Table 2 model specific features – ZyXEL Communications P-660H-D Series User Manual
Page 40
P-660R/H-D Series User’s Guide
39
Chapter 1 Getting To Know Your Prestige
Note: See the product specifications in the appendix for detailed features and
standards support.
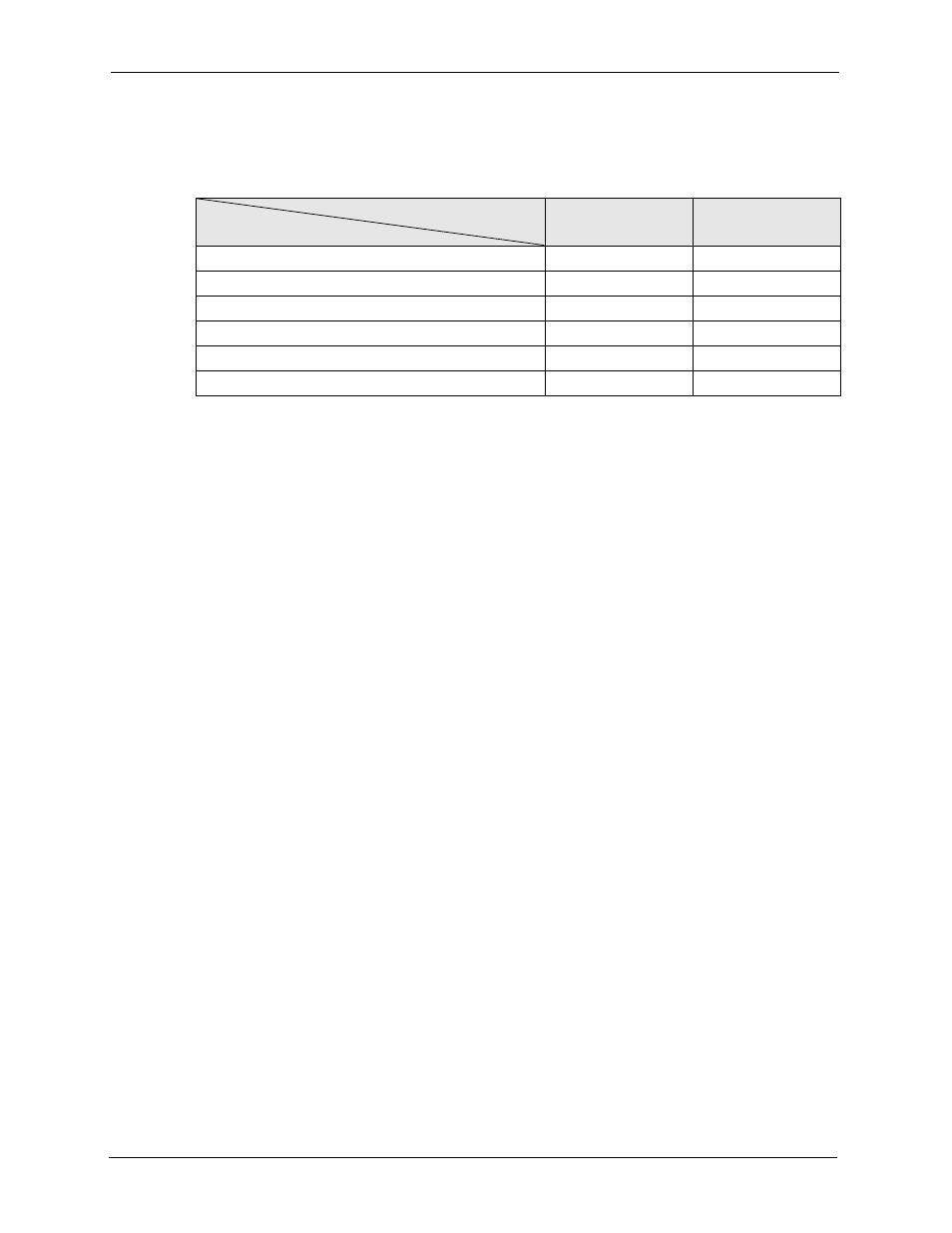
Table Key: An O in a mode’s column shows that the device mode has the specified feature.
The information in this table was correct at the time of writing, although it may be subject to
change.
High Speed Internet Access
Your Prestige ADSL/ADSL2/ADSL2+ router can support downstream transmission rates of
up to 24Mbps and upstream transmission rates of 3.5Mbps. Actual speeds attained depend on
the ADSL service you subscribed to, distance from your ISP, line quality, etc.
Zero Configuration Internet Access
Once you connect and turn on the Prestige, it automatically detects the Internet connection
settings (such as the VCI/VPI numbers and the encapsulation method) from the ISP and makes
the necessary configuration changes. In cases where additional account information (such as
an Internet account user name and password) is required or the Prestige cannot connect to the
ISP, you will be redirected to web screen(s) for information input or troubleshooting.
Any IP
The Any IP feature allows a computer to access the Internet and the Prestige without changing
the network settings (such as IP address and subnet mask) of the computer, when the IP
addresses of the computer and the Prestige are not in the same subnet.
Firewall
The Prestige is a stateful inspection firewall with DoS (Denial of Service) protection. By
default, when the firewall is activated, all incoming traffic from the WAN to the LAN is
blocked unless it is initiated from the LAN. The Prestige firewall supports TCP/UDP
inspection, DoS detection and prevention, real time alerts, reports and logs.
Table 2 Model Specific Features
MODEL
FEATURE
P-660R-D
P660H-D
Integrated 4-port Switch
O
Firewall
O
Meida Bandwidth Management
O
Content Filtering
O
Internet Security Filtering
O
Centralized Logs
O
