5 conclusion, Remote access protection – IBM Tivoli and Cisco User Manual
Page 92
74
Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
Remote access protection
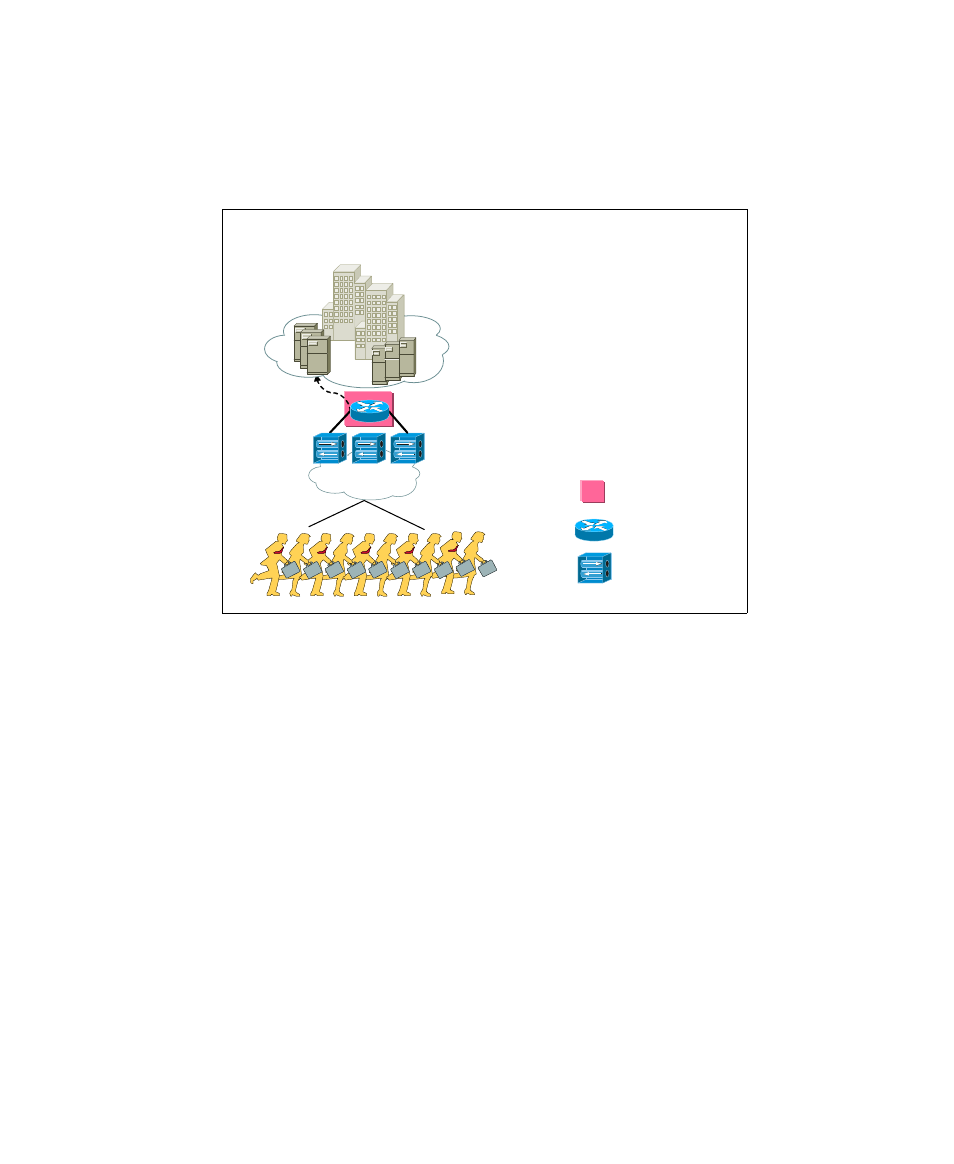
Remote access users use dial-up or VPN to connect to corporate resources. To
enforce these users to comply to the corporate policies, a policy enforcement
device may be deployed at the remote access entry points (Figure 3-16).
Figure 3-16 Remote access protection
The policy enforcement points can vary, depending on which section of the
enterprise the organization would like to enforce compliance. The physical
locations of posture enforcement points depend on the organization’s network
and security architecture.
3.5 Conclusion
The IBM Integrated Security Solution for Cisco Networks is an integration of
products from IBM and Cisco. New components have been added to each of the
individual product sets so they can work in unison. The components in this
chapter have been described with integration being the prime objective. Some of
the components can perform other functions not mentioned here. This chapter
has dealt with the various logical and physical components that make up the IBM
Integrated Security Solution for Cisco Networks. A logical data flow has been
provided to show how the various components communicate and deliver the
desired result of policy compliance validation and remediation.
Mobile
Users
Internet
Legacy VPN
Concentrators
AAA
AAA
Corporate
Network
AAA
Posture Enforcement
Points
Remote Access Protection
Router
VPN
Concentrator
