Idm usage strategies, Idm usage strategies -4 – HP Identity Driven Manager Software Licenses User Manual
Page 26
2-4
Getting Started
Before You Begin
5.
Create the Access Profiles, to set the VLAN, QoS, rate-limits (bandwidth)
attributes, and the network resources that are available, to users in an
Access Policy Group. (See page 3-24)
6.
Create an Access Policy Group, with rules containing the Location, Time,
System, and Access Profile that is applied to users when they login. (See
page 3-34)
OR
If using Active Directory synchronization, add rules and Access Profiles
to the Access Policy Groups automatically created by Active Directory
synchronization.
7.
If Active Directory synchronization is not used, assign Users to the
appropriate Access Policy Group. (See page 3-41).
8.
If automatic deployment is disabled, deploy the configuration policies to
the IDM Agent on the RADIUS server. (See page 3-46)
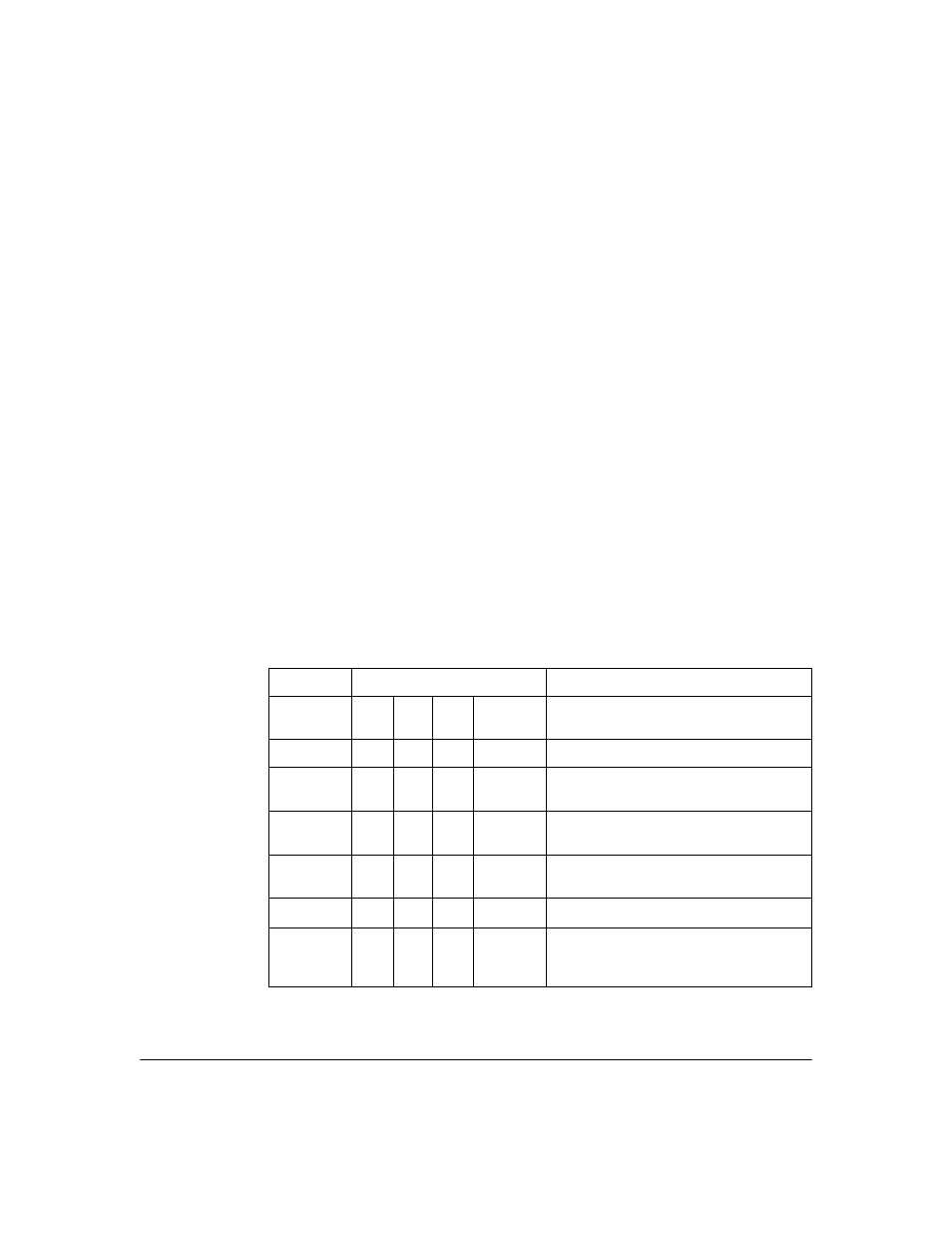
IDM Usage Strategies
You can use IDM to simply monitor user activity on the network, or to apply
user authentication rules to improve network security and performance. The
following table identifies the IDM configuration for various deployment and
usage strategies for IDM.
Table 2-1: IDM Deployment and Usage Strategies
Authenticate
Authorize
Strategy Description
VLAN
QoS
Rate-
Limit
Network
Resources
Monitor and report user activity.
x
Enhance normal RADIUS authentication with
Location, Time, and System rules
x
x
Provide rudimentary VLAN segregation
(Unknown Users, Guests, Visitors, Contractors)
x
x
Provide complete VLAN placement for all
Users
x
x
x
Provide QoS and Rate-limits per User
x
x
x
x
x
VLAN, QoS, and Rate-limit attributes, and
accessibility of defined Network Resources for
all users, based on Location, Time, and System
