Rist main profile authentication, Technology overview – Cobalt Co9992-4ENC-4K-HEVC Software-Defined Broadcast Encoder User Manual
Page 118
118
RIST Main Profile Authentication
Technology Overview
RIST Main Profile security (encryption and authentication) is provided by DTLS, which is the
datagram version of the TLS functionality used to secure web sites. This technology is mature
and widely deployed.
DTLS authentication is based on the concept of
Key/Certificate
pairs. A
Key
must be kept
secret. A
Certificate
is derived from the
Key
and is public. A certificate allows secure
communication, but only with the device that holds the corresponding key.
A certificate may be signed by a third party called a
Certificate Authority (CA)
. This is a third
party that is trusted; if a device is prepared to trust the Certificate Authority, that trust extends to
the certificates signed by it.
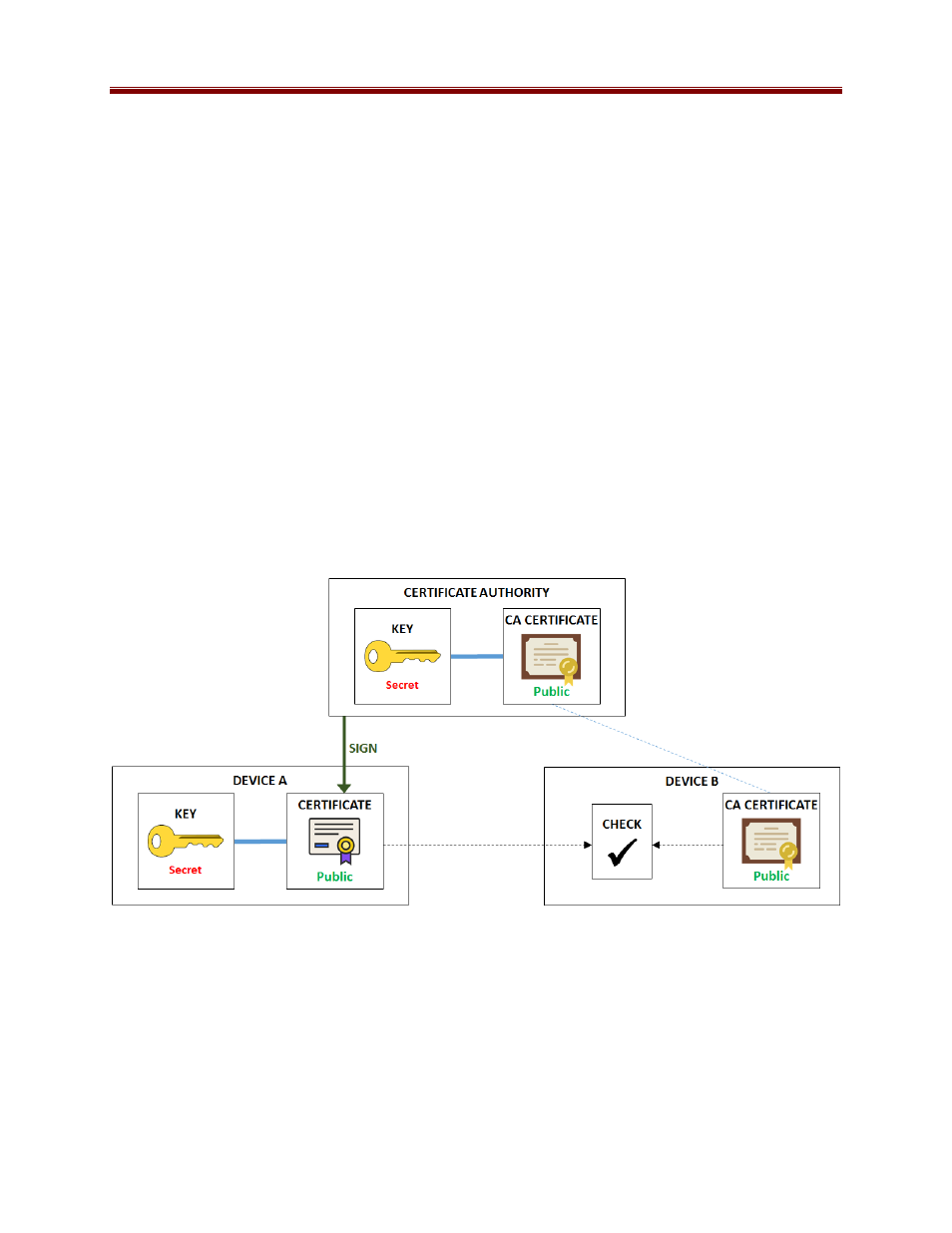
The certificate-based authentication process is illustrated in Figure 1. In this figure, Device B is
deciding whether or not it trusts Device A. The same process can happen independently in the
other direction. Device B has decided to trust certificates signed by a certain CA, so it has a
copy of its CA Certificate, which was transferred to it through some secure means. Device B
then receives a certificate from Device A. Unless that certificate matches the key stored in
Device A, communication cannot even start. Device B can locally check the CA signature in the
certificate coming from Device A against the CA Certificate it has. It that signature matches,
and if Device B is prepared to trust the CA, then it will agree to communicate with Device A.
Security is maintained since:
Even though the certificate from Device A is public, an unauthorized device cannot use it
to establish communication because it does not have the corresponding key.
Communication will not start.
An unauthorized device may have a consistent certificate/key pair, but it will not be able
to use it to start communication because the certificate is not signed by the CA trusted by
Device B.
Figure 1: Certificate Checking
