The big picture – filtering, firewall and nat, 2 the big picture – filtering, firewall and nat – ZyXEL Communications Broadband Security Gateway P-312 User Manual
Page 165
P312 Broadband Security Gateway
Introducing the Prestige Firewall
14-5
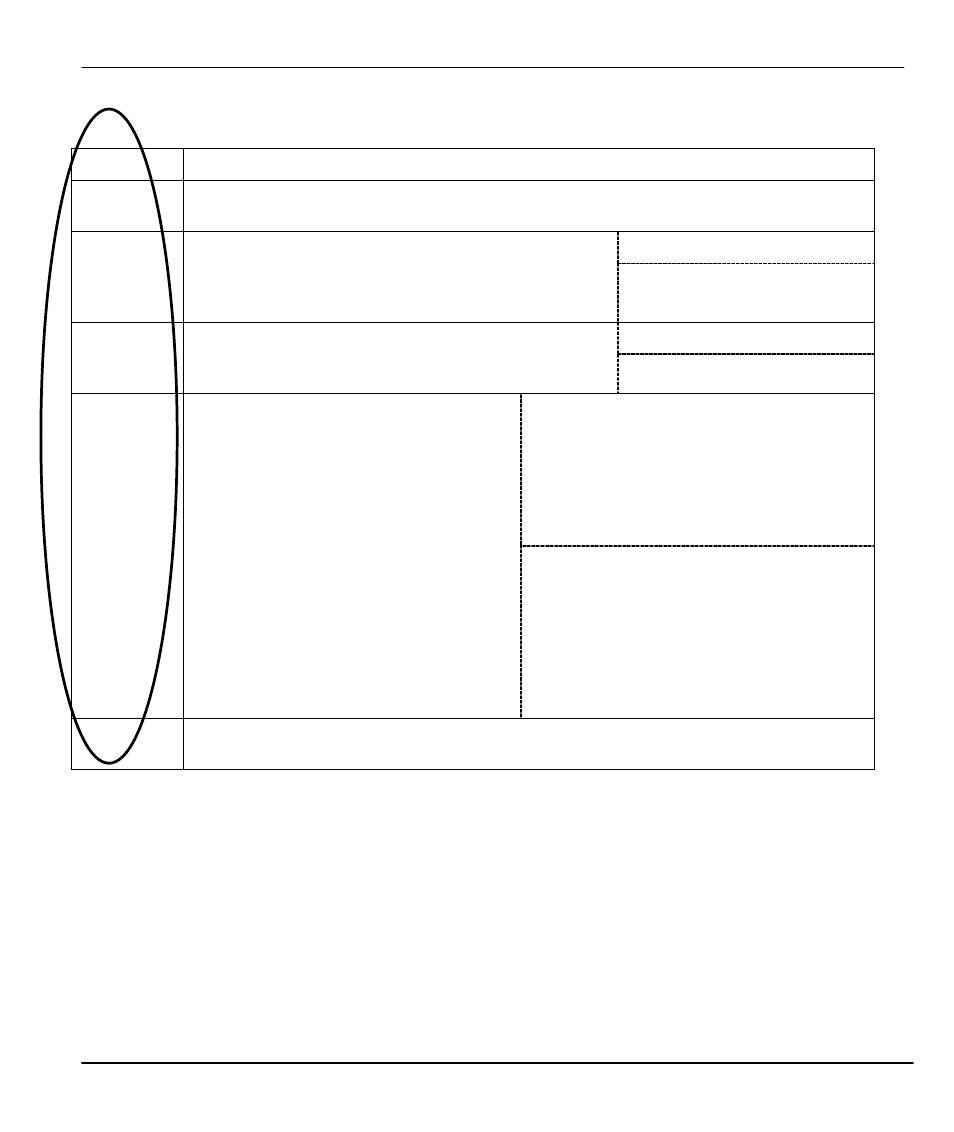
Table 14-4
View Firewall Log
Field
Description
#
This is the index number of the firewall log. 128 entries are available numbered from 0 to
127. Once they are all used, the log will wrap around and the old logs will be lost.
mm:dd:yy
e.g., Jan 1 70
Time
This is the time the log was recorded in this format.
You must configure Menu 24.10 for real time;
otherwise the clock started at Jan 1 70, 00:00:00 the
last time the P312 was reset.
hh:mm:ss
e.g., 00:00:00
From and To IP addresses
Packet
Information
This field lists packet information such as protocol and
src/dest port numbers (TCP, UDP), OR protocol, type
and code (ICMP).
protocol and port numbers.
not match
<1,01> dest IP
This means this packet does not match the
destination IP address in set 1, rule 1.
Other reasons (instead of dest IP) are src
IP, dest port, src port and protocol.
Reason
This field states the reason for the log;
i.e., was the rule matched, not matched,
or was there an attack. The set and rule
coordinates (
Y=00~10) follow with a simple
explanation. There are two policy sets;
set 1 (X = 1) is for LAN to WAN rules and
set 2 (X = 2) for WAN to LAN rules. Y
represents the rule in the set. You can
configure up to 10 rules in any set (Y = 01
to 10). Rule number 00 is the default rule.
attack
land
This is a log for a DoS attack - in this case
a land attack. Other attack types are ip
spoofing, icmp echo, icmp vulnerability,
NetBIOS, smtp illegal command,
traceroute, teardrop, or syn flood.
Action
This field displays whether the packet was blocked, forwarded or neither (block,
forward or none). None means that no action is dictated by this rule.
14.2 The Big Picture – Filtering, Firewall and NAT
The following diagram illustrates the path a packet takes as it passes through the filtering, firewall and NAT
process. NAT has been discussed in full in Chapter 6 of this manual. What follows is a brief comparison of
the firewall and filtering.
