Less secure more secure, Figure 3-8 security zones, Internet – IBM Tivoli and Cisco User Manual
Page 82: Dmz intranet production network management network
64
Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
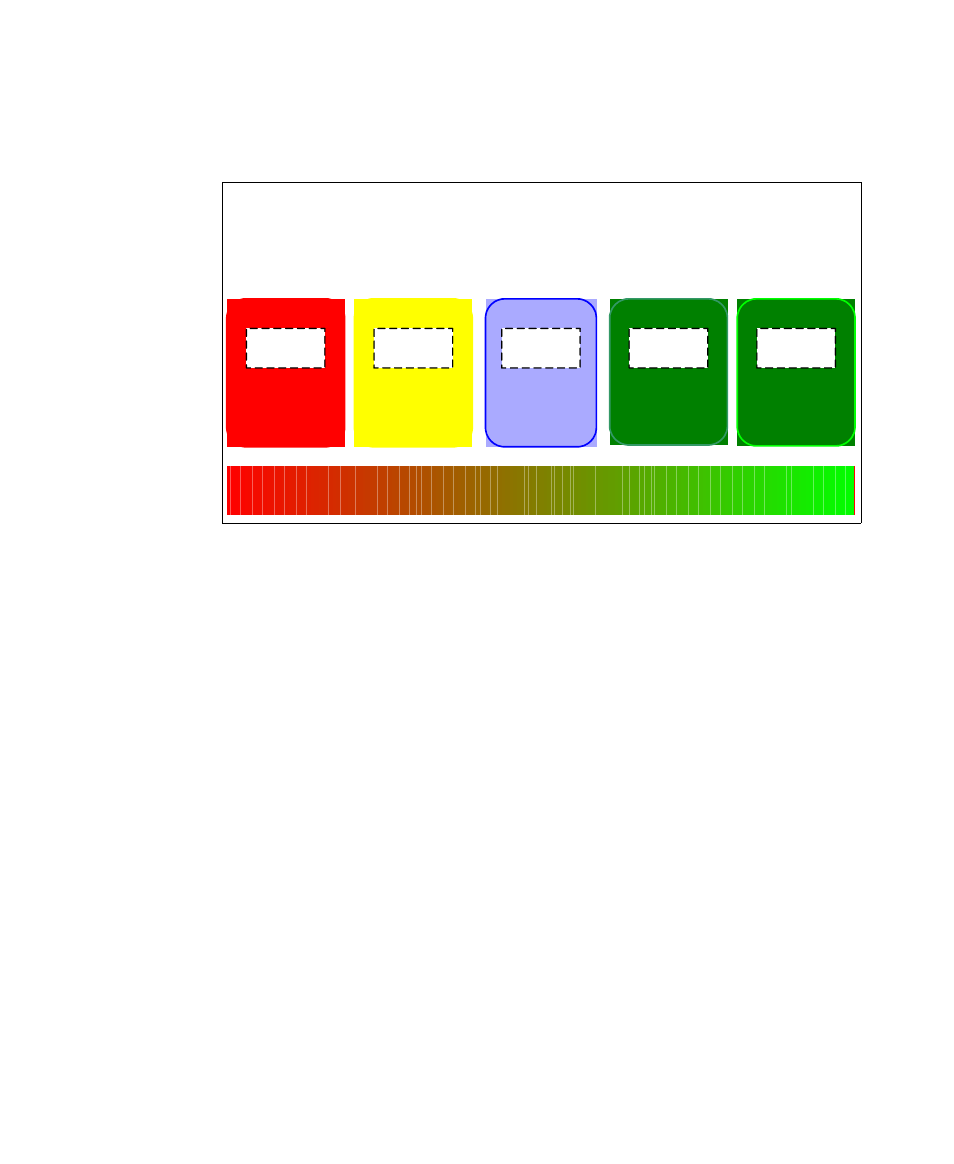
Figure 3-8 shows the security zones and their classifications. Organizations
could have different topologies and have their own architecture and naming of
zones depending on their security policy.
Figure 3-8 Security zones
For more about the MASS architecture methodology, refer to the IBM Redbook
Enterprise Security Architecture Using IBM Tivoli Security Solutions,
SG24-6014.
Enterprise security has to meet many stringent requirements, one of them being
compliance. Maintaining and enforcing client compliance can be a tedious
process that consumes time and resources because:
The number of clients can be large.
Clients are physically dispersed and use different access methods to access
enterprise resources.
Not all clients accessing the network are owned by the enterprise (for
example, partners and contractors).
The IBM Integrated Security Solution for Cisco Networks addresses network
clients’ compliance to policies that are centrally defined by the enterprise. The
solution can enforce client compliance and help remediate compliance violations.
Hence it is important to understand network clients, their access methods, and
how this solution can effectively meet the end result of client compliance.
Network client machines represent the users of corporate resources. Clients
access these resources using various access methods such as LAN, wireless,
WAN, and Internet access. Clients using these access methods mostly enter the
Internet
Less Secure More Secure
DMZ
Intranet
Production
Network
Management
Network
Uncontrolled
Zone
Controlled
Zone
Controlled
Zone
Restricted
Zone
Restricted
Zone
Business Partner
Connections
VPN termination
Trusted Internal
Network
Organizations may
set up specialized
restricted zones for
production systems
Which would have
Application &
Database systems
Some organizations
may set up special
networks to
separate various
management
components from
production systems.
Untrusted
External network
like Internet
