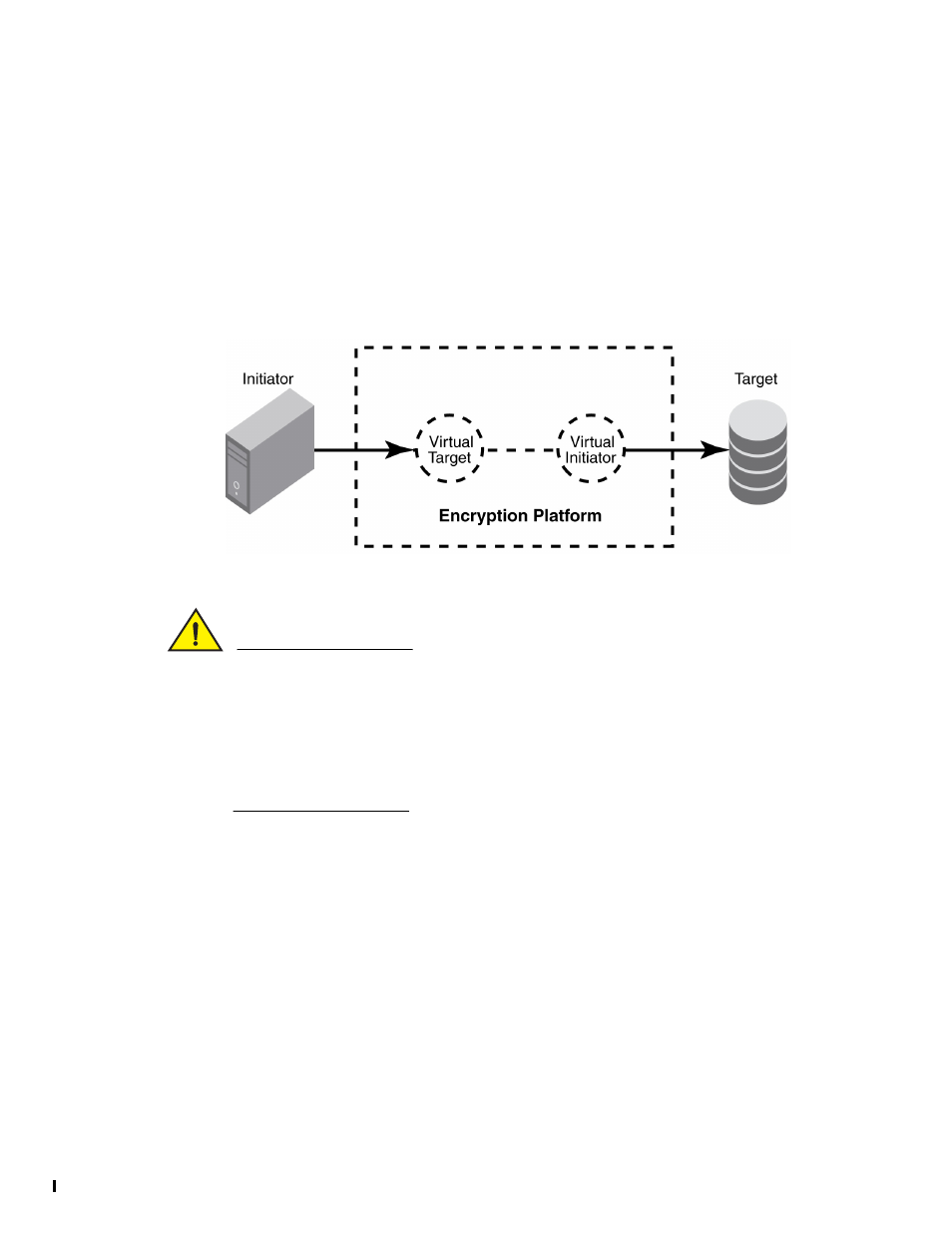
Virtual targets: Any given physical target port is hosted on one encryption switch or blade. If the
target LUN is accessible from multiple target ports, each target port is hosted on a separate
encryption switch or blade. There is a one-to-one mapping between virtual target and physical
target to the fabric whose LUNs are being enabled for cryptographic operations.
•
Virtual initiators: For each physical host configured to access a given physical target LUN, a
virtual initiator (VI) is generated on the encryption switch or blade that hosts the target port. If
a physical host has access to multiple targets hosted on different encryption switches or
blades, you must configure one virtual initiator on each encryption switch or blade that is
hosting one of the targets. The mapping between physical host and virtual initiator in a fabric is
one-to-n, where n is the number of encryption switches or blades that are hosting targets.
FIGURE 84
Relationship between initiator, virtual target, virtual initiator and target
CAUTION
When configuring a LUN with multiple paths, there is a considerable risk of ending up with
potentially catastrophic scenarios where different policies exist for each path of the LUN, or a
situation where one path ends up being exposed through the encryption switch and another path
has direct access to the device from a host outside the secured realm of the encryption platform.
Failure to follow correct configuration procedures for multi-path LUNs results in data corruption. If
you are configuring multi-path LUNs as part of an HA cluster or DEK cluster or as a stand-alone
LUN accessed by multiple hosts, follow the instructions described in the section
LUN rebalancing when hosting both disk and tape targets
If you are currently using encryption and running Fabric OS v6.3.x or earlier, you are hosting tape
and disk target containers on different encryption switches or blades. Beginning with Fabric OS
v6.4, disk Disk and tape target containers can be hosted on the same switch or blade. Hosting both
disk and tape target containers on the same switch or blade may result in a drop in throughput, but
it can reduce cost by reducing the number of switches or blades needed to support encrypted I/O
in environments that use both disk and tape.
The throughput drop can be mitigated by rebalancing the tape and disk target containers across
the encryption engine. This ensures that the tape and disk target containers are distributed within
the encryption engine for maximum throughput.
