Lun security – HP StorageWorks XP Remote Web Console Software User Manual
Page 19
LUN Configuration and Security Manager XP user guide for the XP128/XP1024
19
LUN Security
To protect data from unauthorized access, apply security policies to LUNs. LUN Manager can apply LUN
security to ports to safeguard LUs. If a port has the External attribute, you cannot apply LUN security to the
port.
NOTE:
You cannot apply LUN security to NAS ports.
If LUN security is applied, it limits which host can access which LUs. A host can only access LUs associated
with its host group. Hosts cannot access LUs associated with other host groups.
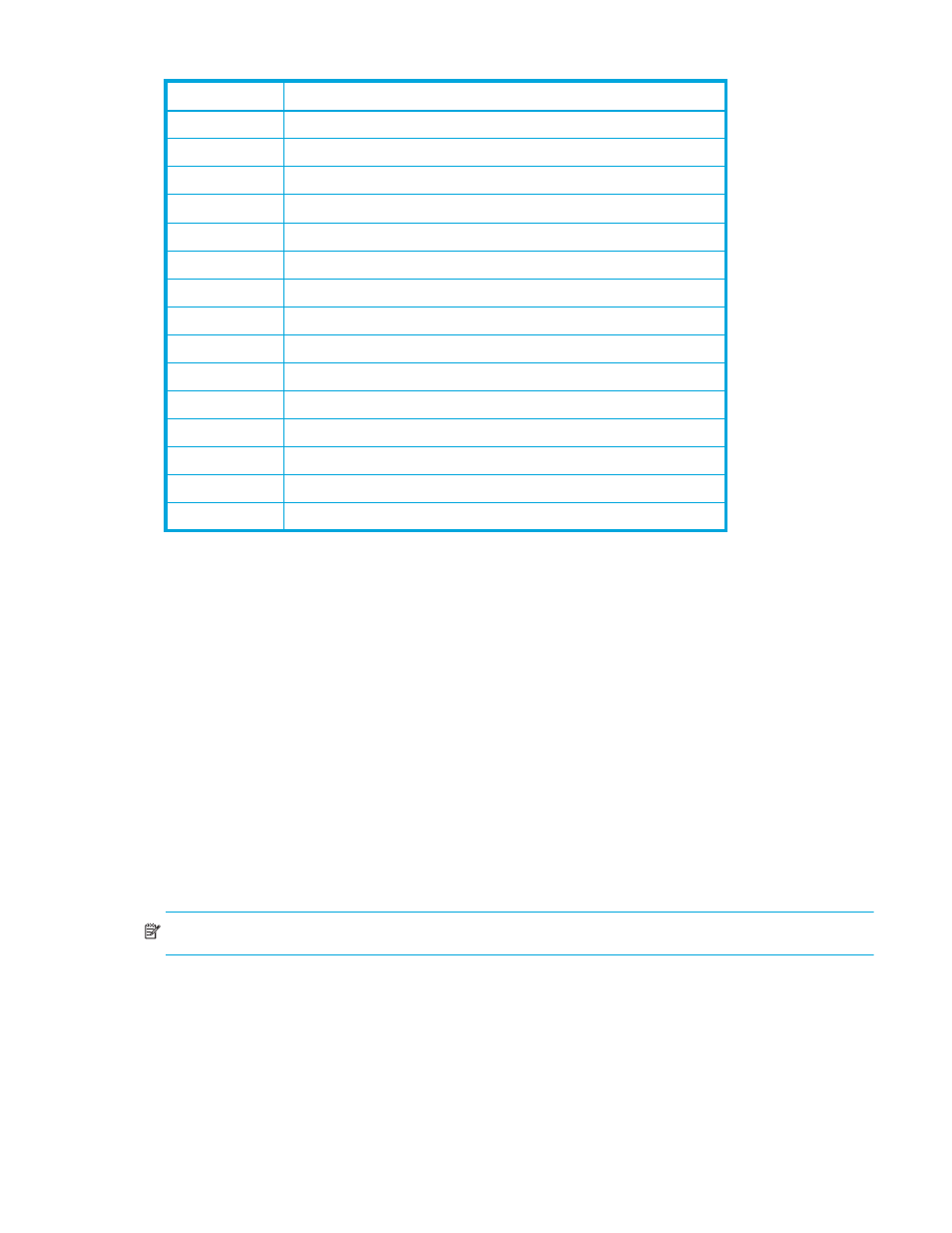
1A – 1F
Reserve
20 – 29
Reserve
2A, 2B
Reserve
2C
Windows Extension
3, 4
2D – 2F
Reserve
6A, 6B
Reserve
6C
Windows Extension 2
4,
5
6D, 6E
Reserve
6F
AIX Extension 2
6
29 Solaris
Extension
7
60
Red Hat Linux, IRIX (Standard Extension 2)
61, 62
Reserve
63
HP-UX (HP Extension 2)
64 – 68
Reserve
69
Solaris Extension 2
6
1. For Windows with any FC HBAs when MSCS is not needed.
2. For Windows with D8602 FC HBAs with or without MSCS.
3. For Windows with Emulex or QLogic FC HBAs with or without MSCS.
4. If you register Windows server hosts in a host group, verify that the host mode of the host group is 0C:
Windows, 2C: Windows Extension, or 6C: Windows Extension 2. If you are thinking about creating
LUSE volumes, such as expanded LUs, consider setting the host mode 2C: Windows Extension or 6C:
Windows Extension 2 to the host group. If the host mode of a host group is 2C: Windows Extension or
6C: Windows Extension 2, and an LU path is defined, you can create a LUSE volume. If the host mode
is 0C: Windows and an LU path is defined for a volume, you cannot execute LUSE operations on the
volume without unmapping the volume first.
5. This mode is the same as host mode 2C.
6. Select this mode if you are using any of the following: The I/O fencing feature in VERITAS Cluster
Server 4.0, VERITAS DataBase Edition/Active Cluster, or VERITAS Storage Foundation for Oracle
RAC.
7. Select this mode when registering Sun Cluster server hosts in the host group. Use this host mode when
both VERITAS Cluster Server and Sun Cluster are used.
Table 3
Host modes for host operating systems (continued)
Host mode
Host operating system
