Enterasys Networks 802.11 User Manual
Page 52
Security
2-18
4.
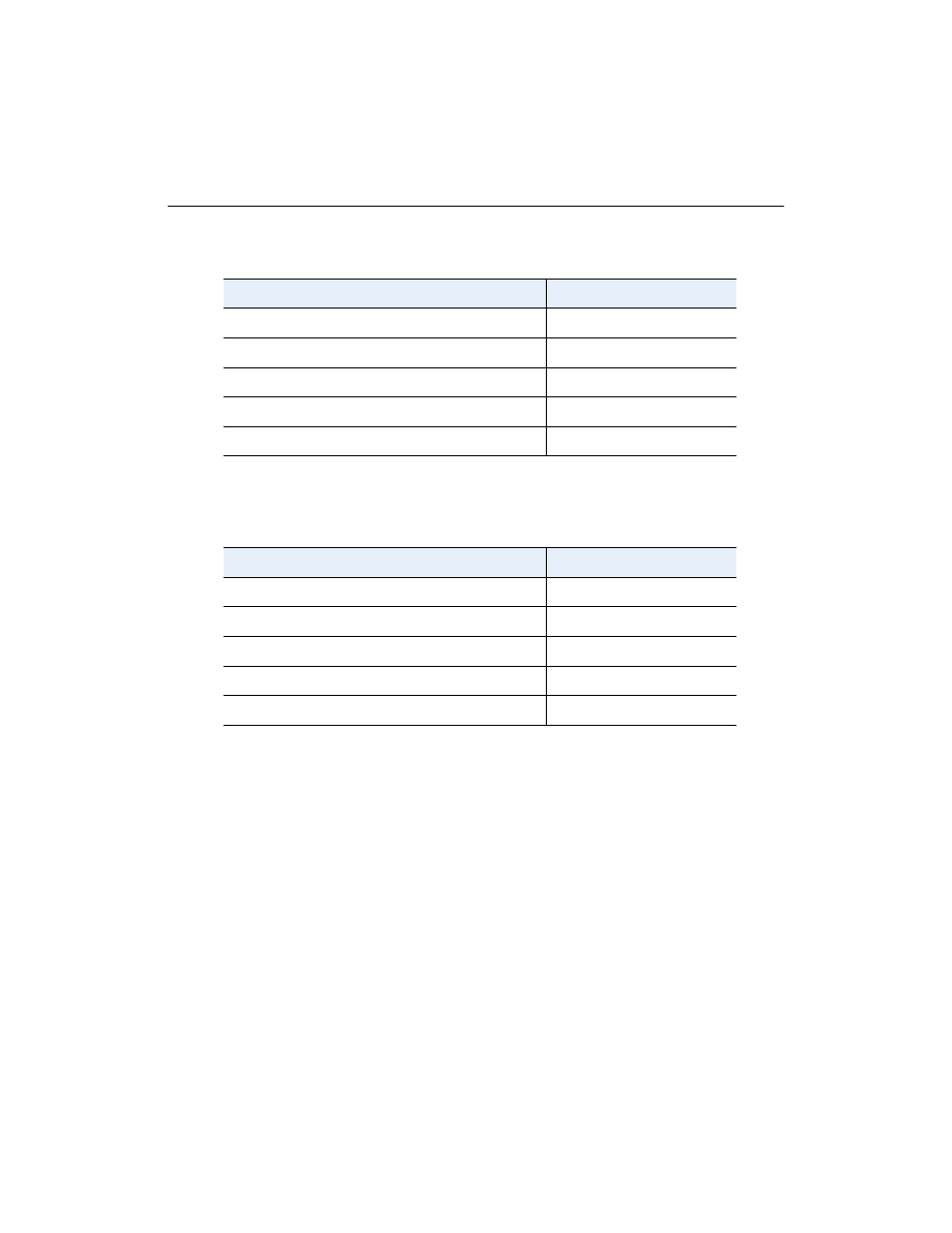
Once the AP transmits the new keys to all clients in the supplicant list, it begins using
the new TX key (Key4). At this time all supplicants are using Key3 as their TX key.
5.
The key period expires. The AP creates two new random keys, loads them into the
inactive authenticator key indexes (Keys 1 and 2 in this example), and repeats the
process (starting at step 3).
AP
Client
Key #
Encryption
TX/RX
State
TX/RX
Encryption
Key1
aaaaaaaaaaaaaa Inactive
aaaaaaaaaaaaaa
Key2 bbbbbbbbbbbbb
Inactive
bbbbbbbbbbbbb
Key3 cccccccccccccc
RX
Active
TX
cccccccccccccc
Key4
ddddddddddddd
TX
Active
RX
ddddddddddddd
AP
Client
Key #
Encryption
TX/RX
State
TX/RX
Encryption
Key1
eeeeeeeeeeeee Inactive
aaaaaaaaaaaaaa
Key2
fffffffffffff
Inactive
bbbbbbbbbbbbb
Key3 cccccccccccccc
RX
Active
TX
cccccccccccccc
Key4
ddddddddddddd
TX
Active
RX
ddddddddddddd
