Internet, Chapter 2. architecting the solution, Figure 2-5 nac deployment scenario – IBM Tivoli and Cisco User Manual
Page 45
Chapter 2. Architecting the solution
27
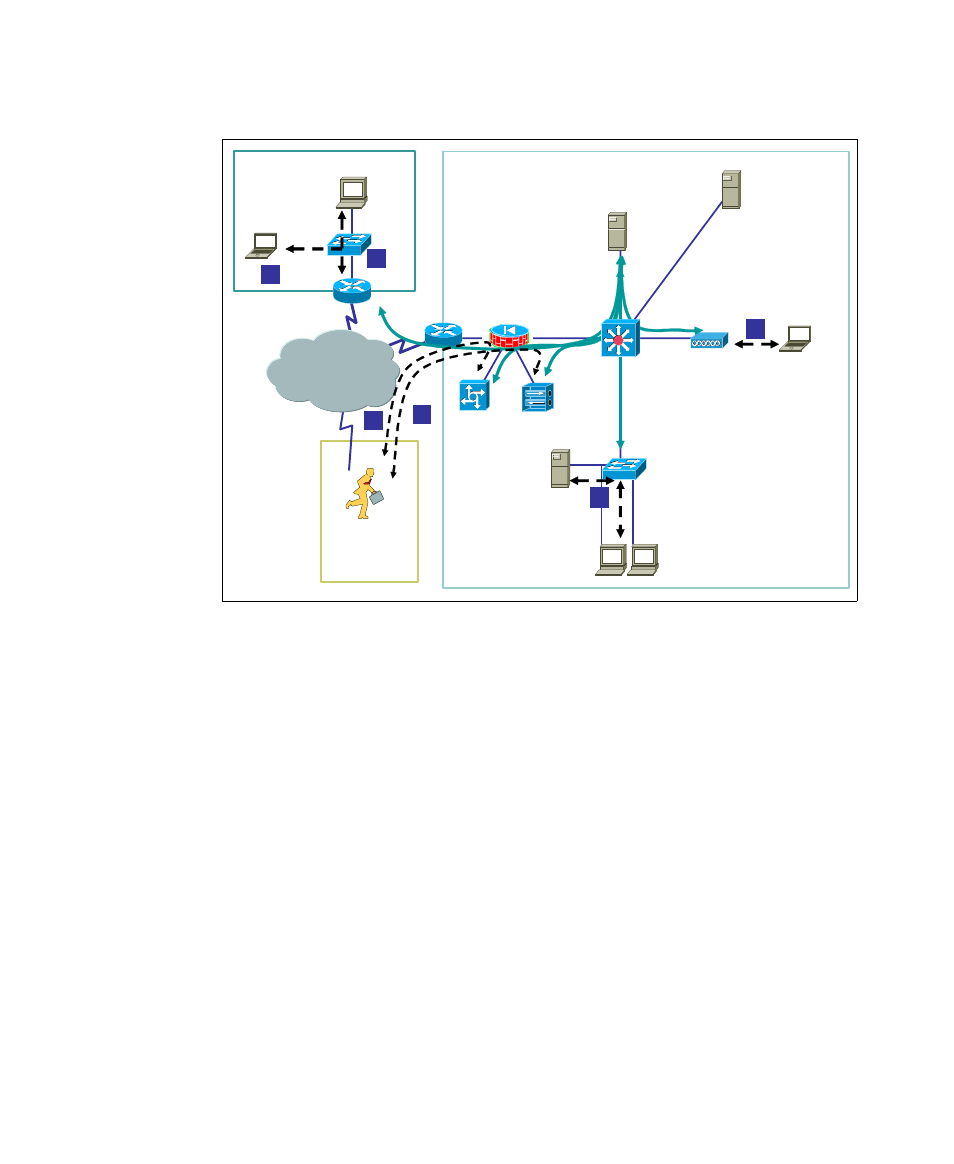
Figure 2-5 illustrates a possible NAC deployment scenario.
Figure 2-5 NAC deployment scenario
Typical candidates for NAC protection are networks (both wireless and wired)
used by the mobile users to connect to the intranet while visiting the office [1], as
well as the dial-up and VPN networks used to connect remotely [2,3]. (Especially
in a dial-up and VPN environment, NAC enables posture control of the users
(clients) connecting to the intranet where the other methods of enforcing
compliance are limited.) In the next step, all branch office networks [4] can be
protected with NAC. Finally, the solution can be extended to cover all wireless
networks [5] and the stationary networks in the main campus [6].
A second factor strongly influencing project scope is the availability of automated
remediation. As the number of quarantined clients increases, the number of help
desk calls grows, raising the total cost of ownership (TCO) for the solution.
Corporate
Network
Branch Office
Internet
Mobile
Users
Dial-in
NAS
RA IPsec
VPN
Campus FW
Edge Router
SCM
Server
AAA Server (ACS)
Branch
Router
RADIUS
(posture)
EAP/UDP
4
4
2
EAP/UDP
1
EAP 802.1x
(wireless)
3
5
EAP 802.1x (wired)
6
