4 binary, Protocol, Command structure – INFICON Helium Leak Detector Modul1000 Interface description User Manual
Page 16: Examples 1-14, 4binary protocol, 1 command structure, 2 examples
1-14
Binary Protocol
jin
s
80
e.f
m
Op
er
at
in
g M
a
nua
l
(1
01
1)
4
Binary Protocol
4.1
Command Structure
In binary protocol the command to the leak detector always starts with STX (0x05).
It is followed by a byte which indicates the length of the telegram (inclusive Start-Byte
and checksum). The next byte is the command number. The command byte may be
followed by additional information (parameter and/or data). Please refer to
"Command list" (chapter 4.5) for detailed information about command number,
parameter and data format.
Every telegram ends with a checksum. The checksum is the sum of all bytes before
the checksum byte modulo 256 (decimal).
The leak detector replies to every valid command with an acknowledgement. This
answer starts with the length byte followed by the command number, additional data
(optional) and the checksum.
In case of an error, the leak detector answers with an error byte instead of the
command number (refer to "Error Messages" in chapter 4.4).
Timeout to receive data between 2 sign is: 1000 ms.
4.2
Examples
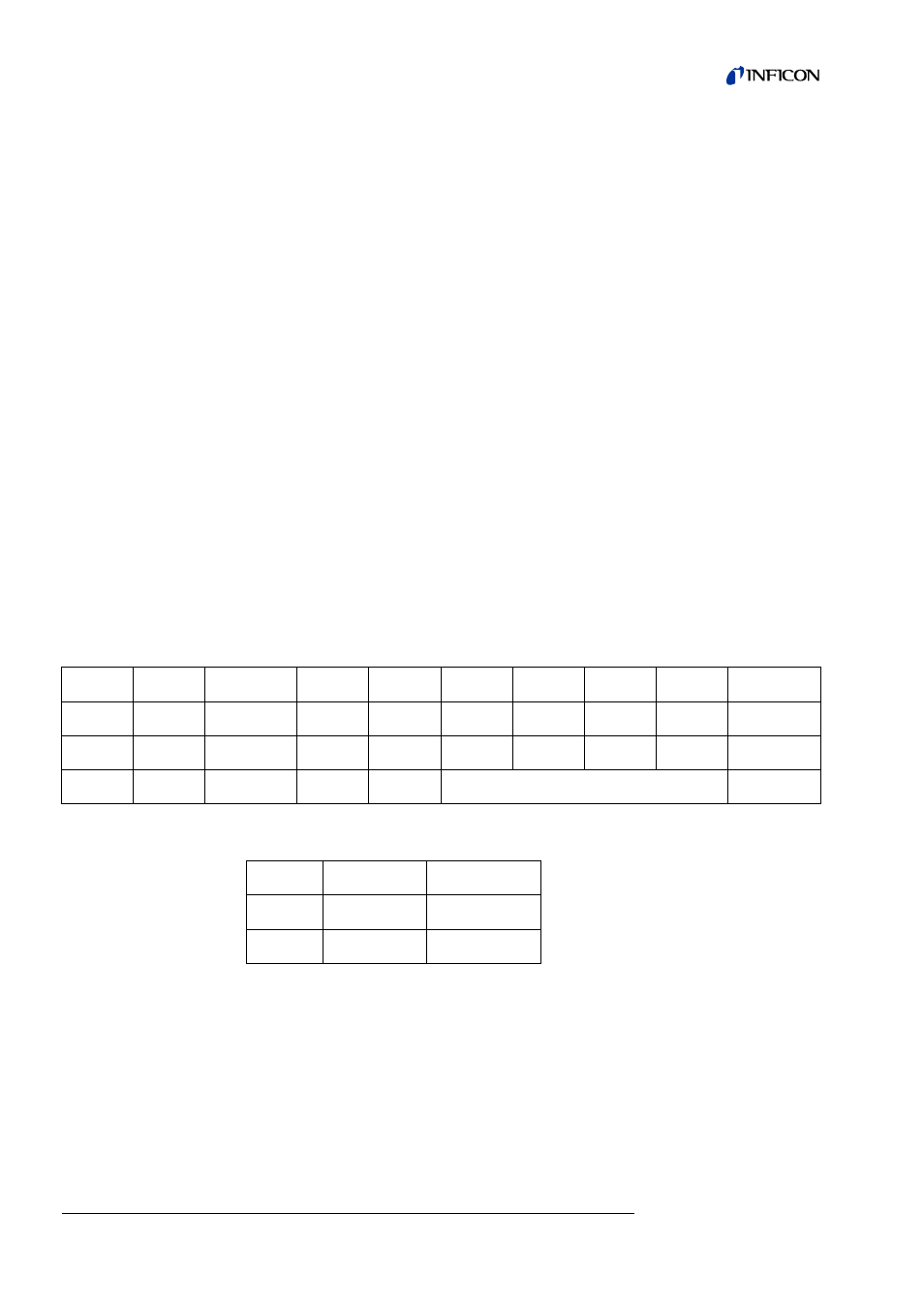
Example 1: Set trigger level 2 to 1.2E-7mbarl/s
PC
Î Leak detector
Leak detector
Î PC
5
10
57
2
0
52
0
217
89
176
0x05
0x0A
0x39
0x02
0x00
0x34
0x00
0xD9
0x59
0xB0
Start
Length
Command Para0
Para1
Data
Data
Data
Data
Checksum
Trigger
Trig. 2
mbarl/s
1.2E-7 (4-Byte float)
3
57
60
0x03
0x39
0x3C
Length Command Checksum
