Smurf attack, Traceroute, Ip spoofing – ZyXEL Communications ZyXEL ZyWALL IDP 10 User Manual
Page 103: Distributed denial-of-service attack, Scanning, A.4 scanning
ZyWALL IDP10 User’s Guide
Introduction to Intrusions
A-3
A.3.6 Smurf Attack
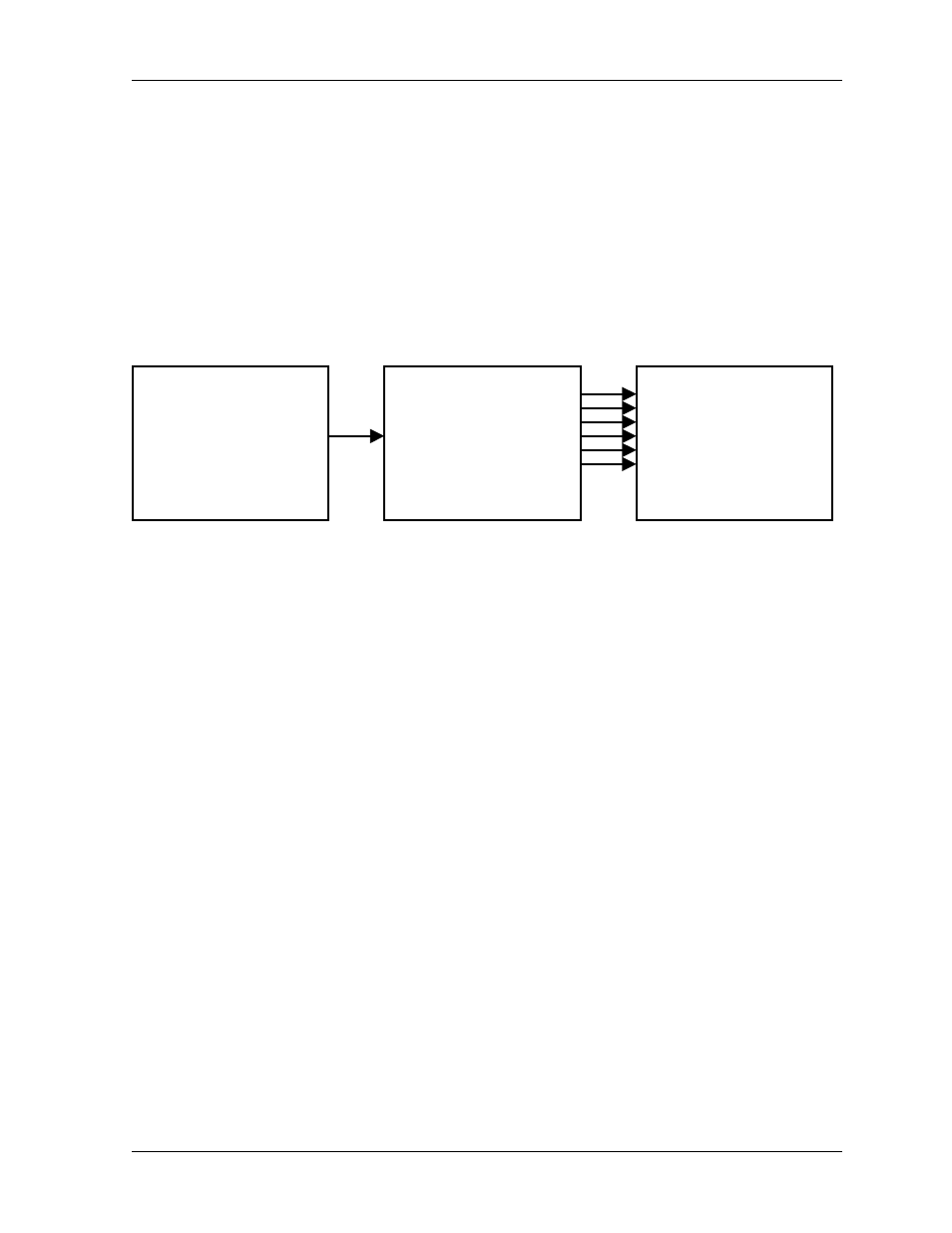
A Smurf attack targets a feature in the IP specification known as directed or subnet broadcasting, to
quickly flood the target network with useless data. A Smurf hacker floods a router with Internet
Control Message Protocol (ICMP) echo request packets (pings). Since the destination IP address of
each packet is the broadcast address of the network, the router will broadcast the ICMP echo request
packet to all hosts on the network. If there are numerous hosts, this will create a large amount of ICMP
echo request and response traffic. If a hacker chooses to spoof the source IP address of the ICMP echo
request packet, the resulting ICMP traffic will not only clog up the "intermediary" network, but will
also congest the network of the spoofed source IP address, known as the "victim" network. This flood
of broadcast traffic consumes all available bandwidth, making communications impossible.
Figure A-3 Smurf Attack
A.3.7 Traceroute
Traceroute is a utility used to determine the path a packet takes between two endpoints. Sometimes
when a packet filter firewall is configured incorrectly an attacker can traceroute the firewall gaining
knowledge of the network topology inside the firewall.
A.3.8 IP Spoofing
Often, many DoS attacks also employ a technique known as IP spoofing as part of their attack. IP
spoofing may be used to break into systems, to hide the hacker's identity, or to magnify the effect of
the DoS attack. IP spoofing is a technique used to gain unauthorized access to computers by tricking a
router or firewall into thinking that the communications are coming from within the trusted network.
To engage in IP spoofing, a hacker must modify the packet headers so that it appears that the packets
originate from a trusted host and should be allowed through the router or firewall.
A.3.9 Distributed Denial-Of-Service Attack
A distributed denial-of-service (DDoS) attack is one in which multiple compromised systems attack a
single target, thereby causing denial of service for users of the targeted system. A hacker begins a
DDoS attack by exploiting vulnerability in one computer system and making it the “DDoS source”. It
is from this source that the hacker identifies and communicates with other systems that can be
compromised. The hacker instructs the “DDoS source(s)” to launch flood attacks against a specified
target. The inundation of packets to the target causes a denial of service.
A.4 Scanning
Hackers scan ports to find targets. Some example methods are as follows:
Attack Source
Attackers broadcast
"ping" packets with a
spoofed source IP
address to every host on
the intermediary network.
Intermediary Network
Every host on the
intermediary network
sends "responses" to
every host on the Victim
network.
Victim Network
