IBM Tivoli and Cisco User Manual
Page 245
Chapter 7. Network enforcement subsystem implementation
227
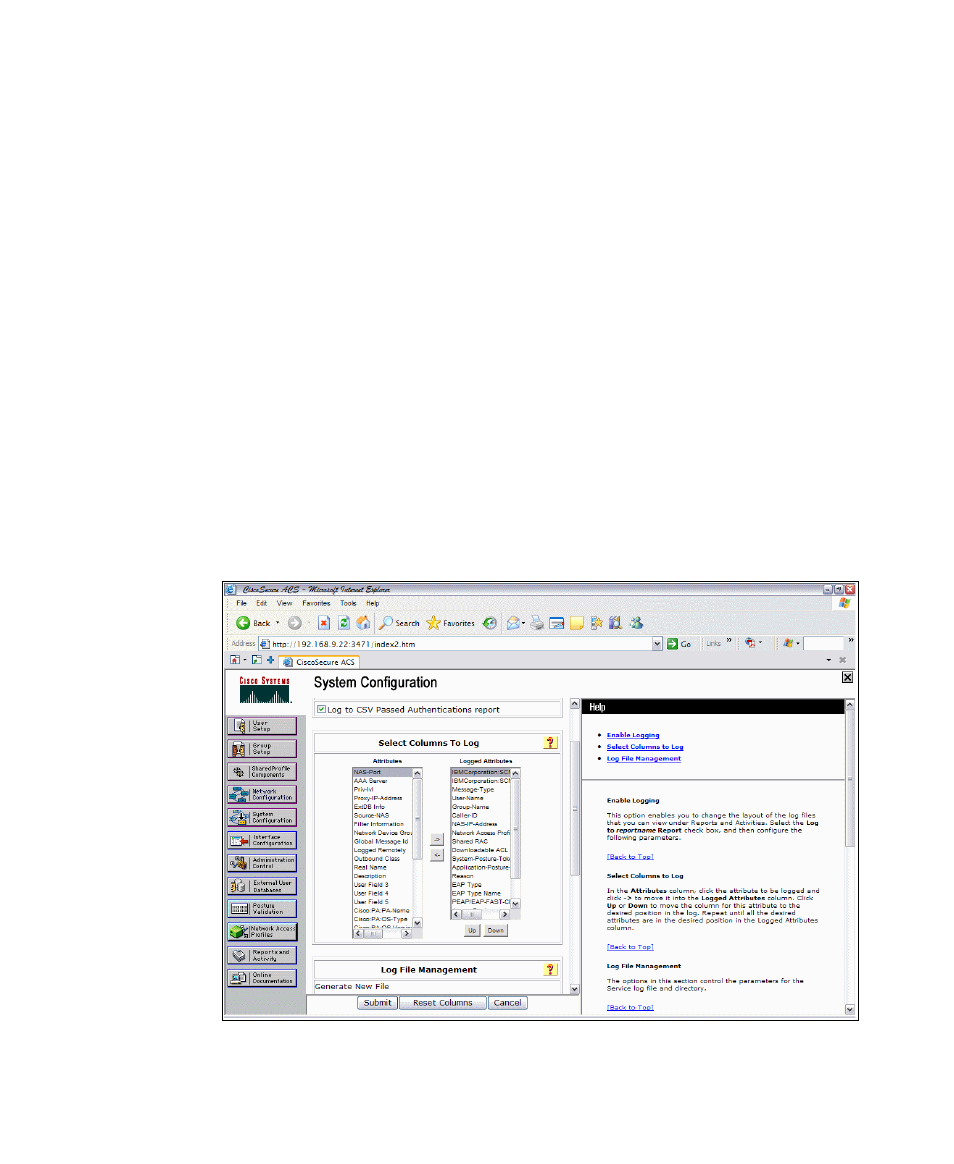
that you wish to include in the log file. Scroll down and change the file
management settings if desired.
We recommend that you include the following fields in Logged Attribute:
– Network Access Profile Name
– Shared RAC
– Application Posture Token
– System Posture Token
– Reason
These should be moved toward the top of the list of installed attributes for
easy access. This makes writing policy rules and troubleshooting much
easier. The
NAS-IP-Address
and
User Name
fields also provide valuable
information during troubleshooting.
All client instances successfully completing the posture validation process are
logged in the passed authentications log even if the client has posture
validated into a state other than Healthy. The failed authentication attempts
log contains entries for clients failing to complete the posture validation
process.
When you are finished, click Submit.
5. Select CSV Failed Authentications (Figure 7-10).
Figure 7-10 Passed authentication logging
