ATL Telecom AM2 User Manual
Page 50
ATL User Guide
AM2 G.SHDSL Modem
50
A ping of death attack attempts to crash your system by sending a fragmented packet, which when
reconstructed is larger than the maximum allowable size. Other known variants of the ping of death include
teardrop, bonk and nestea.
A land attack is an attempt to slow your network down by sending a packet with identical source and
destination addresses originating from your network.
IP Spoofing is a method of masking the identity of an intrusion by making it appeared that the traffic came
from a different computer. This is used by intruders to keep their anonymity and can be used in a Denial of
Service attack.
A smurf attack involves two systems. The attacker sends a packet containing a ICMP echo request (ping) to
the network address of one system. This system is known as the amplifier. The return address of the ping has
been faked (spoofed) to appear to come from a machine on another network (the victim). The victim is then
flooded with responses to the ping. As many responses are generated for only one attack, the attacker is able
use many amplifiers on the same victim.
IP Spoofing: Falsify the IP header information to deceive the destination host.
Traditional firewalls are stateless meaning they have no memory of the connections of data or packets that
pass through them. Such IP filtering firewalls simply examine header information in each packet and attempt
to match it to a set of defined rules. If the firewall finds a match, the prescribed action is taken. If no match
is found, the packet is accepted into the network, or dropped, depending on the firewall configuration.
A stateful firewall maintains a memory of each connection and data passing through it. Stateful firewalls
record the context of connections during each session, continuously updating state information in dynamic
tables. With this information, stateful firewalls inspect each connection traversing each interface of the
firewall, testing the validity of data packets throughout each session. As data arrives, it is checked against the
state tables and if the data is part of the session, it is accepted. Stateful firewalls enable a more intelligent,
flexible and robust approach to network security, while defeating most intrusion methods that exploit state-
less IP filtering firewalls.
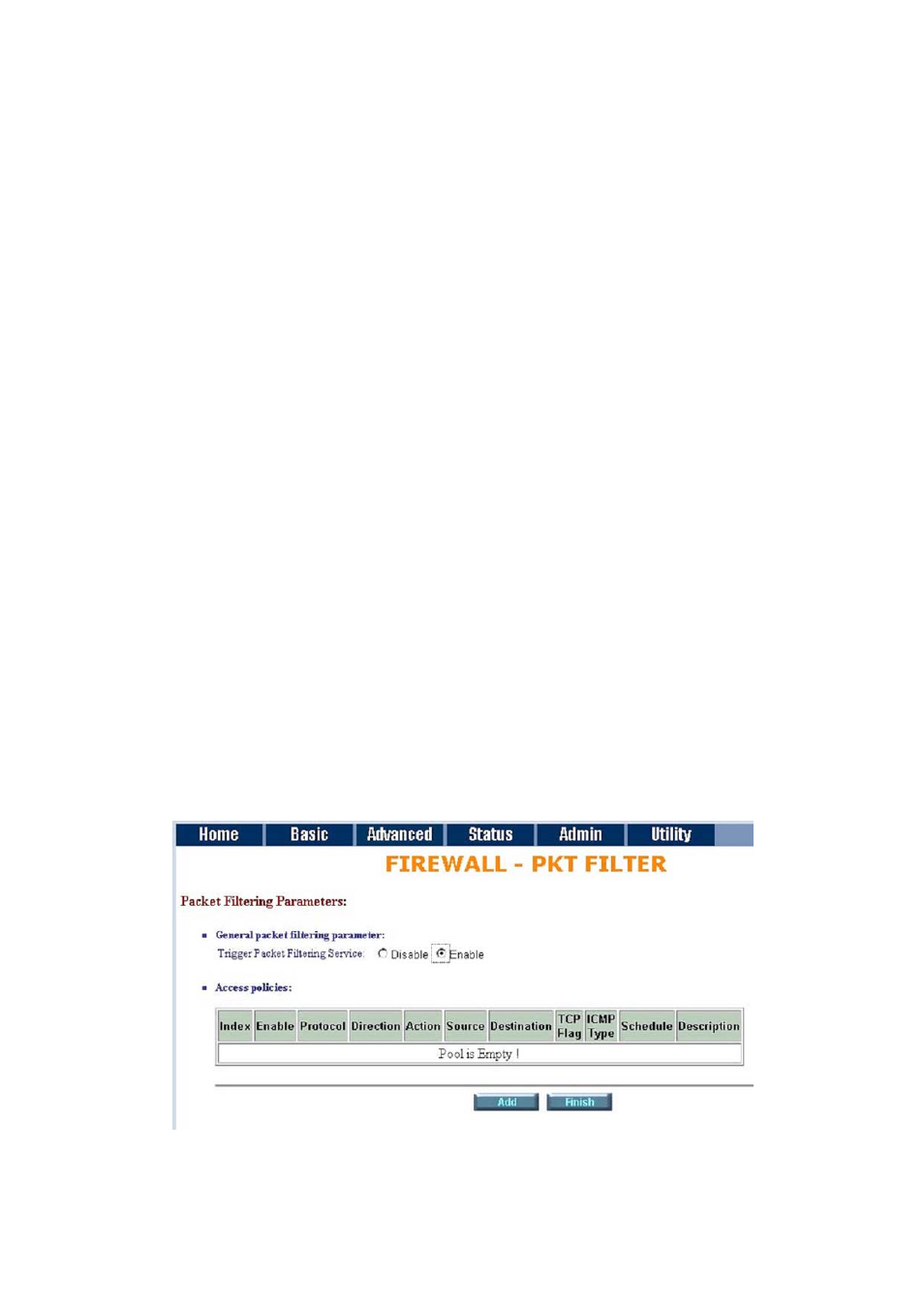
If you want to configure the Packet Filtering Parameters, choose Enable and press Add.
Select the protocol and configure the parameter.
