2 configuration of the compliance policies – IBM Tivoli and Cisco User Manual
Page 170
152
Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
14.The installation itself is very fast, but the database creation process may take
a while. You may see the black command line window popping up listing the
DB2 command execution results.
Do not
close this window. When the
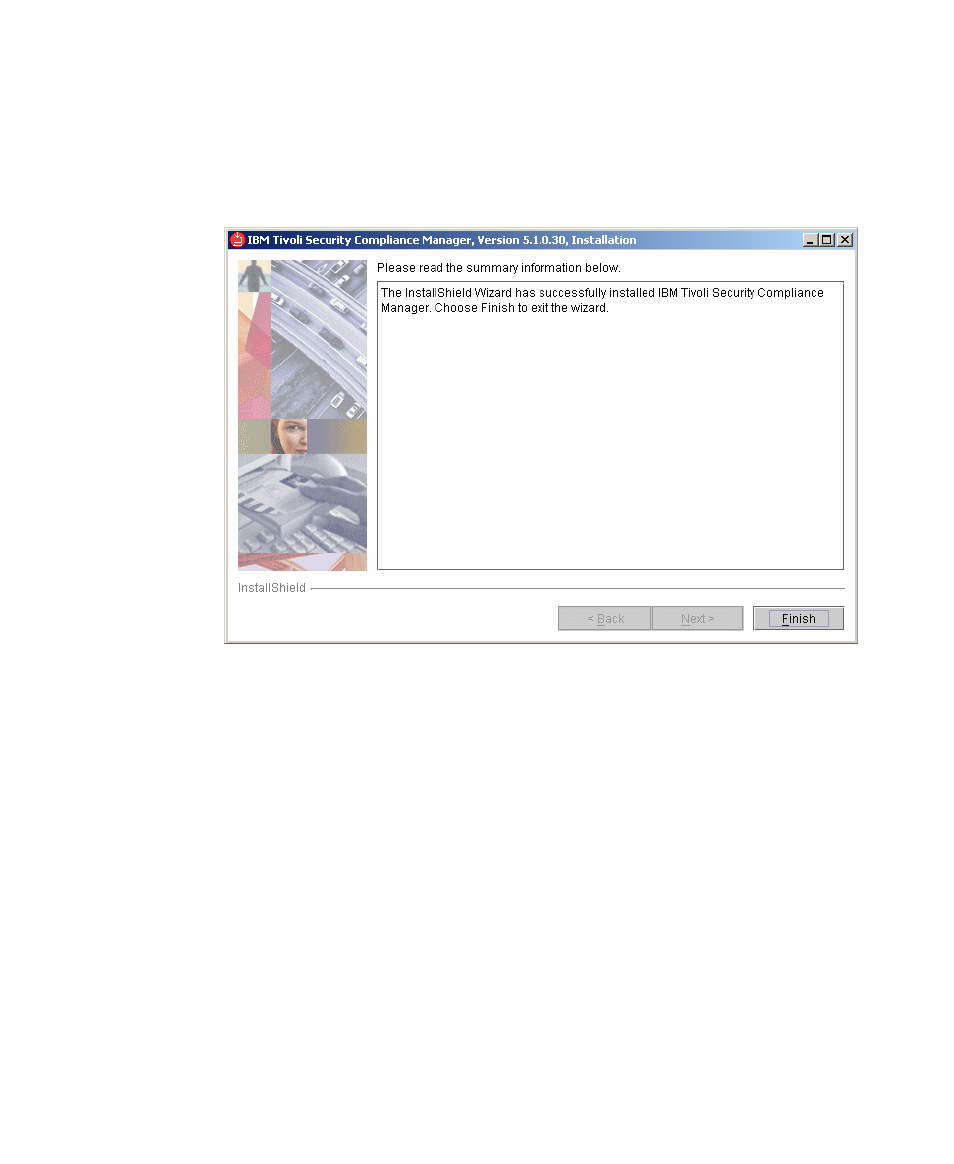
installation process is finished the last window is displayed, as shown in
Figure 6-27. Click Finish to close the installation wizard.
Figure 6-27 Installation result window
This concludes the Tivoli Security Compliance Manager server installation. You
may proceed with the next components.
6.2 Configuration of the compliance policies
Since we have a Security Compliance Manager up and running we must set up
the correct compliance policies to check for violations. For the purpose of this
book we selected the following policies to be implemented and enforced:
The antivirus software must be installed on the client workstation in the
correct version, and it must be up-to-date with the virus signatures file and
running. As an example we are using Symantec Antivirus software, but the
solution can include rules for different antivirus software as well.
