The intrusion prevention system (ips), Networking and security basics – Linksys WRVS4400N User Manual
Page 15
WRVS4400N User Guide 9
The Intrusion Prevention System (IPS)
Networking and Security Basics
The Intrusion Prevention System (IPS)
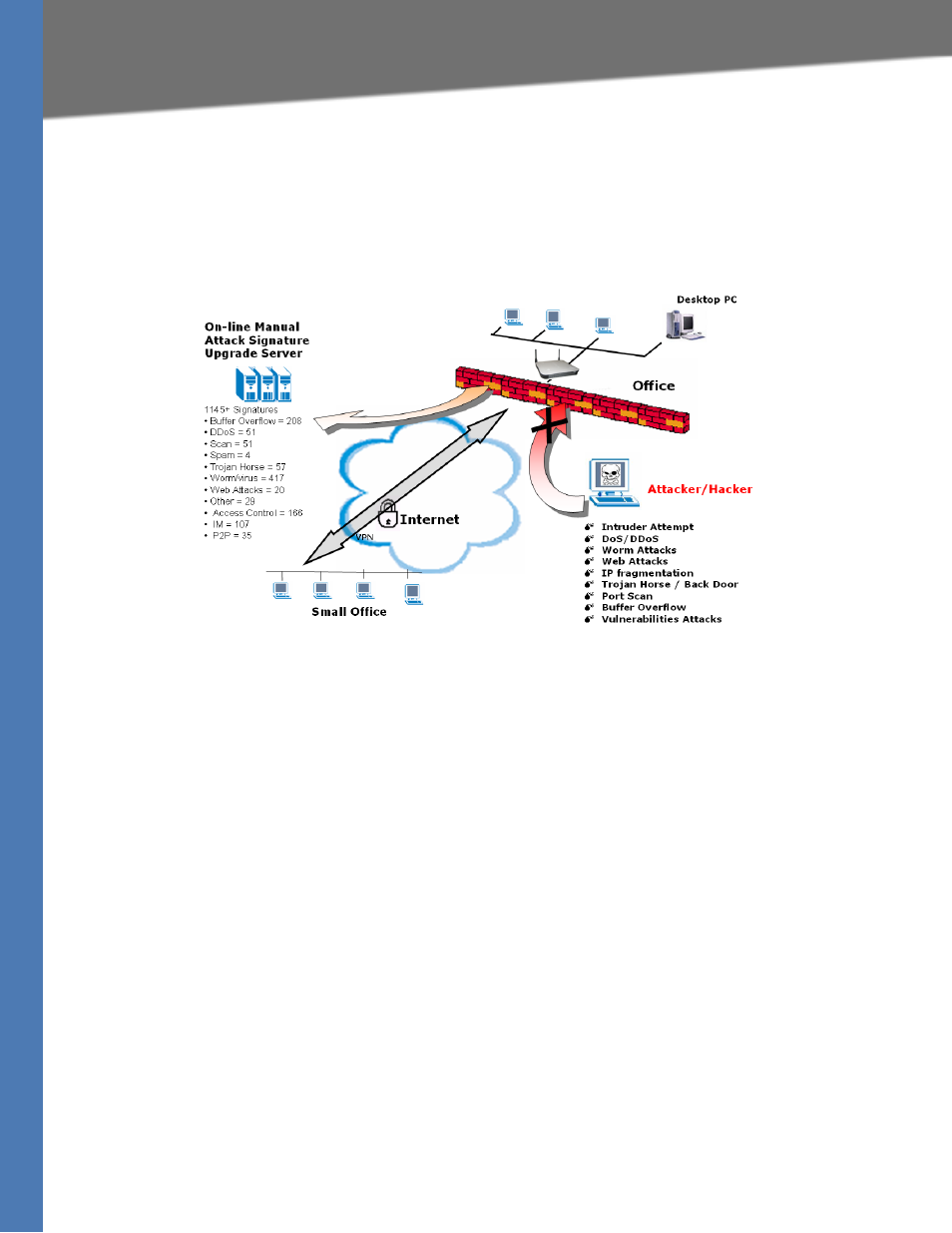
IPS is an advanced technology to protect your network from malicious attacks. IPS works
together with your SPI Firewall, IP Based Access List (IP ACL), Network Address Port Translation
(NAPT), and Virtual Private Network (VPN) to achieve the highest amount of securities.
IPS Scenarios
IPS works by providing real-time detection and prevention as an in-line module in a router. The
Wireless-N Security Router has hardware-based acceleration for real-time pattern matching for
malicious attacks. It actively filters and drops malicious TCP/UDP/ICMP/IGMP packets and can
reset TCP connections. This protects your client PCs and servers running various operating
systems including Windows, Linux, and Solaris from network worm attacks. However, this
system does not prevent viruses attached emails.
The P2P (peer to peer) and IM (instant messaging) control allows the system administrator to
prevent network users from using those protocols to communicate with people over the
Internet. This helps the administrators to set up company policies on how to use their Internet
bandwidth wisely.
The signature file is the heart of the IPS system. It is similar to the Virus definition files on your
PC’s Anti-Virus programs. IPS uses this file to match against packets coming in to the Router and
performs actions accordingly. As of today, the Wireless-N Router is shipped with signature file
version 1.3.8 and with a total of 1101 rules. The rules cover the following categories: DDoS,
Buffer Overflow, Access Control, Scan, Trojan Horse, Misc., P2P, IM, Virus, Worm, and Web
Attacks.
Customers are encouraged to update their IPS signature file regularly to prevent any new type
of attacks on the Internet.
