2 wireless security settings, Security settings – B&B Electronics EKI-6311GN-EU - Manual User Manual
Page 37
Page 31
4.2 Wireless Security Settings
To prevent unauthorized radios from accessing data transmitting over the connectivity, the EKI-6311GN
provides you with rock solid security settings.
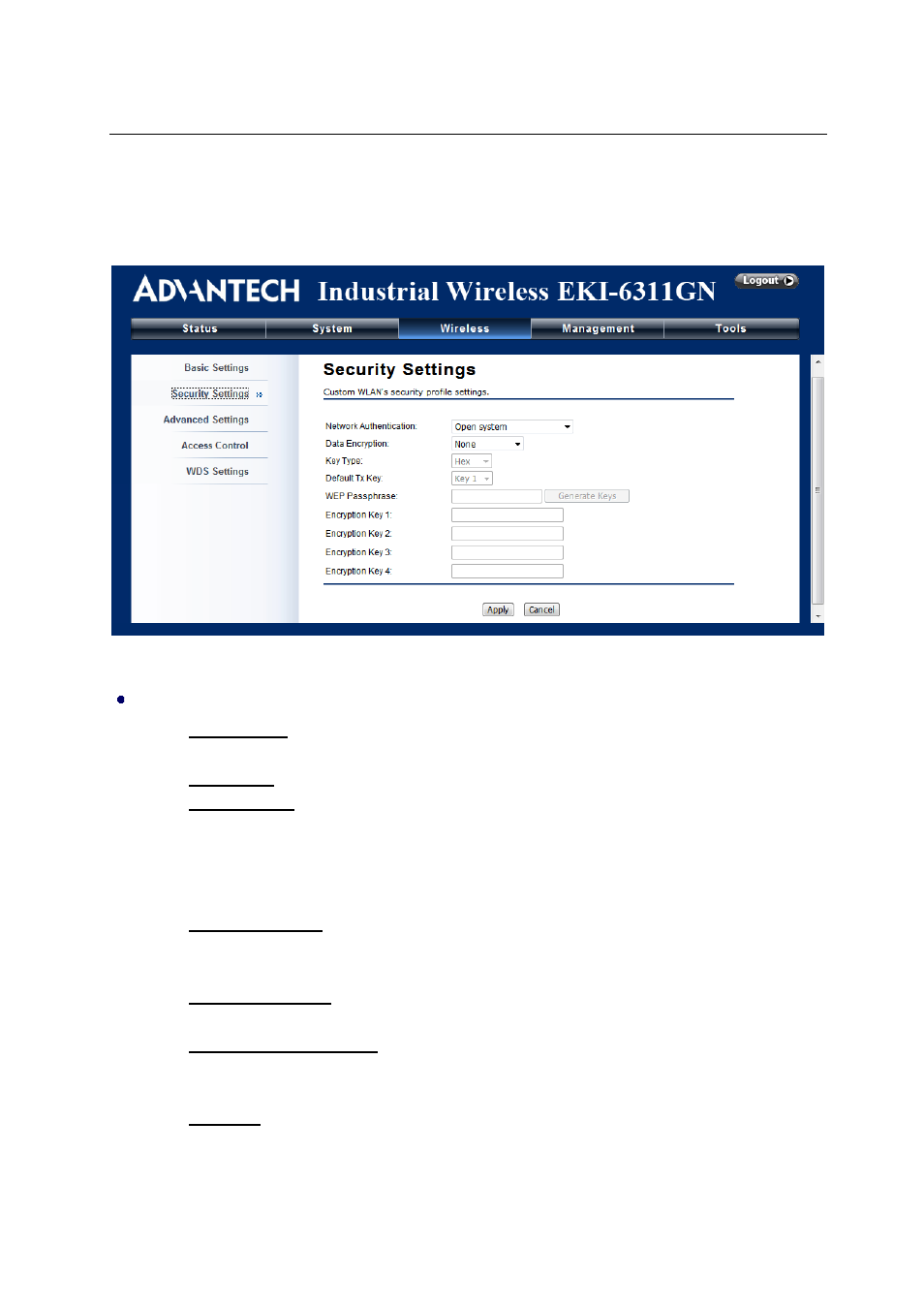
Security Settings
Open “Security Settings” in “Wireless” as below:
Figure 17 Security Settings
Network Authentication
Open System: It allows any device to join the network without performing any security
check.
Shared Key: Data encryption and key are required for wireless authentication.
Legacy 802.1x: As an IEEE standard for port-based Network Access Control, it provides the
rights to access the wireless network and wired Ethernet. With User and PC identity,
centralized authentication as well as dynamic key management, it controls the security risk
of wireless network to the lowest. To serve the 802.1x, at least one EAP type should be
supported by the RADIUS Server, AP and wireless client.
WPA with RADIUS: With warrant (username, password and etc.) offered by user, this kind
of authentication can be realized with specific RADIUS server. This is the common way to
be adopted in large enterprise network.
WPA2 with RADIUS: As a new version of WPA, only all the clients support WPA2, can it be
available. If it is selected, AES encryption and RADIUS server is required.
WPA&WPA2 with RADIUS: It provides options of WPA (TKIP) or WPA2 (AES) for the client.
If it is selected, the data encryption type must be TKIP + AES and the RADIUS server must
be set.
WPA-PSK: It is a simplified WPA mode with no need for specific authentication server. In
this so-called WPA Pre-Shared Key, all you have to do is just pre-enter a key in each WLAN
node and this is the common way to be adopted in large and middle enterprise as well as
residential network.
