Protecting components – Rockwell Automation Logix5000 Controllers Security Programming Manual User Manual
Page 34
Chapter 4 Configuring source protection in the Logix Designer application
Protecting components
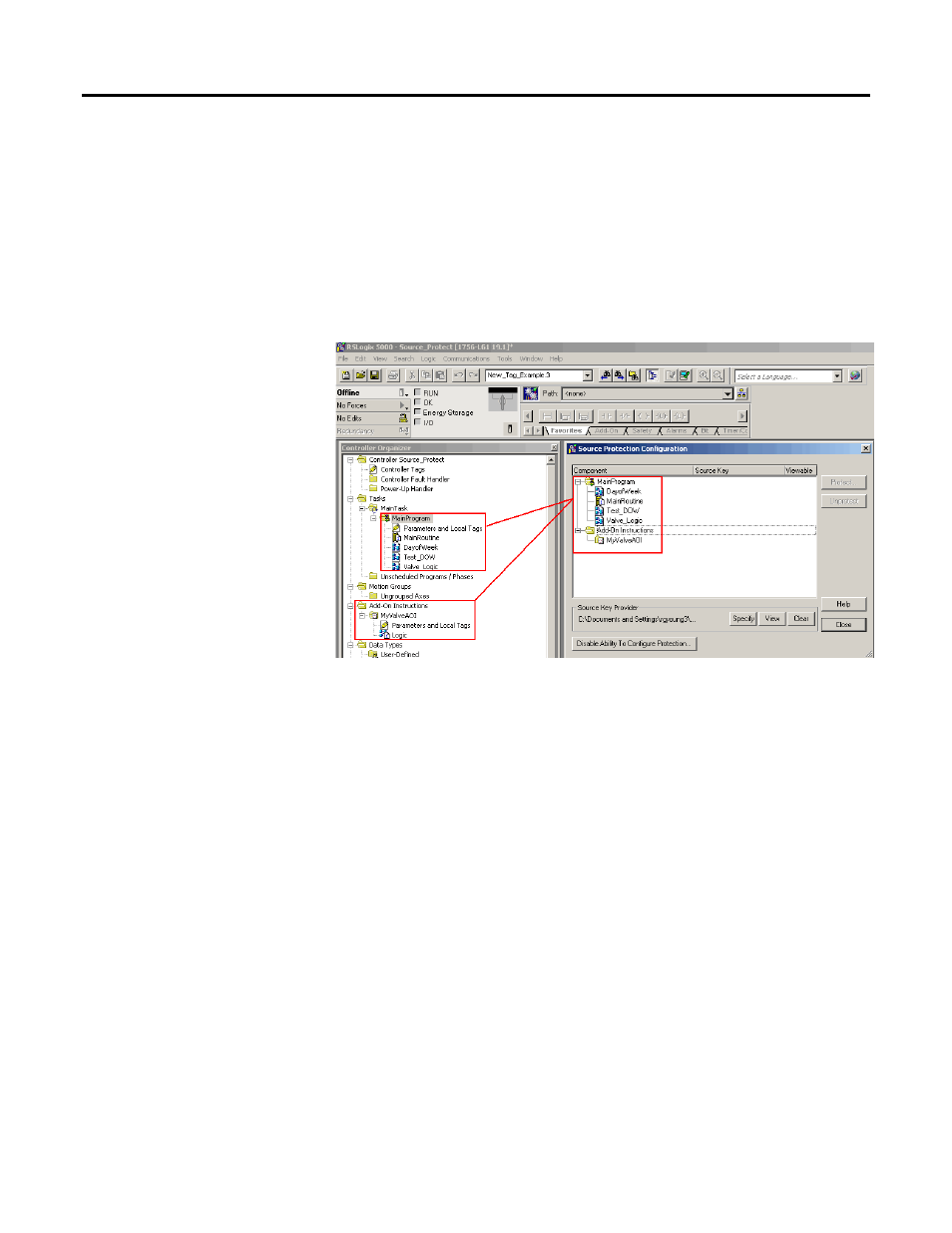
The Source Protection Configuration dialog box lists all Program Routines,
Add-On Instructions, and Equipment Phase State Routines in the project file.
You protect these components by applying source keys. Source keys are
user-generated passwords used to lock components. Users that do not have the
source key for a component are not able to modify the component and may not be
able to view the component.
About source keys
In version 18 and earlier of RSLogix 5000 software, only IEC-61131 compliant
source keys are recognized. Each source key must begin with a lowercase character
a-z or underscore character ( _ ), and contain only characters lowercase a-z, 0-9,
and an underscore character ( _ ). You can enter uppercase A-Z characters in
RSLogix 5000 software or in the source key file, but the uppercase characters are
converted to lowercase. Source keys are limited to 40 characters in length.
In version 19 and later of the application, source keys are case-sensitive and may
contain any printable ASCII character, excluding the space character. This
includes uppercase A-Z, lowercase a-z, numbers 0-9, and symbols such as "!@#$%.
Source keys are limited to 40 characters in length.
Source key names
Version 19 and later of the application supports associating names with source
keys. Source key names are descriptive text that help identify source keys. Where
appropriate, Logix Designer application will display the source key name in place
of the source key itself. This provides an additional layer of security for the source
key.
34
Rockwell Automation Publication 1756-PM016G-EN-P - October 2014
