Wireless security commands, Auth, Auth 7-114 – SMC Networks SMC2552W-G2-17 User Manual
Page 251
Command Line Interface
7-114
7
Wireless Security Commands
The commands described in this section configure parameters for wireless security
on the 802.11g interface.
auth
This command defines the 802.11 authentication type allowed by the VAP interface.
Syntax
auth
<open-system | shared-key | wpa | wpa-psk | wpa2 | wpa2-psk |
wpa-wpa2-mixed
| wpa-wpa2-psk-mixed | >
• open-system - Accepts the client without verifying its identity using a
shared key. “Open” authentication means either there is no encryption (if
encryption is disabled) or WEP-only encryption is used (if encryption is
enabled).
• shared-key - Authentication is based on a shared key that has been
distributed to all stations. If encryption is enabled, “shared” authentication
uses WEP-only encryption.
• wpa - Clients using WPA are accepted for authentication.
• wpa-psk - Clients using WPA with a Pre-shared Key are accepted for
authentication.
• wpa2 - Clients using WPA2 are accepted for authentication.
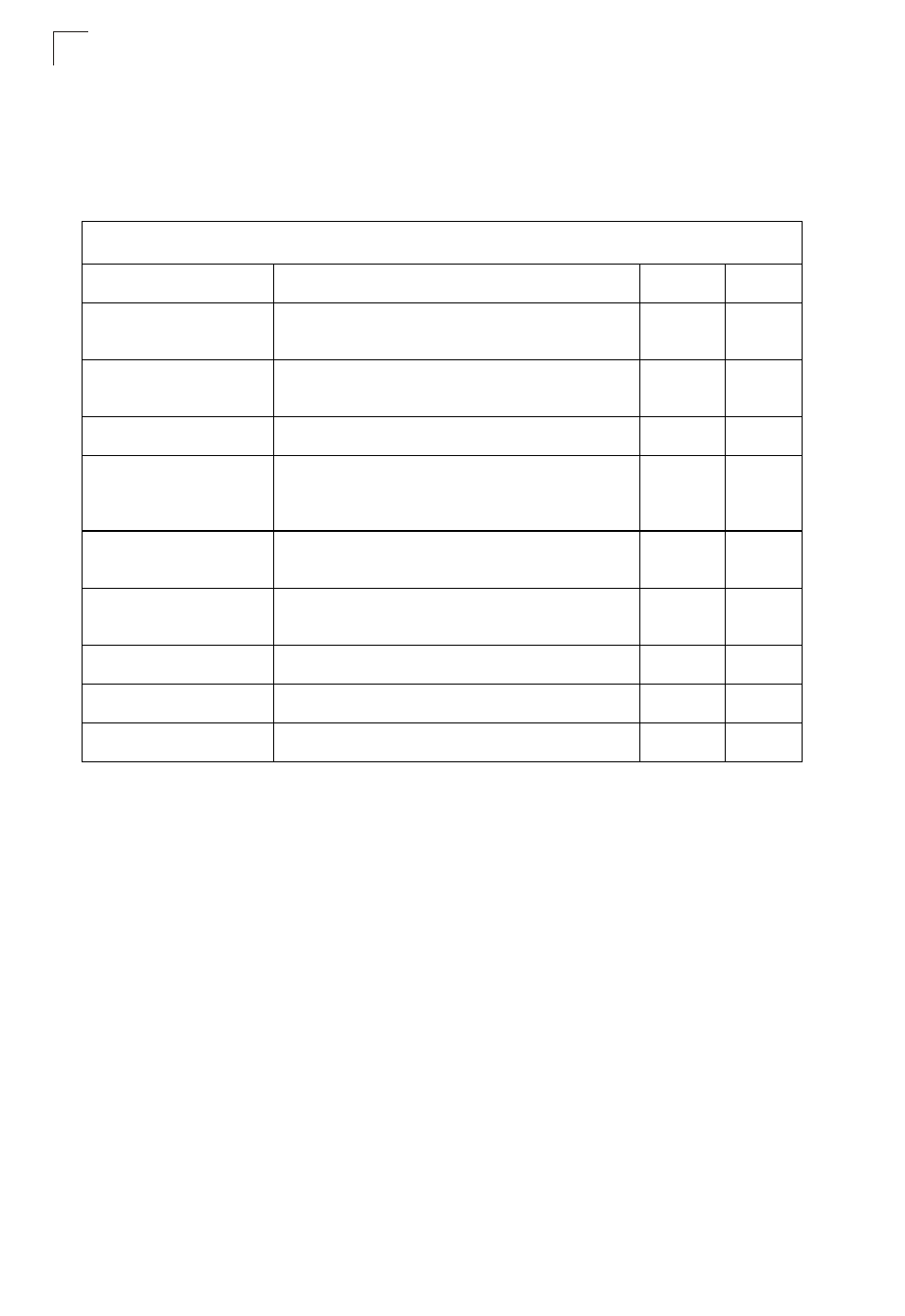
Table 7-19. Wireless Security Commands
Command
Function
Mode
Page
auth
Defines the 802.11 authentication type allowed by the
access point
IC-W-VAP
encryption
Defines whether or not WEP encryption is used to
provide privacy for wireless communications
IC-W-VAP
key
Sets the keys used for WEP encryption
IC-W
transmit-key
Sets the index of the key to be used for encrypting
data frames sent between the access point and
wireless clients
IC-W-VAP
cipher-suite
Selects an encryption method for the global key used
for multicast and broadcast traffic
IC-W-VAP
mic_mode
Specifies how to calculate the Message Integrity
Check (MIC)
IC-W
wpa-pre-shared- key
Defines a WPA preshared-key value
IC-W-VAP
pmksa-lifetime
Sets the lifetime PMK security associations
IC-W-VAP
pre-authentication
Enables WPA2 pre-authentication for fast roaming
IC-W-VAP
