Infrastructure requirements – Fortinet FORTIOS V3.0 MR7 User Manual
Page 18
FortiOS v3.0 MR7 SSL VPN User Guide
18
01-30007-0348-20080718
Topology
Configuring a FortiGate SSL VPN
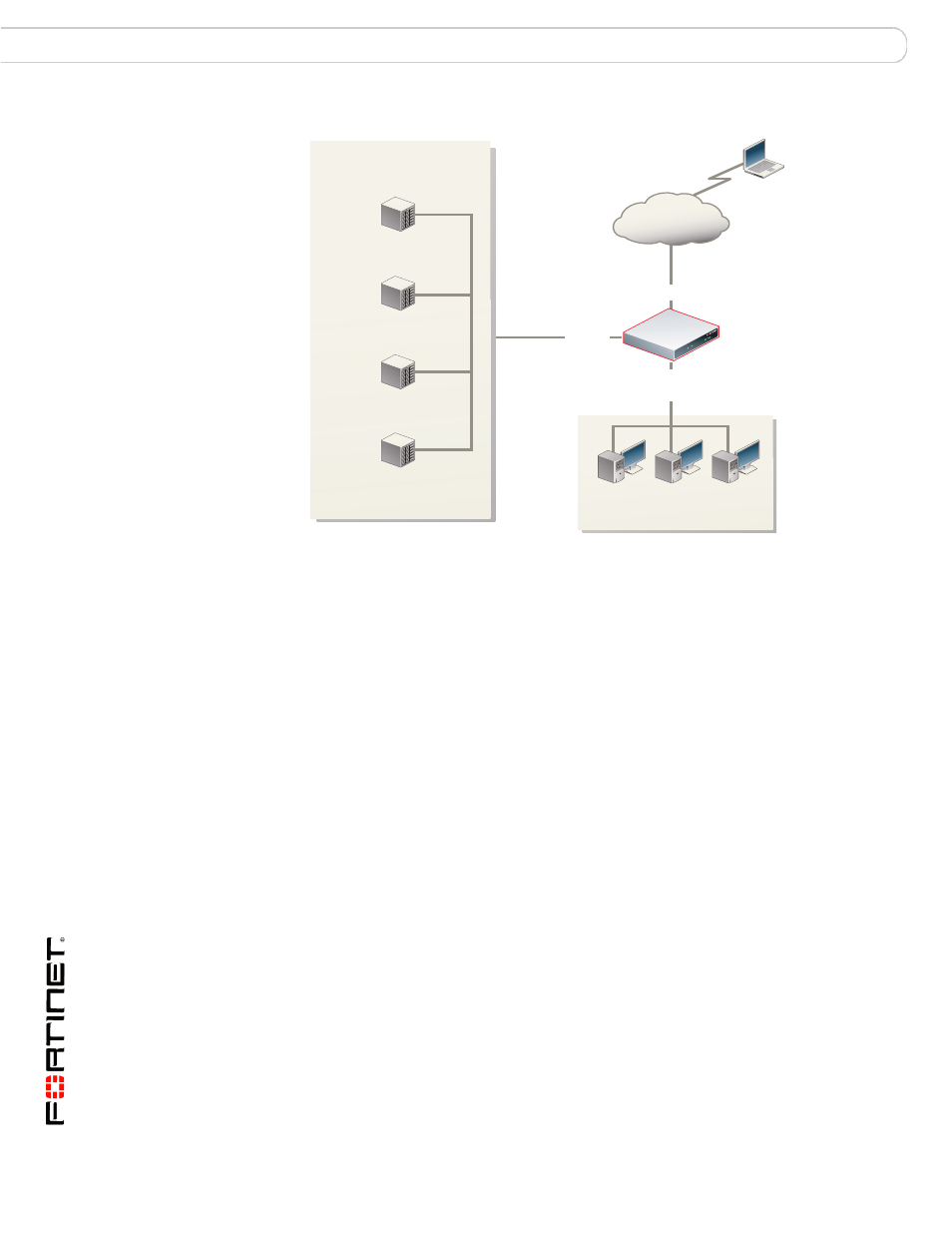
Figure 1: Example SSL VPN configuration
To provide remote clients with access to all of the servers on Subnet_1 from the
Internet, you would configure FortiGate_1 as follows:
•
Create an SSL VPN user group and include the remote users in the user
group. When you create the user group, you also specify whether the users
may access the web portal in web-only mode or tunnel mode.
•
For tunnel-mode users, define the virtual IP addresses that the FortiGate unit
is to assign to remote clients when they connect.
•
Create a firewall destination IP address of 172.16.10.0/24.
•
Create a firewall policy to allow the SSL VPN user group members to connect
to Subnet_1 through the VPN. For more information, see
.
If your user community needs access to Subnet_2, you would create a second
firewall destination IP address of 192.168.22.0/24 and create a second
firewall policy that binds the associated remote clients to the Subnet_2 destination
address.
Infrastructure requirements
•
The FortiGate unit must be operating in NAT/Route mode and have a static
public IP address.
•
The ISP assigns IP addresses to remote clients before they connect to the
FortiGate unit.
•
If the remote clients need web-only mode access, see
•
If the remote clients need tunnel-mode access, see
Subnet_2
192.168.22.0/24
internal
192.168.22.1
Subnet_1
172.16.10.0/24
HTTP/HTTPS
172.16.10.2
Telnet
172.16.10.3
FTP
172.16.10.4
SMB/CIFS
172.16.10.5
Internet
FortiGate_1
wan1
dmz
172.16.10.1
Remote client
