Creating a virtual private network (vpn) -5, Creating a virtual private network (vpn) – Acer 700 Series User Manual
Page 13
1-5
AcerRouter 700 Series User Guide
AcerVoIp system does not support fax over the Internet.
When data is sent over a congested and unpredictable public network such as the
Internet, it may encounter variable delays and data loss. For time insensitive data, this
is acceptable, since delay does not do any harm, and the application software will
recover from any data loss by requesting the sender to re-send any lost data.
However, this is not the case with time-sensitive data such as voice traffic. Extreme
care has to be taken to make sure that the quality of voice traffic through the Internet
does not suffer much due to delays through the network. On the other hand, there will
still be times when no matter what is done, the quality of voice over the Internet can
not compare to the quality of voice calls through the standard PSTN network.
However, AcerRouters continue to be at the forefront of this type of Internet voice
technology.
The AcerRouter 700 maintains a convenient SpeedDial table in which shortcuts can
be configured either for conventional calls, or for AcerVoIp calls. These shortcuts are
from one to eight digits in length. Thus, an out-going call may be placed
conventionally through the ISDN/PSTN or across the Internet in a seamless manner.
Additionally, the AcerVoIp offers a FallBack feature: AcerVoIp entries in the
SpeedDial table can be configured to make a standard PSTN call in case the called
part cannot be reached through the Internet. This called Fallback. This is so that the
caller’s dialing habits are not changed, making the feature easy and familiar to the
user.
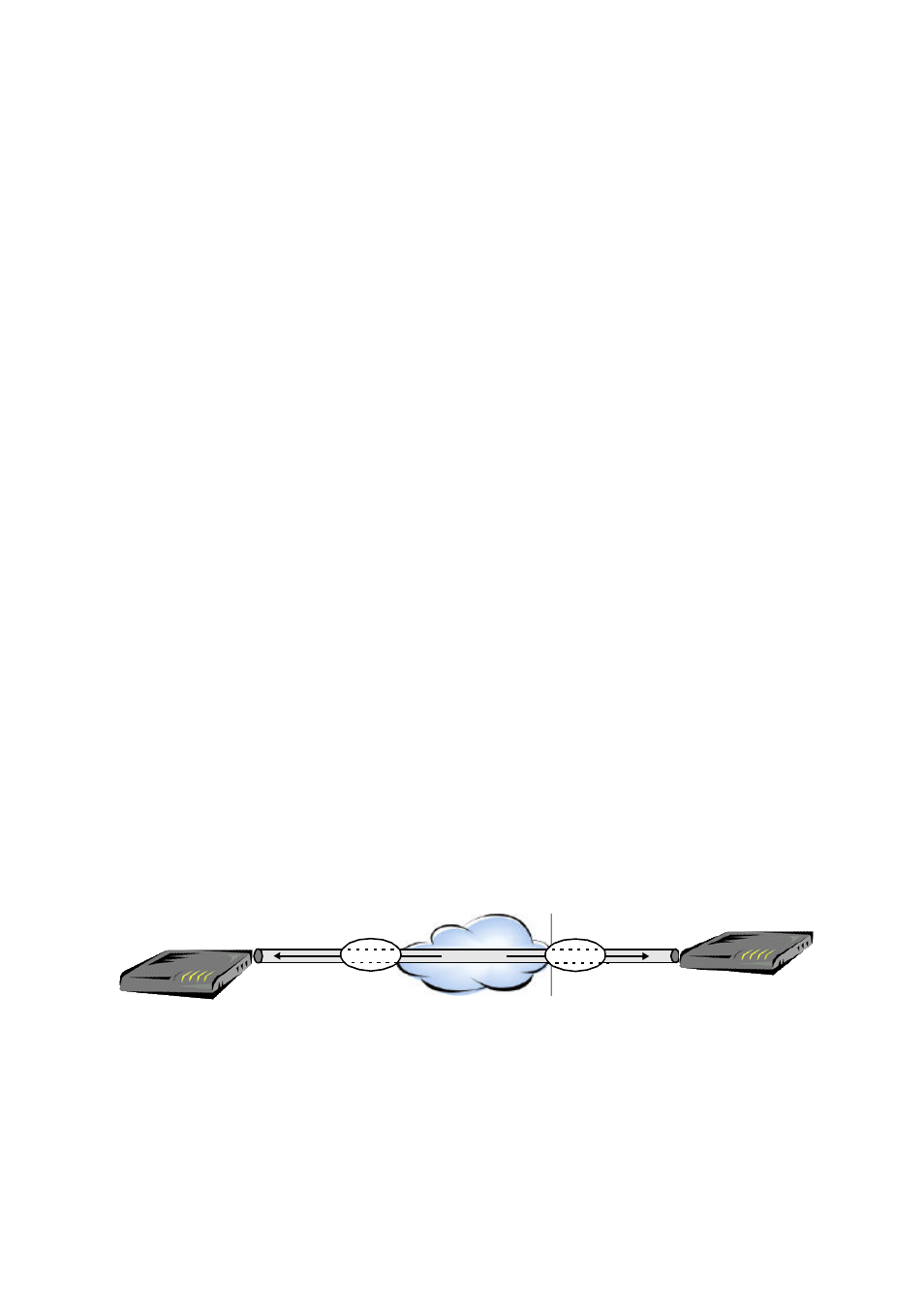
Creating a Virtual Private Network (VPN)
Virtual Private Networking (VPN) provides a means to connect remote LANs over
public networks such as the Internet. This means that only local toll charges to an
Internet Service Provider are incurred. The data can be encrypted to prevent
unauthorized access.
In order to accomplish this, a special connection is first set up between the two sites,
called "tunnel". Once a tunnel is set up, one or more user data sessions may be
established which flows through the tunnel.
In the AcerRouter, tunnels are created over the Internet. They are configured in a
manner similar to a telephone line. It is not necessary to require authentication when
creating a tunnel, since no sensitive data will be transferred until a user connection is
established. Therefore, authentication information is normally associated with the
connection profile for the user data session using the tunnel.
Figure 1-6 Creating a Virtual Private Network
As is the case for switched connections, a PC on the LAN sending data to a resource
reachable through a VPN connection profile will cause a tunnel to be set up to the
remote site. Once this is done, the VPN user session will commence, beginning with a
PPP authentication exchange.
VPN Tunnel
over ISDN
700 #1
700 #2
Secure Data
ISP
ISP
Internet
