Vlan mapping implementations, Configuring loop detection, Overview – H3C Technologies H3C S12500-X Series Switches User Manual
Page 152: Loop detection mechanism
141
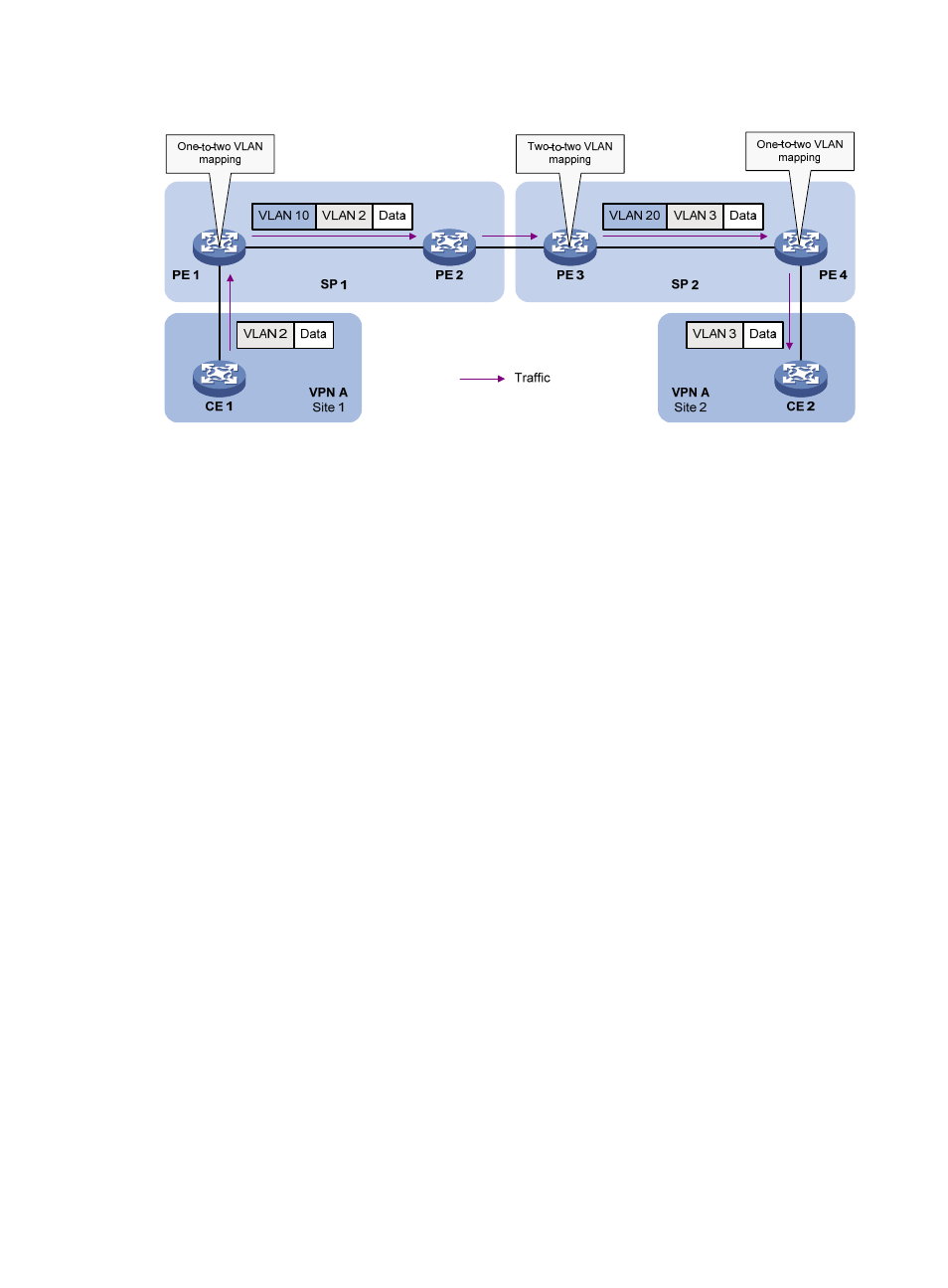
Figure 41 Application scenario of one-to-two and two-to-two VLAN mapping
Site 1 and Site 2 are in VLAN 2 and VLAN 3, respectively. The VLAN assigned to VPN A is VLAN 10
in the SP 1 network and VLAN 20 in the SP 2 network. When the packet from Site 1 arrives at the edge
of network SP 1, PE 1 tags the packet with outer VLAN 10 by using one-to-two VLAN mapping. With
one-to-two VLAN mapping, a VPN user can plan the VLAN IDs in the network without conflicting with
SVLANs. One-to-two VLAN mapping adds a VLAN tag to a tagged packet and expands the number of
available VLANs to 4094 × 4094. One-to-two VLAN mapping releases the stress on the SVLAN
resources, which were 4094 VLANs in the SP network before the mapping process was initiated.
When the double-tagged packet from the SP1 network enters the SP 2 network, PE 3 replaces the outer
VLAN tag (VLAN 10) with VLAN 20, which is the VLAN that the SP 2 network assigns to VPN A. Also,
PE 3 replaces the inner tag (VLAN 2) of the packet with VLAN 3, so that users in Site 1 can communicate
with users in Site 2.
VLAN mapping implementations
shows a simplified network to help explain the concepts and terms that you might encounter
when working with VLAN mapping.
These basic concepts include the following:
•
Uplink traffic—Traffic transmitted from the customer network to the service provider network.
•
Downlink traffic—Traffic transmitted from the service provider network to the customer network.
•
Network-side port—A port connected to or closer to the service provider network.
•
Customer-side port—A port connected to or closer to the customer network.
