Backup links and unwanted loops in wds bridges, Security considerations related to wds bridges – Allied Telesis AT-WA7400/EU User Manual
Page 175
AT-WA7400 Management Software User’s Guide
175
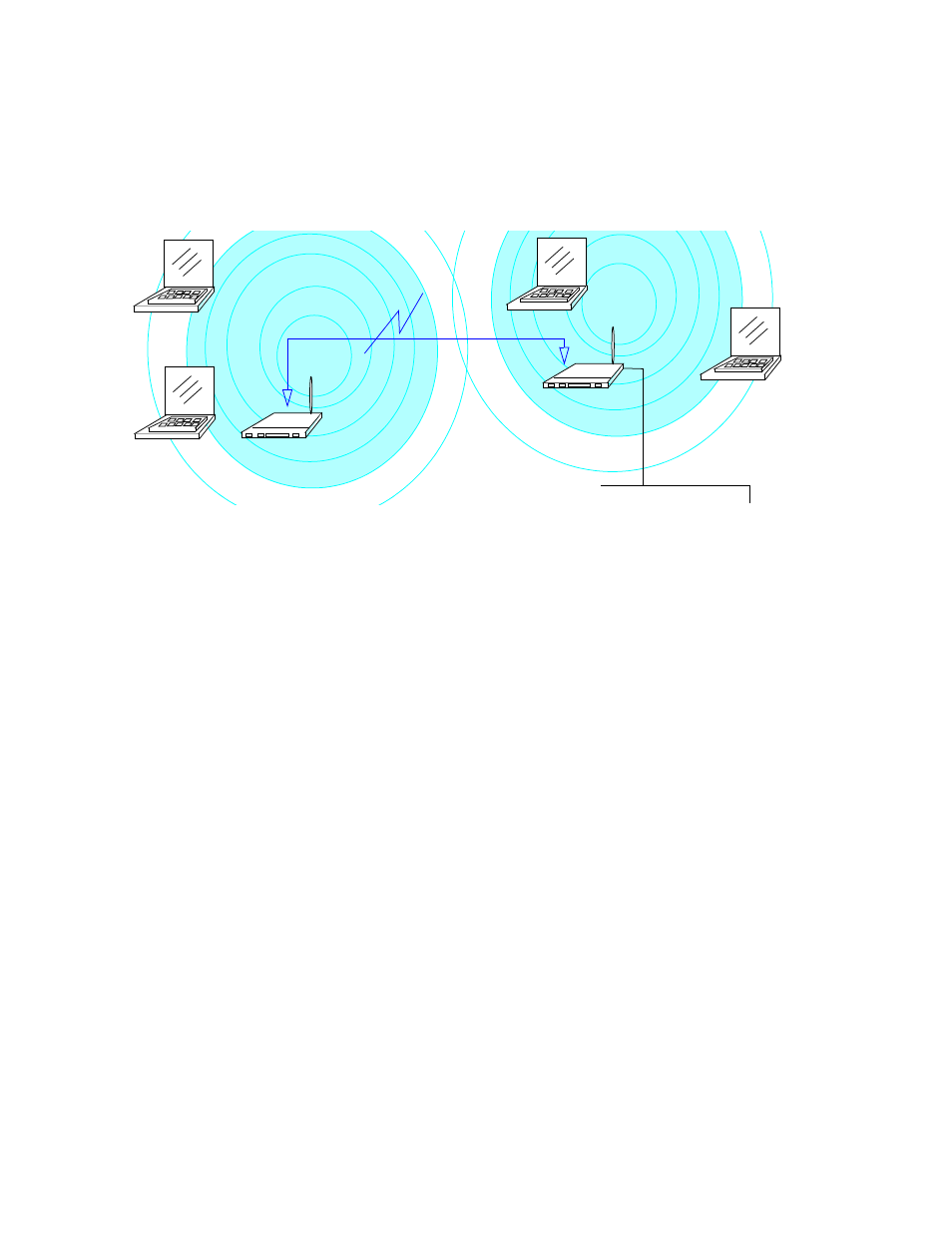
Ethernet cabling. You can solve this problem by placing a second access
point closer to second group of stations (Poolside in the example) and
bridge the two access points with a WDS link. This extends your network
wirelessly by providing an extra hop to get to distant stations, as shown in
Figure 51.
Figure 51. WDS Bridge
Backup Links
and Unwanted
Loops in WDS
Bridges
Another use for WDS bridging, the creation of backup links, is not
supported in this release of the AT-WA7400 Management Software. The
topic is included here to emphasize that you should not try to use WDS in
this way; backup links will result in unwanted, endless loops of data traffic
If an access point provides Spanning Tree Protocol (
STP
), WDS can be
used to configure backup paths between access points across the
network. For example, between two access points you could have both a
primary path via Ethernet and a secondary (backup) wireless path via a
WDS link. If the Ethernet connection goes down, STP would reconfigure
its map of the network and effectively fix the down network segment by
activating the backup wireless path.
In this release, the AT-WA7400 Management Software does not provide
STP. Without STP, it is possible that both connections (paths) may be
active at the same time, and result in an endless loop of traffic on the LAN.
Therefore, be sure not create loops with either WDS bridges or
combinations of Wired (Ethernet) connections and WDS bridges.
For more information, see “WDS Guidelines” on page 176.
Security
Considerations
Related to WDS
Bridges
Static Wired Equivalent Privacy (
WEP
) is a data encryption protocol for
802.11 wireless networks. Both access points in a given WDS link must be
configured with the same security settings. For static WEP, either a static
64-bit (40-bit secret key + 24-bit initialization vector (IV)) or 128-bit (104-bit
secret key + 24-bit IV) Shared Key is specified for data encryption.
WDS Bridge
Client Station
Client Station
Client Station
"East Wing" AP
"Poolside" AP
Client Station
LAN
Wire
d (E
ther
net)
Con
nect
ion
