Example 5.7. access control summary logging, Audit log reference – Red Hat 8.1 User Manual
Page 172
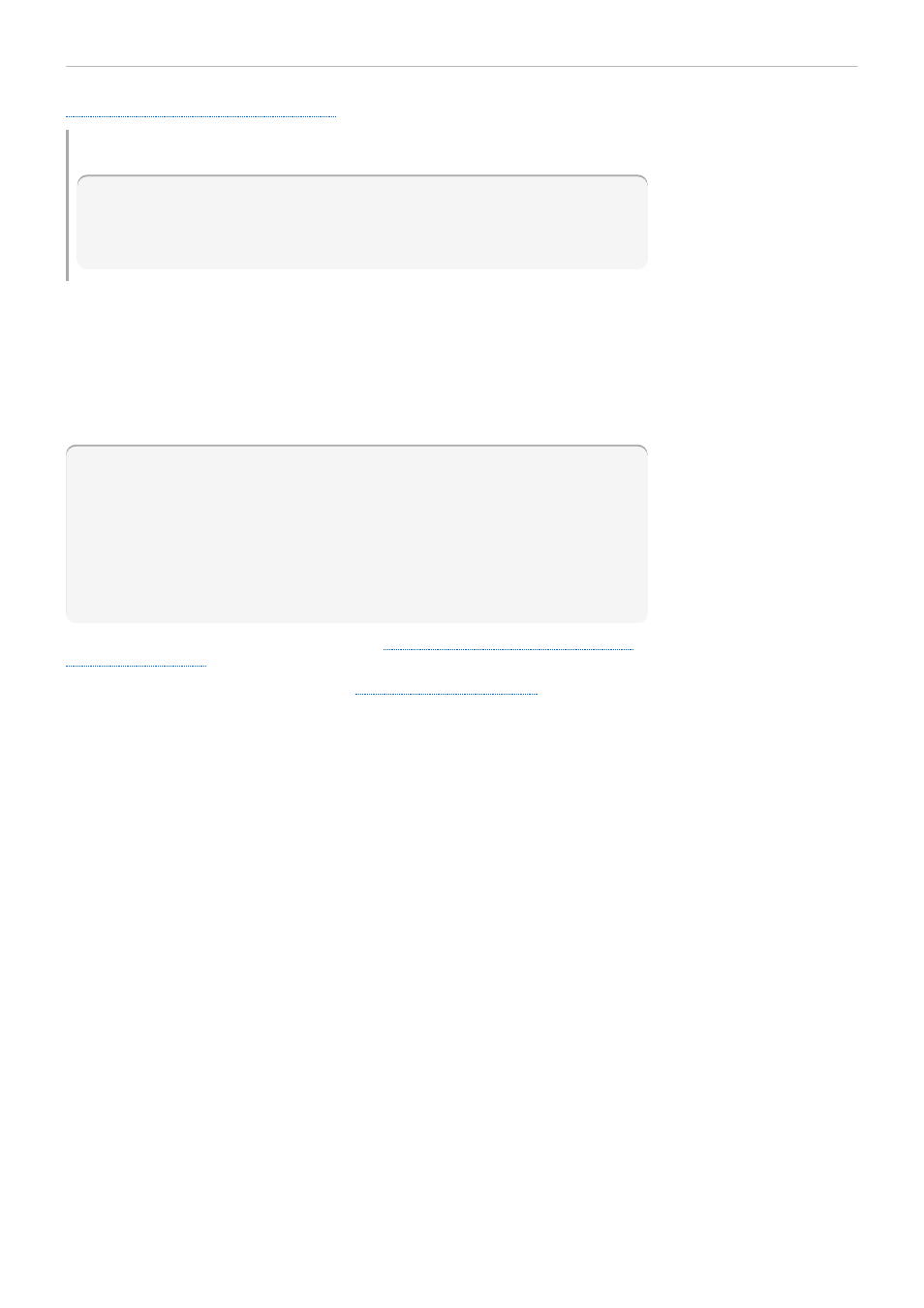
Example 5.7, “Access Control Summary Logging”
shows the summary access control log entry.
Example 5.7. Access Control Summary Logging
[09/Jan/2009:16:02:01 -0500] NSACLPlugin - #### conn=24826547353419844 op=1
binddn="uid=scarter,ou=people,dc=example,dc=com"
[09/Jan/2009:16:02:01 -0500] NSACLPlugin - conn=24826547353419844 op=1 (main):
Allow search on entry(ou=people,dc=example,dc=com).attr(uid) to
uid=scarter,ou=people,dc=example,dc=com: allowed by aci(2): aciname= "Enable
anonymous access", acidn="dc=example,dc=com"
5.3. Audit Log Reference
The audit log records changes made to the server instance. Unlike the error and access log, the audit
log does not record access to the server instance, so searches against the database are not logged.
The audit log is formatted differently than the access and error logs and is basically like a time-stamped
LDIF file. The operations recorded in the audit log are formatted as LDIF statements:
timestamp: date
dn: modified_entry
changetype: action
action:attribute
attribute:new_value
-
replace: modifiersname
modifiersname: dn
-
replace: modifytimestamp
modifytimestamp: date
-
LDIF files and formats are described in more detail in the
"LDAP Data Interchange Format" appendix of
the Administrator's Guide
.
Several different kinds of audit entries are shown in
Example 5.8, “Audit Log Content”
.
172
Chapter 5. Log File Reference
