Panning, Lgorithm, Ecurity – Weidmuller WI-MOD-945-E: 900Mhz Wireless Ethernet & Device Server v2.16 User Manual
Page 33: Spanning tree algorithm, 5 - spanning tree algorithm, 6 - security menu
Weidmuller Wireless Ethernet Modem & Device Server WI-MOD-945-E User Manual
Page 33
www.weidmuller.com
Rev 2.136
3.5 - Spanning Tree Algorithm
The bridge “Spanning Tree Protocol” function was introduced to
handle network loops and provide redundant paths in networks. To
enable tick the STP box on any “WDS Connections” you have
configured on the “Repeaters” configuration page.
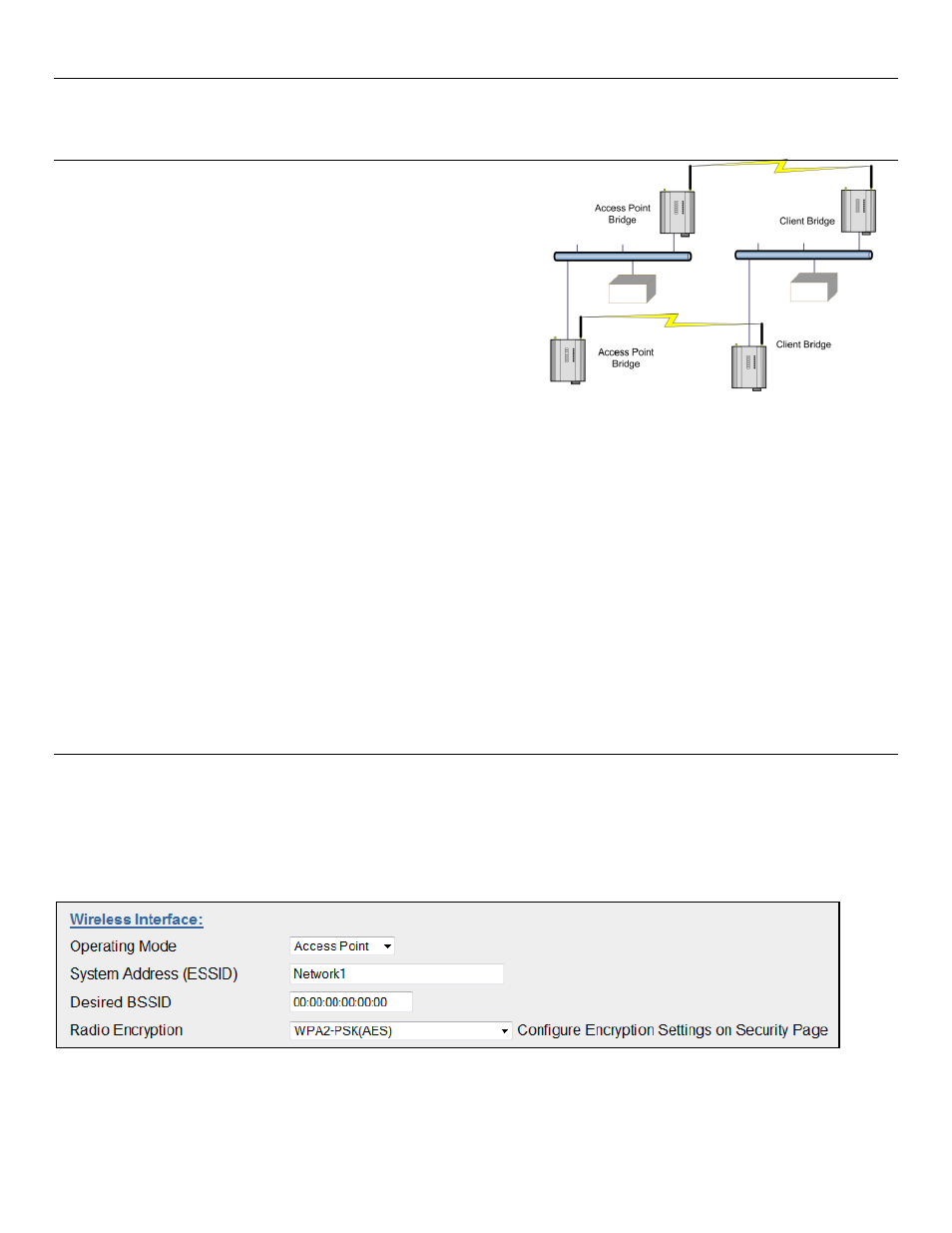
For example, consider this network with a redundant wireless link. If
the bridge Spanning Tree Protocol is enabled, one of the two wireless
links will be disabled - that is, all wireless data will be transferred by
one link only. If the active link fails, the other link will automatically
start transferring the wireless data.
The Spanning Tree Protocol implemented is IEEE 802.1d compatible. The algorithm forms a loop-free network by
blocking traffic between redundant links in the network. These blocked links are placed in a standby condition, and may
be automatically enabled to repair the network if another link is lost. The Spanning Tree Algorithm maintains a single path
between all nodes in a network, by forming a tree-like structure. The Bridge Priority determines where the node sits in the
tree. A Bridge configured with the lowest priority (0) will become the root node in the network, and will direct traffic
between each of its branches. The root node is typically the unit that handles the majority of traffic in the network. The
WI-MOD-945-E is configured with a Bridge Priority of 32768 by default. The intention is to reduce traffic that the WI-MOD-
945-E must handle, by placing it at the branch level in the network tree. As a branch, the WI-MOD-945-E needs only pass
traffic to devices that are its “leaves”.
There is some overhead in maintaining a network utilizing the Spanning Tree Algorithm. Users wishing to increase their
throughput, at the expense of redundancy should disable Spanning Tree. The Spanning Tree Protocol can be configured
on the Repeaters configuration page.
3.6 - Security Menu
Select the Radio Encryption level from the drop down menu on the Main index page and
then press the “Save Changes”
button. T
he default setting is “None”.
Available encryption levels are -
“None”, “WEP (64-bit)”, “WEP (128-bit)”, “WPA-PSK (TKIP)”, “WPA-PSK (AES)”,
“WPA2-PSK (AES)”, “WPA-PSK/ WPA2-PSK” (Legacy) & WPA-Enterprise.
Security Menu
Figure 17 - Spanning Tree Protocol
