2 smart card removal behavior, Smart card removal behavior, Smart card removal behavior 4.2 – HID Crescendo Integration User Manual
Page 42
Crescendo Integration Guide
47A3-905, A.1
Microsoft Windows Server 2003
Page 42 of 54
© 2008 HID Global Corporation. All rights reserved
December 1, 2008
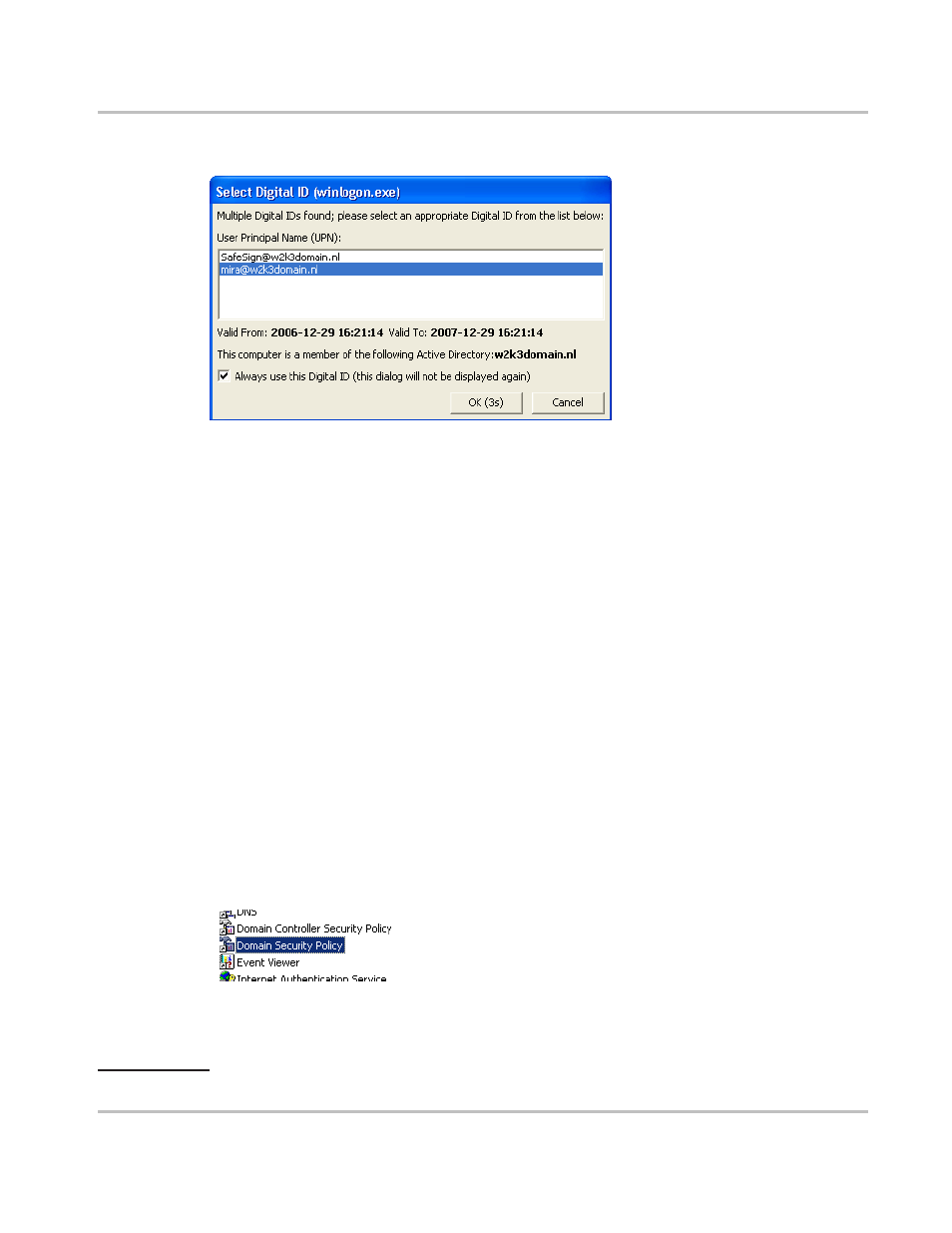
Select ‘Always use this Digital ID’. The dialog appears at log on, and within a 5 second counter the login
proceeds with the selected certificate:
Figure 46:Select digital id (winlogon.exe): Always use this digital id
This functionality has been included to allow users to be aware if their token contains multiple Digital IDs for
log on (should they want to switch at a given time). This counter can be configured in the registry
6
.
Smart Card Removal Behavior
4.2
For security reasons, enable smart card removal behavior. This means when a user removes their token from the
smart card reader, a pre-defined policy is activated within that domain.
Smart card removal behavior is defined by a security policy. This policy determines what happens when the token for
a logged on user is removed from the smart card reader. The options are:
No Action
•
Lock Workstation: the workstation is locked when the token is removed
•
Force Logoff: the user is automatically logged off when the token is removed
•
If Lock Workstation is specified, then the workstation is locked when the token is removed, thereby allowing users to
leave their workplace and take their token with them, while still maintaining a protected session. This policy setting is
described below.
Configuration of Smart Card Removal Behavior
4.2.1
Smart card removal behavior is configured on the Domain Controller. In order to configure the smart card removal
behavior for your domain, go to the
domain Security policy settings. For instance, configure all computers in the
domain, in addition to the Domain Controller
7
.
To open the
domain Security policy settings, go to
Start > Settings > Control Panel > Administrative Tools:
Figure 47: domain Security policy
6 In order to enable and configure this functionality, you need sufficient administration rights to edit the registry.
7 Do not confuse this with the Domain Controller Security Policy settings, where you configure the Security Policy for the Domain Controller.
