HP Integrity NonStop H-Series User Manual
Page 44
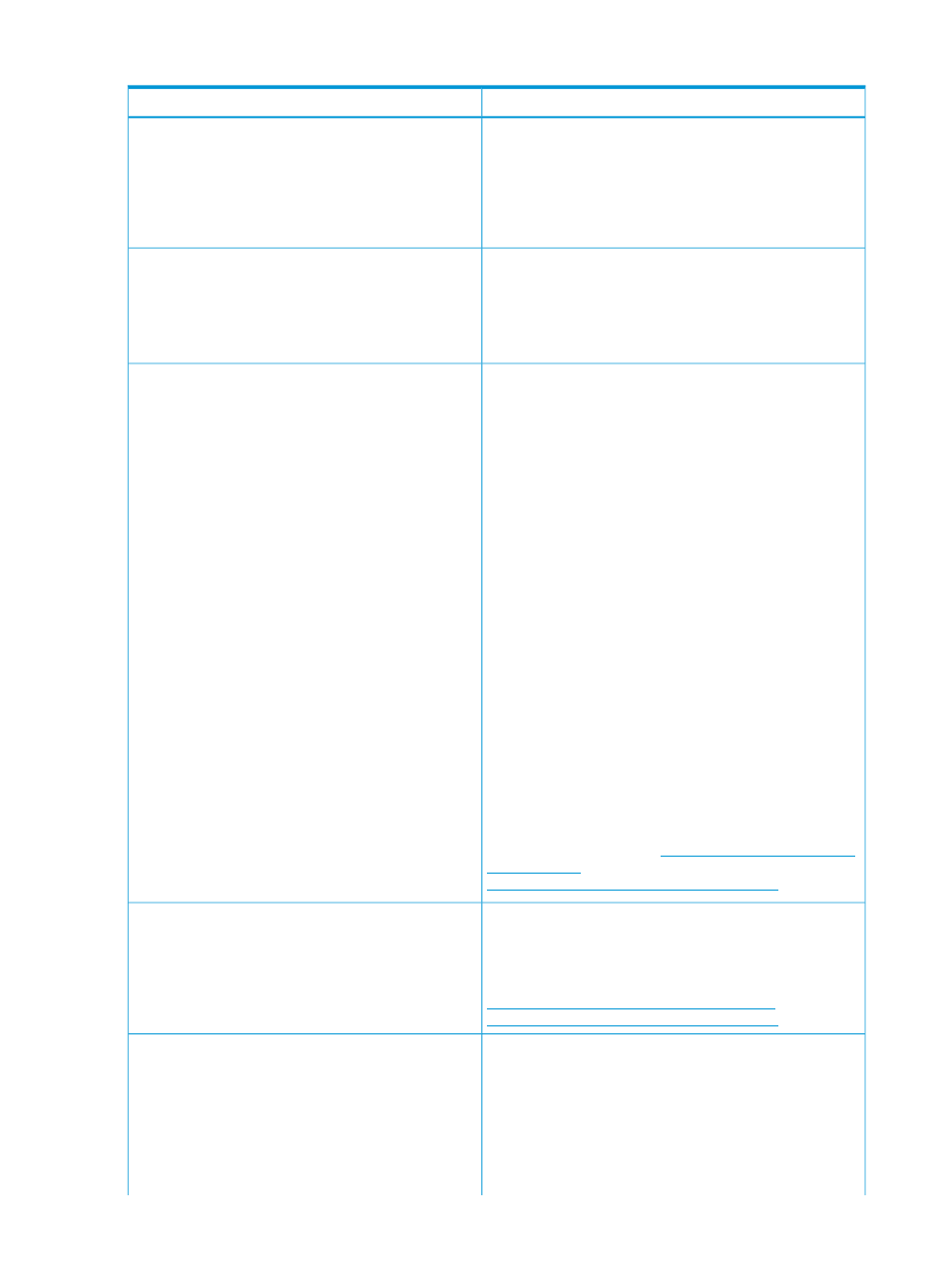
Table 7 Contents of host.xml
Description
Component
Within JBoss AS 7, the security realms are used to secure
access to the management interfaces. These realms are also
security-realms
used to provide security to resources, which get exposed by
JBoss Remoting such as EJB access. They are used to define
an identity for the server, where, the identity can be used for
both inbound and outbound connections which is established
by the server.
The host.xml defines two security realms namely, the
ManagementRealm
and ApplicationRealm. The
security-realm
ManagementRealm
is used by the management interface,
and the ApplicationRealm is used by the remoting
subsystem to authenticate and authorize incoming requests
for EJB invocations.
The default configuration in both the ManagementRealm
and the ApplicationRealm has two authentication
authentication
mechanisms. The local mechanism and username-password
authentication mechanism which use Digest authentication.
This means the password is encrypted using a digest
algorithm.
1.
Local authentication mechanism: When using this
mechanism (represented by the
optional for the remote clients to send a username to the
server. This configuration specifies that where clients do
not send a username to the server, it is assumed that the
clients username is $local (indicated by the
default-user
attribute). The local authentication can
also be configured to restrict users that are allowed access
by using the allowed-user attribute. This attribute with
a value of * means that the remote user can specify any
username, and is accepted over the local mechanism
provided that the username-password authentication
mechanism is a success.
2.
Username-password authentication mechanism: Here the
user details are loaded from the properties file referred to
by the attribute path. The entries are prehashed, and
each entry is of the format username=
. The entries can be added to the properties file
using the add-user.sh script in the
folder.
For more information, see Authentication section in the
chapter Management Tasks
.
The contents of this element are used to load properties for
a user. The entries are of the form
authorization
where ROLES is a comma separated list of roles that are
associated with the user. For more information, see
Authorization section in the chapter Management Tasks
.
This element defines the interfaces to access the management
functionality. In NSASJ, only the native interface is enabled,
management-interfaces
and the interface is by default associated with the security
realm by the name ManagementRealm. By default, the
management interface is available on the port
BASE_PORT+3
.
NOTE:
BASE_PORT
is obtained from the user during NSASJ
installation.
44
Configuring NSASJ
