Network number and lockout key – Clear-Com Tempest900 User Manual
Page 37
31
Tempest®900 2-Channel Wireless Intercom System
Network Number and Lockout Key
The
Network Number
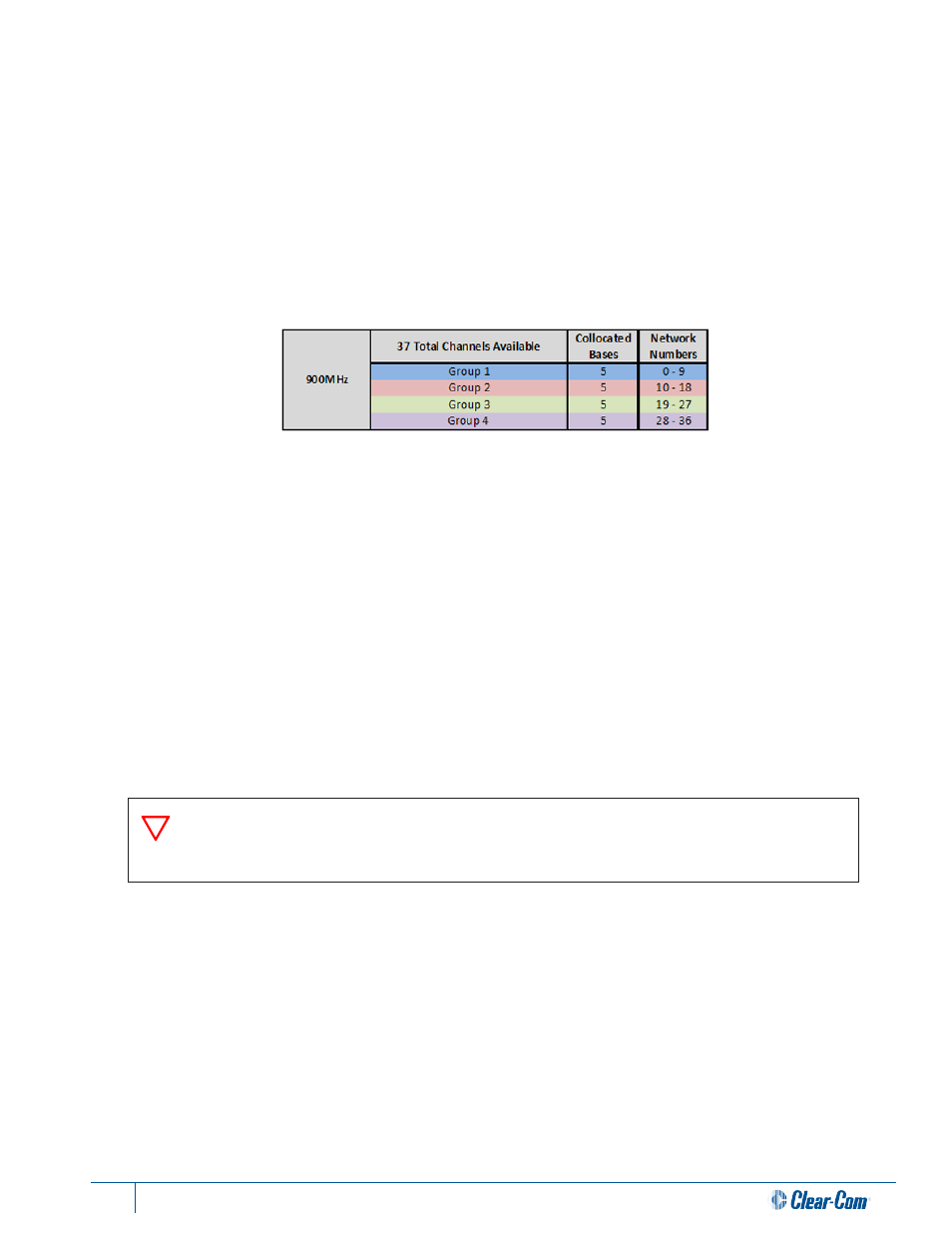
determines the RF frequency hopping pattern for the BaseStation and its corresponding BeltStations.
This is a key operational parameter and is represented by a number between 0 and 36.
When using multiple collocated Tempest BaseStations, it is imperative that Network Numbers are properly coordinated.
BaseStations that are synchronized together must utilize the same Network Number Group for optimal performance to be
acheived. Up to 5 Tempest 900 BaseStations can be utilized in one Network Number Group under ideal conditions. For
example, a configuration using 5 Tempest 900 BaseStations would assign each BaseStation a Network Number (0,1,2,3,4)
from Group 1. The chart below outlines each Network Number Group and it’s capacity.
The
Lockout Key
prevents systems with the same Network Number from trying to communicate with each other and is
represented by a number between 0 and 255. BaseStations that are collocated within the same installation may have
the same Lockout Key as long as the Network Numbers are different. Lockout keys serve as differentiators for systems
using the same Network Number. Together, the Network Number and Lockout Key represent more than 11,000 possible
combinations to minimize the possibility of inter-system interference.
The Network Numbers and Lockout Keys for Tempest Wireless BaseStations are set to a factory default before leaving the
factory. It is always recommended to adjust the Network Number and Lockout Key upon initial set up out of the box. Failure
to set a unique Network Number and Lockout Key may result in poor system performance caused by interference from
another Tempest Wireless system using the same Network Number and Lockout Key. Because of the requirement to pair
every BeltStation to each BaseStation that it will communicate with, it is not possible to manipulate Network Numbers and
Lockout Keys at a BeltStation to gain unauthorized access to a communication channel
Collocated BaseStations must use Network Numbers from the same Network Number Group;
failure to do so can lead to poor performance.
