Example of eserver setup network topology – Innotech eServer User Manual
Page 22
eServer Setup and Site Installation Instructions
Page 22
© Mass Electronics Pty Ltd 2009
Edition 5.0 dated 07/01/2014
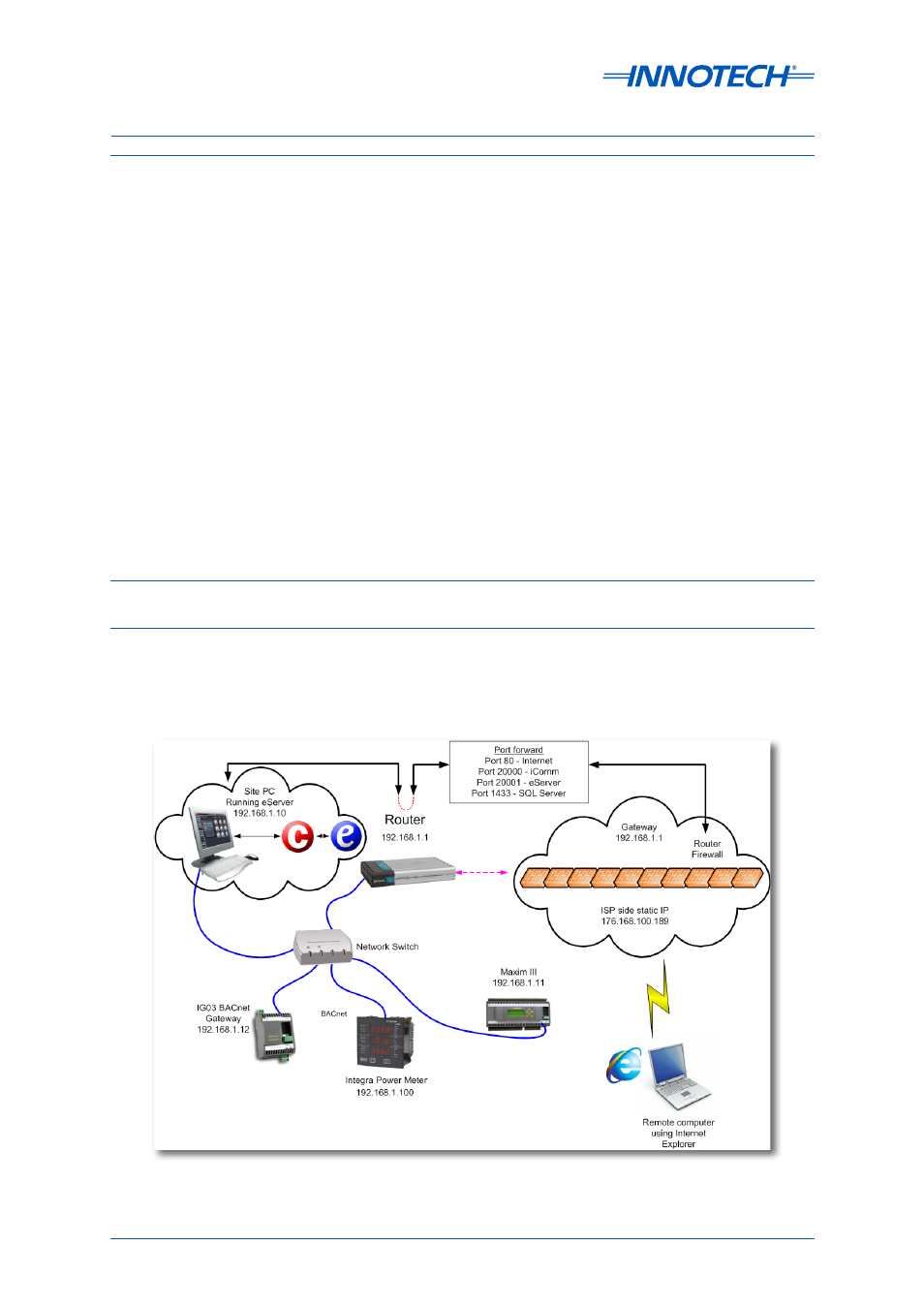
Figure 2-1: Example of eServer Setup Network Topology
2-2.2.3 Security Information
Both iComm and eServer are resistant to denial of service attacks from unauthenticated clients,
and both support 32-bit encryption with initial login challenge/response authentication. If a client's
login name and password is not authenticated immediately by eServer or iComm, the connection is
terminated.
Both servers have been tested for buffer overrun attacks, and both servers have an audit trail of
connection attempts. It is not possible, even with a custom-written rogue program that manages
proper authentication, for any program to connect to either of these servers and execute a file
or download unauthorised data from the server. Neither of these programs currently contains
functionality to allow file downloads, server-side execution, or any kind of interactive login.
To setup access over the internet, you will need to open Ports 80, 1433, 20000 and 20001 through the
Firewall to transmit and receive data. Then accept incoming connections, and Port Forward from the
external static IP address, to the internal static IP address of the computer running the iComm Server
and eServer software. You will be able to see who has logged in via the audit trails, even from an
eServer Client computer.
From the eServer Client computer, only ports 80, 1433, 20000 and 20001 need to be open for an
outgoing connection.
2-2.3 Setup of a Dedicated Site Computer with ADSL Connection
2-2.3.1 Overview
This section provides detailed information for configuring a site computer with a dedicated ADSL
connection for running the eServer software. Refer to Figure 2-1 for an example eServer setup
network topology.
