Displaying connection limit logs, Displaying attack prevention logs – H3C Technologies H3C SecBlade LB Cards User Manual
Page 57
48
Displaying connection limit logs
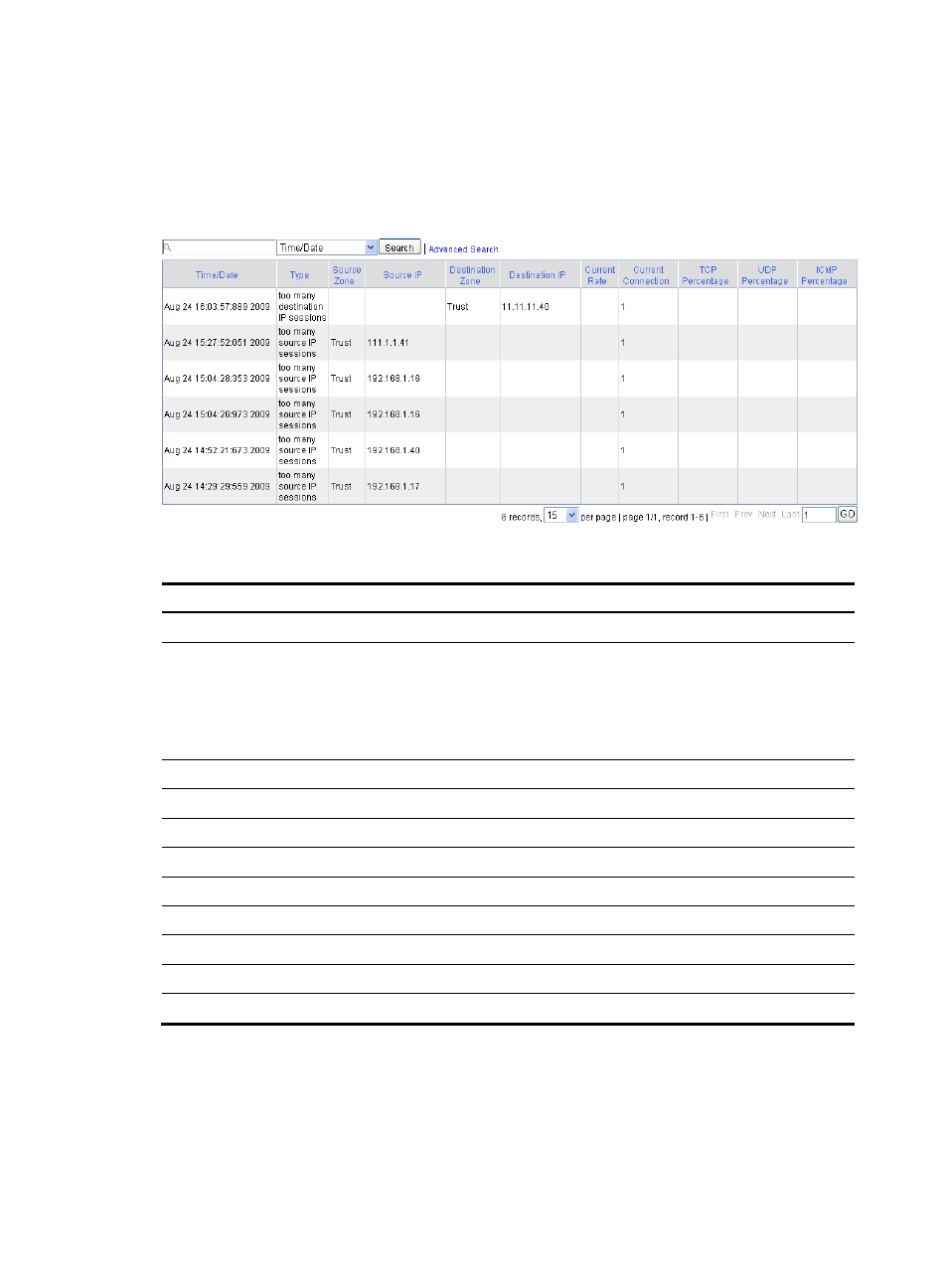
Select Log Report > Report > Connection Limit Log from the navigation tree to enter the page as shown
in
describes the configuration items.
Figure 18 Connection limit log configuration page
Table 15 Configuration items
Item Description
Time/Date
Time when the connection limit log was generated.
Type
Type of the traffic alarm:
too many source IP sessions—The number of source IP-based connections exceeds
the upper limit.
too many source IP sessions—The number of destination IP-based connections
exceeds the upper limit.
Source Zone
Source zone of the connection.
Source IP
Source IP address of the connection.
Destination Zone
Destination zone of the connection.
Destination IP
Destination IP address of the connection.
Current Rate
Rate of the current connection.
Current Connection
Total number of the current connections.
TCP Percentage
Percentage of TCP packets to the total packets.
UDP Percentage
Percentage of UDP packets to the total packets.
ICMP Percentage
Percentage of ICMP packets to the total packets.
Displaying attack prevention logs
Select Log Report > Report > Attack Prevention Log from the navigation tree to enter the page as shown
in
describes the configuration items.
