Netopia 3300 User Manual
Page 134
5-2 Firmware User Guide
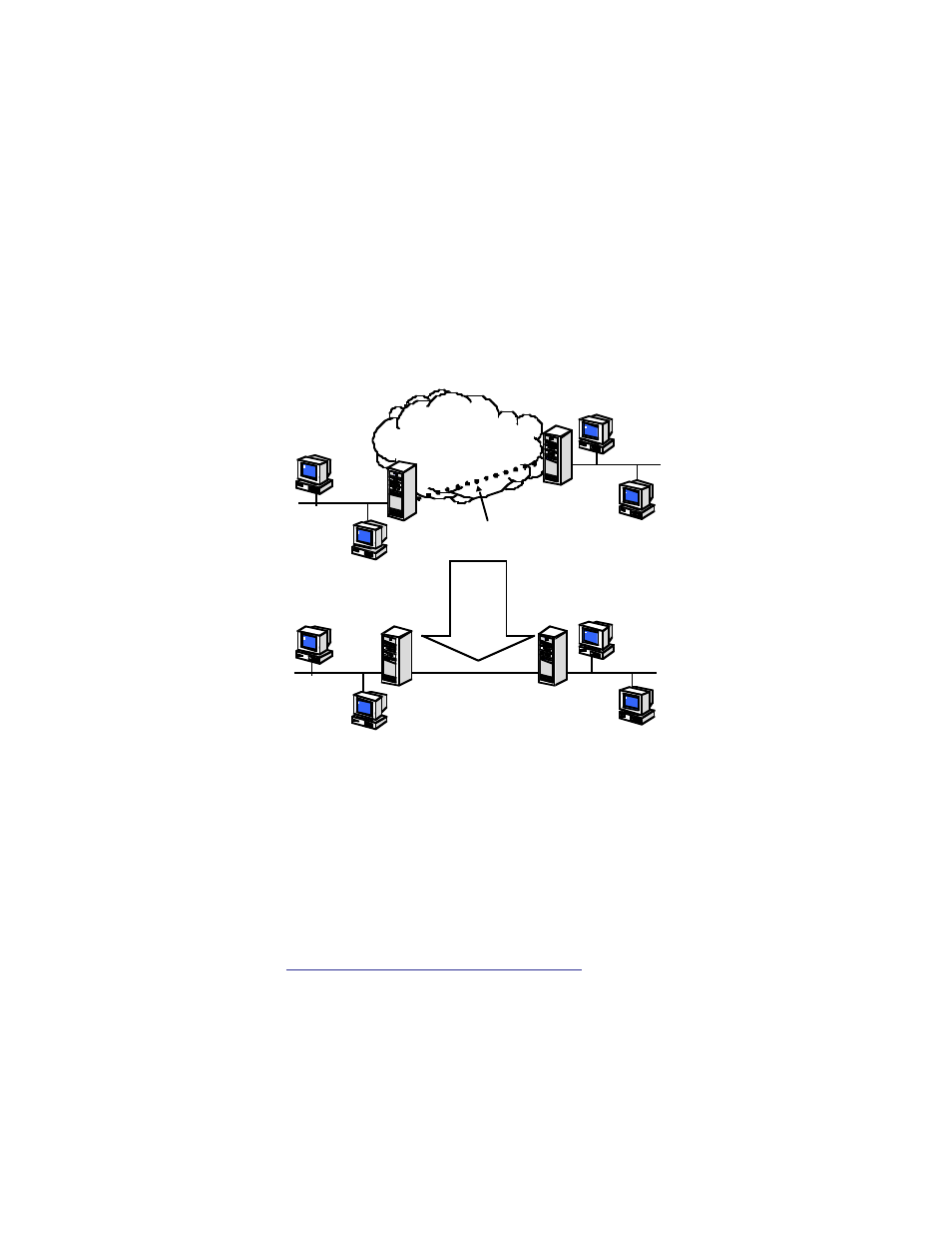
Netopia Firmware Version 8.7 can be used in VPNs either to initiate the connection or to answer it. When used
in this way, the Routers are said to be tunnelling through the public network (Internet). The advantages are that,
like your long distance phone call, you don't need a direct line between one computer or LAN and the other, but
use the local connections, making it much cheaper; and the information you exchange through your tunnel is
private and secure.
Tunneling is a process of creating a private path between a remote user or private network and another private
network over some intermediate network, such as the IP-based Internet. A VPN allows remote offices or
employees access to your internal business LAN through means of encr yption allowing the use of the public
Internet to look “vir tually” like a private secure network. When two networks communicate with each other
through a network based on the Internet Protocol, they are said to be tunneling through the IP network.
Unlike the phone company, private and public computer networks can use more than one protocol to carr y your
information over the wires. Several such protocols are in common use for tunnelling, Point-to-Point Tunnelling
Protocol (PPTP), IP Security (IPsec), Layer 2 Transpor t Protocol (L2TP), Generic Routing Encapsulation (GRE),
and Ascend Tunnel Management Protocol (ATMP). The Netopia Router can use any of these.
•
Point-to-Point Tunneling Protocol (PPTP) is an extension of Point-to-Point Protocol (PPP) and uses a client
and ser ver model. Netopia’s PPTP implementation is compatible with Microsoft’s and can function as
either the client (PAC) or the ser ver (PNS). As a client, a Netopia Router can provide all users on a LAN with
secure access over the Internet to the resources of another LAN by setting up a tunnel with a Windows NT
ser ver running Remote Access Ser vices (RAS) or with another Netopia Router. As a ser ver, a Netopia
Netopia Router can provide remote users a secure connection to the resources of the LAN over a dial-up,
cable, DSL, or any other type of Internet access. Because PPTP can create a VPN tunnel using the Dial-Up
Networking (DUN) (see
"Dial-Up Networking for VPN" on page 5-21)
utility built into Windows 95, 98, or NT,
no additional client software is required.
•
IPsec stands for IP Security, a set of protocols that suppor ts secure exchange of IP packets at the IP layer.
IPsec is deployed widely to implement Vir tual Private Networks (VPNs). IPsec suppor ts two encr yption
modes: Transpor t and Tunnel. Transpor t mode encr ypts only the data por tion (payload) of each packet, but
Transit Internetwork
Logical
Equivalent
Virtual Private Network
