Securing web access, Security domain – HP Integrity NonStop H-Series User Manual
Page 58
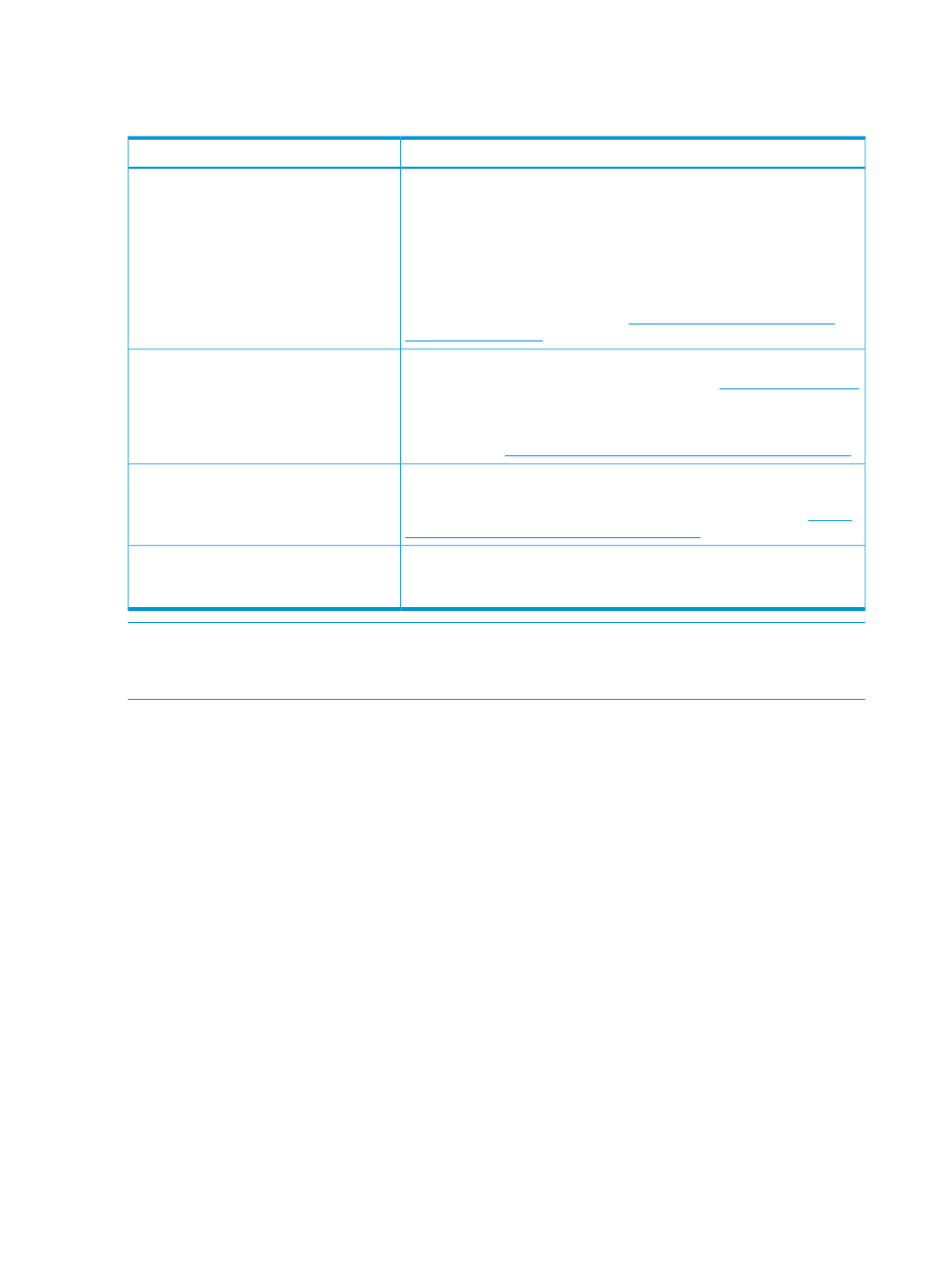
lists the components of the Web subsystem, and then discusses the attributes
comprising it.
Table 14 Components of Web subsystem
Element/Attribute
Component
Represents the interface between external clients sending requests and
receiving responses from a particular service. In addition to the ability to
connector
execute Servlets and JSP pages, the connector component enables Catalina
to function as a standalone web server. The default configuration of NSASJ
has two connectors, HTTP and HTTPS that support the HTTP/1.1 protocol.
These can be configured to listen to standard ports 80 and 443, or at
base_port + 9 and base_port +10 based on the selection made during
the installation. The connectors process requests and create responses. For
more information on connector, see
.
The virtual-server element represents a virtual host, which is an
association of a network name for a server such as
virtual-server
with the particular server on which Catalina is running. To be effective,
this name must be registered. A default sample configuration of virtual
host can be found in the NSASJ domain.xml. For more information on
virtual host, see
.
The jsp-configuration describes the way JSP container works. There
must be only one jsp-configuration element inside the Web
jsp-configuration
subsystem. For more information on jsp-configuration, see
.
The static-resource is the default service for all web applications
that serves static resources. It processes all requests that are not mapped
to other Servlets with Servlet mappings.
static-resource
NOTE:
NSASJ does not support AJP connector.The load balancing of the web server is handled
by the NonStop platform services such as TCP/IP and TS/MP Pathway. Mod_cluster used by
JBoss is not required for load balancing connectors in NSASJ.
Securing web access
There are two ways to secure and restrict access for applications on NSASJ’s web container.
Security domain
A security domain consists of configurations for authentication, authorization, security mapping,
and auditing. It implements Java Authentication and Authorization Service (JAAS) declarative
security. An application can be authenticated by specifying the security domain in either the server's
configuration file (domain.xml) or in the application descriptor file (jboss-web.xml), and by
adding the required annotations such as @RolesAllowed, @SecurityDomain in the application. The
following example provides a sample configuration of security in domain.xml:
With this configuration, the application can use the login module to authenticate a user by providing 58 Configuring NSASJ
security constraint in the applications.
