TANDBERG Gatekeeper User Manual
Page 35
TANDBERG Gatekeeper User Guide
Page 35 of 105
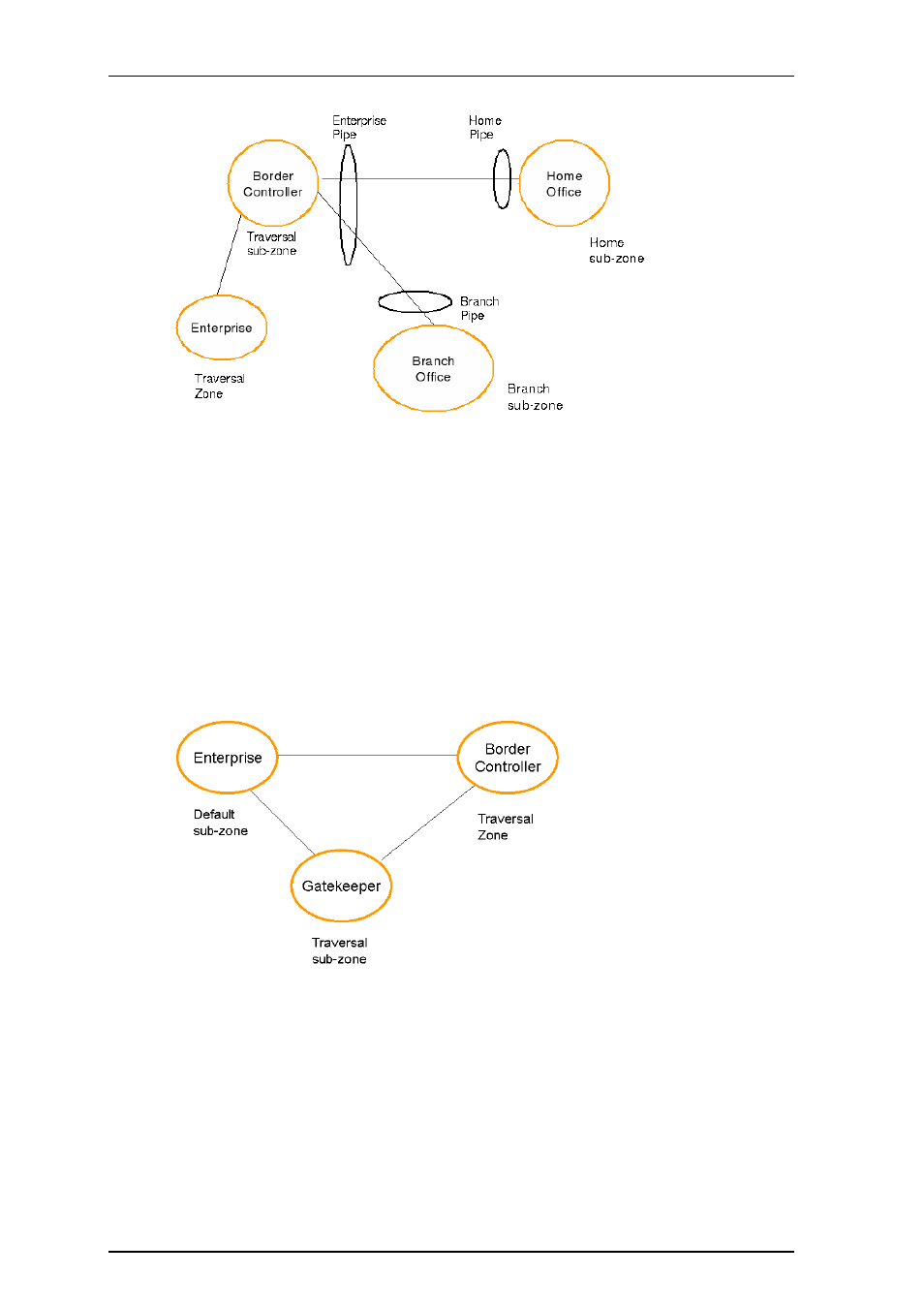
Figure 15: Border Controller example configuration
Figure 15 shows how the Border Controller could be configured for the deployment in Figure 14. The
introduction of the firewalls means that there is no longer any direct connectivity between the Branch
and Home offices. All traffic must be routed through the Border Controller. This is shown by the absence
of a link between the Home and Branch subzones.
The Traversal Zone in Figure 15 represents the Enterprise Gatekeeper. The Border Controller will
consume bandwidth from the Traversal Zone for all calls placed to endpoints managed by the Enterprise
Gatekeeper. In this example we have assumed that there is no bottleneck on the link between the
Border Controller and the Enterprise network, so have not placed a pipe on this link. If you want to limit
the amount of traffic flowing through your firewall, you could provision a pipe on this link.
The traversal subzone in Figure 15 may be used to control the amount of traffic flowing through the
Border Controller itself.
Because the Gatekeeper is only managing endpoints on the LAN, its configuration is simpler as shown in
Figure 16: Gatekeeper example configuration
All of the endpoints in the enterprise will be assigned to the default subzone. The Traversal subzone
controls traversal traffic flowing through the Gatekeeper, whilst the Traversal Zone controls all traffic
traversing the enterprise firewall and passing on to the Border Controller. Both subzones and the
Traversal zone are linked: the link between the default subzone and the Traversal zone is used by
endpoints which can send media directly to the Border Controller. The other two links are used by
endpoints using the Gatekeeper to traverse the firewall.
The Gatekeeper is shipped with Default and Traversal Zones and Default and Traversal subzones
already configured. They are also preconfigured with the links between these zones to allow calls to be
placed. You may delete or amend the default links if you need to model restrictions of your network. The
default links may be restored by running the command:
xCommand DefaultLinksAdd
