Scenario 2: gateway-to-gateway with certificates, Internet – Enterasys Networks Security Router X-PeditionTM User Manual
Page 371
Interoperability Profile for the XSR
XSR User’s Guide 14-49
Scenario 2: Gateway-to-Gateway with Certificates
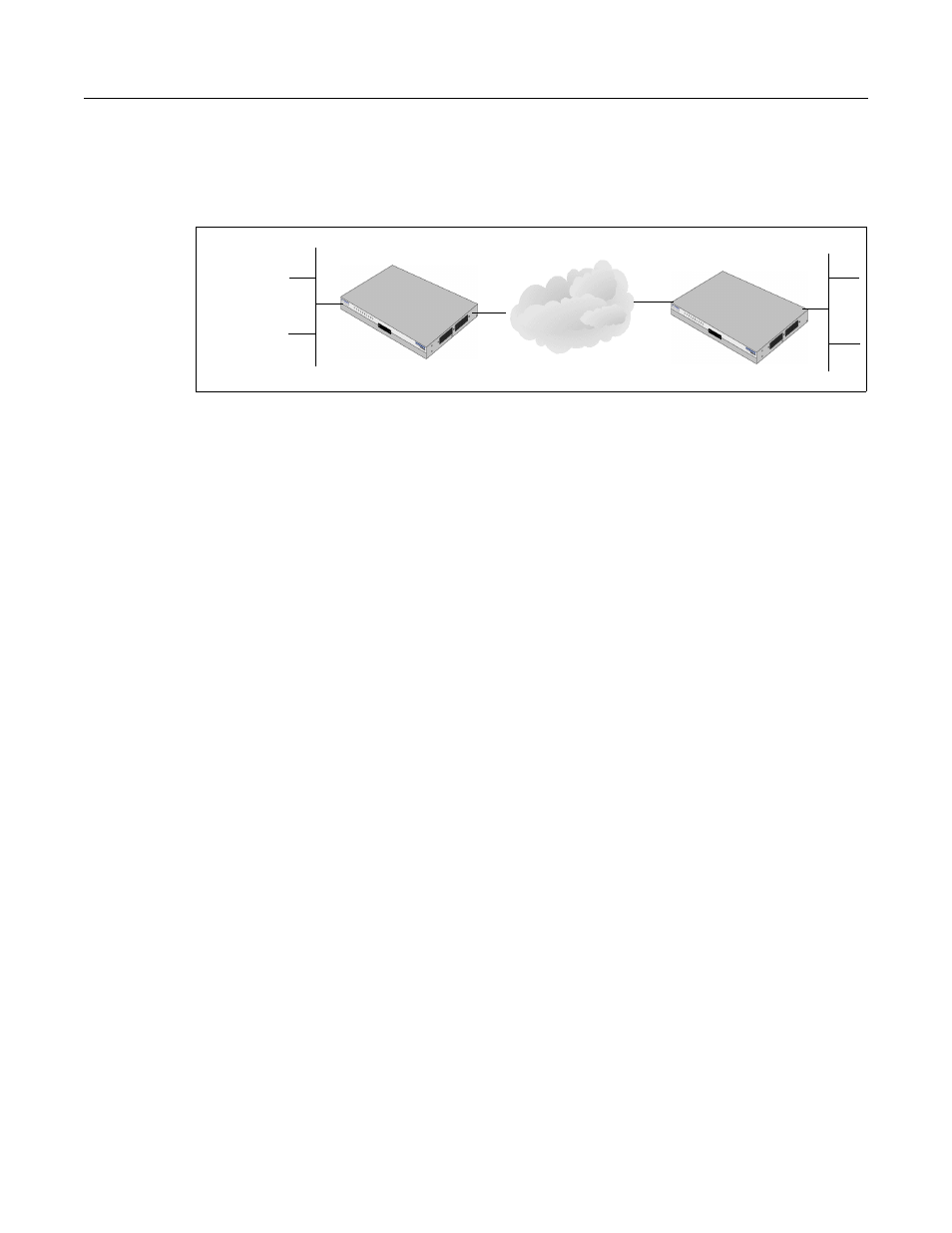
The following is a typical gateway-to-gateway VPN that uses certificates for authentication, as
illustrated in
.
Figure 14-14 Gateway-to Gateway with Certificates Topology
Gateway A connects the internal LAN 10.5.6.0/24 to the Internet. Gateway A's LAN interface has
the address 10.5.6.1, and its WAN (Internet) interface has the address 14.15.16.17.
Gateway B connects the internal LAN 172.23.9.0/24 to the Internet. Gateway B's WAN (Internet)
interface has the address 22.23.24.25. Gateway B's LAN interface address, 172.23.9.1, can be used
for testing IPsec but is not needed for configuring Gateway A.
The IKE Phase 1 parameters used in Scenario 2 are:
•
Main mode
•
Triple DES
•
SHA-1
•
MODP group 2 (1024 bits)
•
SA lifetime of 28800 seconds (eight hours) with no Kbytes rekeying
The IKE Phase 2 parameters used in Scenario 2 are:
•
Triple DES
•
SHA-1
•
ESP tunnel mode
•
MODP group 2 (1024 bits)
•
Perfect forward secrecy for rekeying
•
SA lifetime of 3600 seconds (one hour) with no Kbytes rekeying
•
Selectors for all IP protocols, all ports, between 10.5.6.0/24 and 172.23.9.0/24, using IPv4
subnets
This configuration assumes you have already set up the XSR for basic operations (refer to the XSR
Getting Started Guide). Also, you should have generated a master key (see the XSR User Guide). To
set up Gateway A for this scenario, perform the same steps as you would perform in Scenario 1,
with one exception.
In Step 5, for authentication, select RSA signatures as follows:
XSR(config-isakmp)#authentication rsa-sig
After completing all 11 steps to configure the VPN, obtain a Root CA and personal certificate for
this scenario by performing the following steps:
Internet
AL
10.5.6.1
AW
14.15.16.17
BW
22.23.24.25
BL
172.23.9.1
172.23.9.0/24
10.5.6.0/24
Gateway A
Gateway B
