Appendix j: ipsec nat traversal, Overview, Before you begin – Cisco 4-Port SSL/IPSec VPN Router RVL200 User Manual
Page 95: Configuration of scenario 1, Configuration of router a, Appendix j, Ipsec nat traversal
8
IPSec NAT Traversal
4-Port SSL/IPSec VPN Router
Appendix J
Appendix J:
IPSec NAT Traversal
Overview
Network Address Translation (NAT) traversal is a technique
developed so that data protected by IPSec can pass
through a NAT. (See NAT 1 and NAT 2 in the diagram.)
Since IPSec provides integrity for the entire IP datagram,
any changes to the IP addressing will invalidate the data.
To resolve this issue, NAT traversal appends a new IP and
UDP header to the incoming datagram, ensuring that no
changes are made to the incoming datagram stream.
This chapter discusses two scenarios. In the first scenario,
traffic is sent in one direction, through Router A, NAT 1,
NAT 2, and Router B. In the second scenario, traffic is sent
in the opposite direction, and a one-to-one NAT rule is
required.
Before You Begin
The following is a list of equipment you need:
Two 4-Port SSL/IPSec VPN Routers (model number:
RVL200), one of which is connected to the Internet
Two 10/100 4-Port VPN Routers (model number:
RV042), one of which is connected to the Internet
•
•
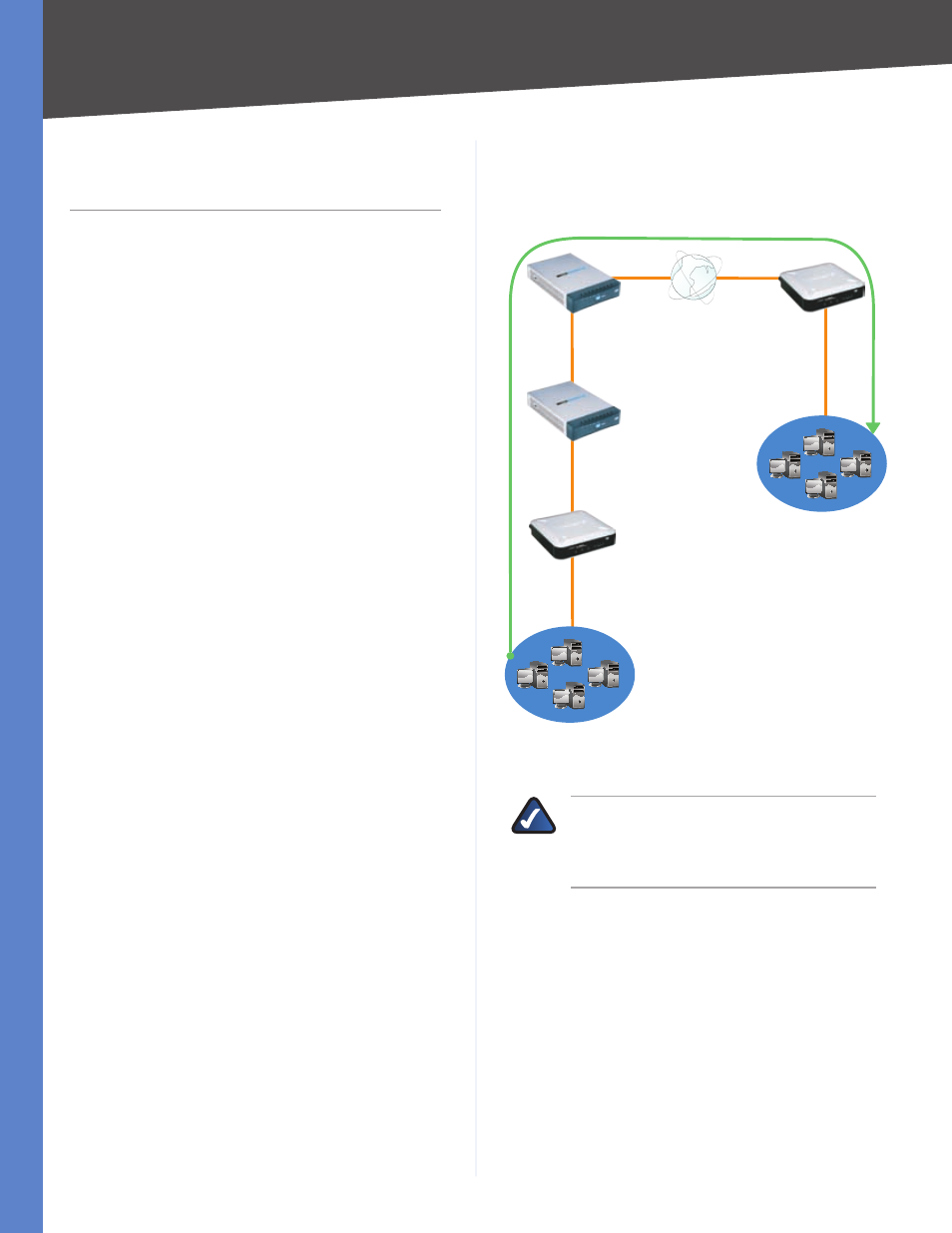
Configuration of Scenario 1
In this scenario, Router A is the RVL200 Initiator, while
Router B is the RVL200 Responder.
192.168.2.100
192.168.1.101
WAN: 192.168.99.22
Router B - RVL200
Responder
LAN: 192.168.2.0/24
WAN: 192.168.99.11
NAT 2 - RV042
LAN: 192.168.111.1
WAN: 192.168.111.101
NAT 1 - RV042
LAN: 192.168.11.1
WAN: 192.168.11.101
Router A - RVL200 Initiator
LAN: 192.168.1.0/24
Traffic in Scenario 1
NOTE:
Both the IPSec initiator and responder
must support the mechanism for detecting the
NAT router in the path and changing to a new
port, as defined in RFC 3947.
Configuration of Router A
Follow these instructions for Router A.
Launch the web browser for a networked computer,
designated PC 1.
Access the web-based utility of Router A. (Refer to
“Chapter 4: Advanced Configuration” for details.)
Click the IPSec VPN tab.
Click the Gateway to Gateway tab.
Enter a name in the Tunnel Name field.
For the VPN Tunnel setting, select Enable.
1.
2.
3.
4.
5.
6.
