Zigbee security – SENA ProBee-ZS10 User Manual
Page 29
29
ProBee-ZS10 User Guide Rev.1.5
Poll Request
Data Exchange
Parent Node
Sleepy End-Device
Sleep
Wake-Up
Sleep
S53
S52
S54
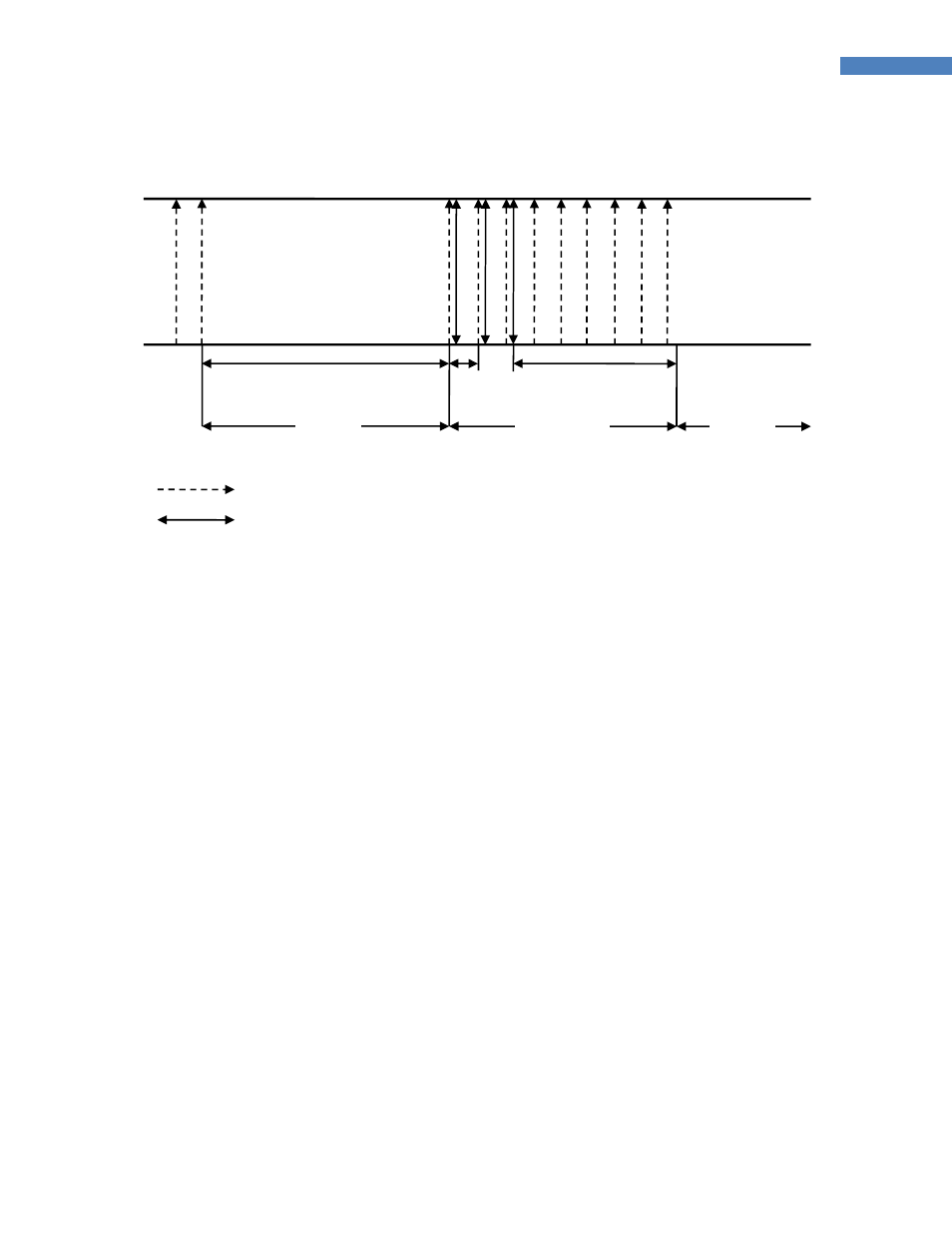
Figure 3-1 Sleep Interval and Wake-up Timing
The sleepy end-device can also wake up from the sleep mode by function button interrupt or incoming
serial data. Once it wakes up, it also polls with the parent node at S52 interval and goes into sleep mode
after S54 time elapses after the last data exchange.
Note: If the sleepy end-device wakes up by incoming serial data, the integrity of the first incoming byte is
not guaranteed. It is strongly recommended to wake up the sleepy end-device by using function button
first before sending the serial data or use higher level serial data protocol to check the data integrity.
3.5 ZigBee
Security
Security is a major concern in the ZigBee architecture. Although ZigBee uses the basic security elements
in IEEE 802.15.4 (e.g., AES encryption & CCM security modes), the ZS10 increases the security level
with:
• 128 bit AES encryption algorithms
• Strong, NIST-approved security
• Defined Key Types (Link, Network)
• Defined Key setup and maintenance
• CCM (Unified/Simpler mode of operation)
• Trust
Centers
