Epson VIGOR 3300 User Manual
Page 91
Vigor3300 Series User’s Guide
87
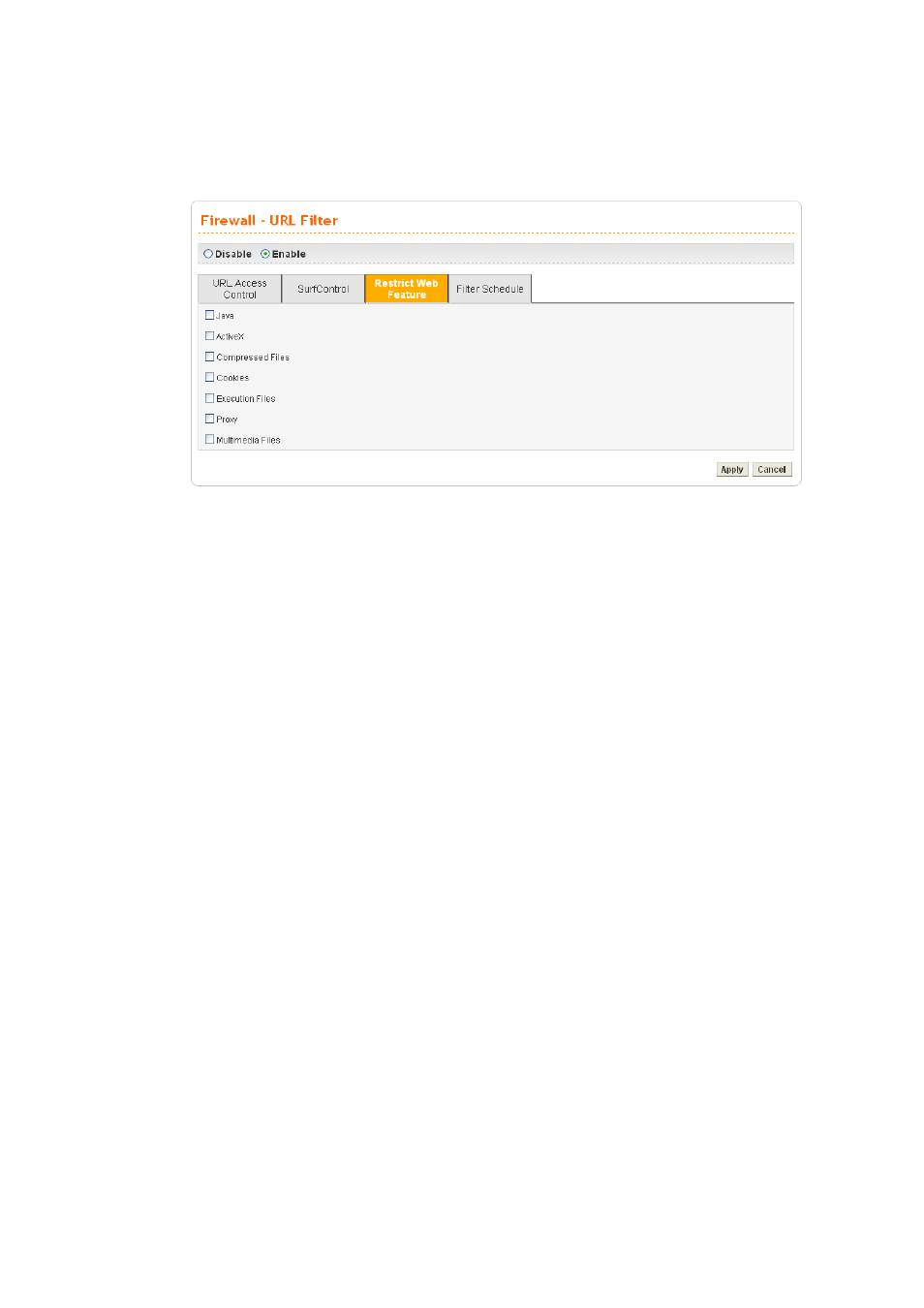
Malicious code may be embedded in some executable objects, such as ActiveX, Java Applet,
compressed files, executable files, Proxy, and Multimedia. For example, an ActiveX object
with malicious code may gain unlimited access to the system.
Java
Activates the Block Java object function. The router will
discard Java objects from the Internet.
ActiveX
Activates the Block ActiveX object function. The router will
discard ActiveX object from the Internet.
Compressed Files
Activates the Block Compressed file function to prevent from
downloading of any compressed file. These following types of
compressed files are blocked by the router.
.zip / .rar /.arj /.ace / .cab /.sit
Execution Files
Activates the Block Executable file function to prevent from
downloading of any executable file. The following types of
executable files are blocked by the router.
.exe /.com /.scr /.pif /.bas /.bat /.inf / .reg
Cookie
Activates the Block Cookie function. Cookies are used by many
websites to create “stateful” sessions for tracking Internet users,
which would violate the users’ privacy. The router will filter out
all cookies-related transmissions.
Proxy
Activates the Block Proxy function. The router will filter out all
proxy-related transmissions.
Multimedia Files
Activates the Block Multimedia function. The router will filter
out multimedia from any website.
F
F
i
i
l
l
t
t
e
e
r
r
S
S
c
c
h
h
e
e
d
d
u
u
l
l
e
e
Filter Schedule function controls what times the URL content filter should be active. It can
specify what times the URL content filtering facility should be active.
